[ad_1] Apr 09, 2025Ravie LakshmananApplication Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a critical security flaw impacting Gladinet CentreStack to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. The vulnerability, tracked as CVE-2025-30406 (CVSS score: 9.0), concerns a case of a hard-coded…
Author: admin
New TCESB Malware Found in Active Attacks Exploiting ESET Security Scanner
[ad_1] Apr 09, 2025Ravie LakshmananWindows Security / Vulnerability A Chinese-affiliated threat actor known for its cyber-attacks in Asia has been observed exploiting a security flaw in security software from ESET to deliver a previously undocumented malware codenamed TCESB. “Previously unseen in ToddyCat attacks, [TCESB] is designed to stealthily execute payloads in circumvention of protection and…
Explosive Growth of Non-Human Identities Creating Massive Security Blind Spots
[ad_1] Apr 09, 2025The Hacker NewsSecrets Management / DevOps GitGuardian’s State of Secrets Sprawl report for 2025 reveals the alarming scale of secrets exposure in modern software environments. Driving this is the rapid growth of non-human identities (NHIs), which have been outnumbering human users for years. We need to get ahead of it and prepare…
PipeMagic Trojan Exploits Windows Zero-Day Vulnerability to Deploy Ransomware
[ad_1] Apr 09, 2025Ravie LakshmananVulnerability / Ransomware Microsoft has revealed that a now-patched security flaw impacting the Windows Common Log File System (CLFS) was exploited as a zero-day in ransomware attacks aimed at a small number of targets. “The targets include organizations in the information technology (IT) and real estate sectors of the United States,…
Microsoft Patches 126 Flaws Including Actively Exploited Windows CLFS Vulnerability
[ad_1] Apr 09, 2025Ravie LakshmananEndpoint Security / Vulnerability Microsoft has released security fixes to address a massive set of 126 flaws affecting its software products, including one vulnerability that it said has been actively exploited in the wild. Of the 126 vulnerabilities, 11 are rated Critical, 112 are rated Important, and two are rated Low…
Adobe Patches 11 Critical ColdFusion Flaws Amid 30 Total Vulnerabilities Discovered
[ad_1] Apr 09, 2025Ravie LakshmananSoftware Security / Vulnerability Adobe has released security updates to fix a fresh set of security flaws, including multiple critical-severity bugs in ColdFusion versions 2025, 2023 and 2021 that could result in arbitrary file read and code execution. Of the 30 flaws in the product, 11 are rated Critical in severity –…
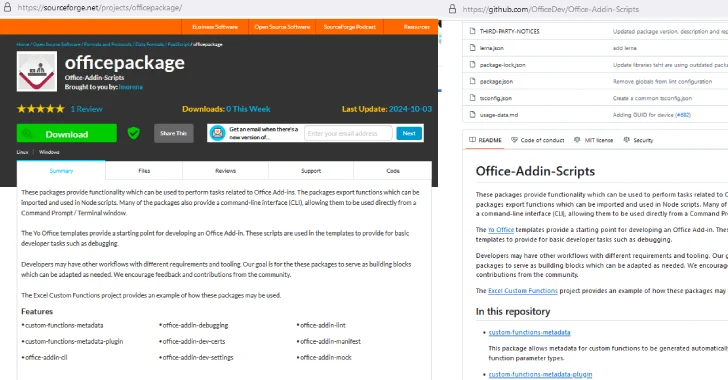
Cryptocurrency Miner and Clipper Malware Spread via SourceForge Cracked Software Listings
[ad_1] Threat actors have been observed distributing malicious payloads such as cryptocurrency miner and clipper malware via SourceForge, a popular software hosting service, under the guise of cracked versions of legitimate applications like Microsoft Office. “One such project, officepackage, on the main website sourceforge.net, appears harmless enough, containing Microsoft Office add-ins copied from a legitimate…
Fortinet Urges FortiSwitch Upgrades to Patch Critical Admin Password Change Flaw
[ad_1] Apr 08, 2025Ravie LakshmananNetwork Security / Vulnerability Fortinet has released security updates to address a critical security flaw impacting FortiSwitch that could permit an attacker to make unauthorized password changes. The vulnerability, tracked as CVE-2024-48887, carries a CVSS score of 9.3 out of a maximum of 10.0. “An unverified password change vulnerability [CWE-620] in…
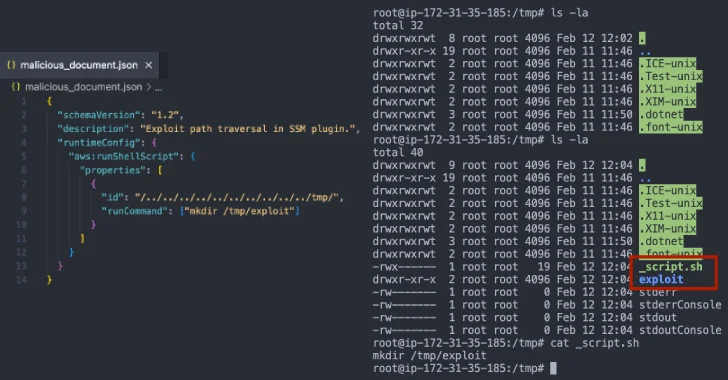
Amazon EC2 SSM Agent Flaw Patched After Privilege Escalation via Path Traversal
[ad_1] Apr 08, 2025Ravie LakshmananCloud Security / Vulnerability Cybersecurity researchers have disclosed details of a now-patched security flaw in the Amazon EC2 Simple Systems Manager (SSM) Agent that, if successfully exploited, could permit an attacker to achieve privilege escalation and code execution. The vulnerability could permit an attacker to create directories in unintended locations on…
UAC-0226 Deploys GIFTEDCROOK Stealer via Malicious Excel Files Targeting Ukraine
[ad_1] The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed a new set of cyber attacks targeting Ukrainian institutions with information-stealing malware. The activity is aimed at military formations, law enforcement agencies, and local self-government bodies, particularly those located near Ukraine’s eastern border, the agency said. The attacks involve distributing phishing emails containing a…