[ad_1] Oct 27, 2023NewsroomNetwork Security / Vulnerability F5 has alerted customers of a critical security vulnerability impacting BIG-IP that could result in unauthenticated remote code execution. The issue, rooted in the configuration utility component, has been assigned the CVE identifier CVE-2023-46747, and carries a CVSS score of 9.8 out of a maximum of 10. “This…
Author: admin
Researchers Warn of Kazakhstan’s Stealthy Cyber Espionage Group
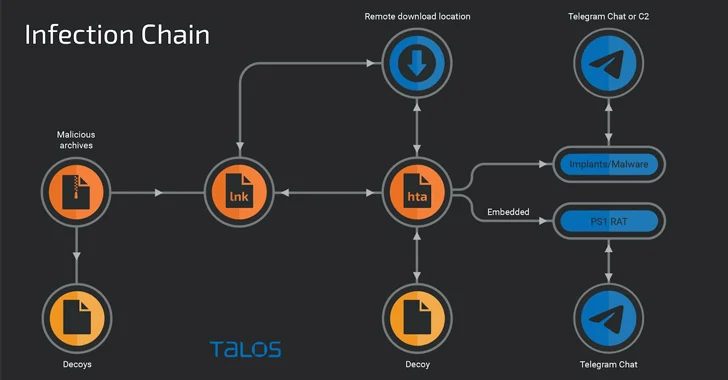
[ad_1] Oct 26, 2023NewsroomEndpoint Protection / Malware A relatively new threat actor known as YoroTrooper is likely made up of operators originating from Kazakhstan. The assessment, which comes from Cisco Talos, is based on their fluency in Kazakh and Russian, use of Tenge to pay for operating infrastructure, and very limited targeting of Kazakhstani entities,…
Critical Flaw in NextGen’s Mirth Connect Could Expose Healthcare Data
[ad_1] Oct 26, 2023NewsroomVulnerability / Network Security Users of Mirth Connect, an open-source data integration platform from NextGen HealthCare, are being urged to update to the latest version following the discovery of an unauthenticated remote code execution vulnerability. Tracked as CVE-2023-43208, the vulnerability has been addressed in version 4.4.1 released on October 6, 2023. “This…
Iranian Group Tortoiseshell Launches New Wave of IMAPLoader Malware Attacks
[ad_1] Oct 26, 2023NewsroomCyber Threat / Malware The Iranian threat actor known as Tortoiseshell has been attributed to a new wave of watering hole attacks that are designed to deploy a malware dubbed IMAPLoader. “IMAPLoader is a .NET malware that has the ability to fingerprint victim systems using native Windows utilities and acts as a…
Record-Breaking 100 Million RPS DDoS Attack Exploits HTTP/2 Rapid Reset Flaw
[ad_1] Oct 26, 2023NewsroomNetwork Security / Cyber Attack Cloudflare on Thursday said it mitigated thousands of hyper-volumetric HTTP distributed denial-of-service (DDoS) attacks that exploited a recently disclosed flaw called HTTP/2 Rapid Reset, 89 of which exceeded 100 million requests per second (RPS). “The campaign contributed to an overall increase of 65% in HTTP DDoS attack…
Microsoft Warns as Scattered Spider Expands from SIM Swaps to Ransomware
[ad_1] Oct 26, 2023NewsroomCyber Threat / Social Engineering The prolific threat actor known as Scattered Spider has been observed impersonating newly hired employees in targeted firms as a ploy to blend into normal on-hire processes and takeover accounts and breach organizations across the world. Microsoft, which disclosed the activities of the financially motivated hacking crew,…
New Safari Exploit Impacts Apple iPhones and Macs with A and M-Series CPUs
[ad_1] Oct 26, 2023NewsroomData Security / Vulnerability A group of academics has devised a novel side-channel attack dubbed iLeakage that exploits a weakness in the A- and M-series CPUs running on Apple iOS, iPadOS, and macOS devices, enabling the extraction of sensitive information from the Safari web browser. “An attacker can induce Safari to render…
The Danger of Forgotten Pixels on Websites: A New Case Study
[ad_1] Oct 26, 2023The Hacker NewsWeb Security / Data Protection While cyberattacks on websites receive much attention, there are often unaddressed risks that can lead to businesses facing lawsuits and privacy violations even in the absence of hacking incidents. A new case study highlights one of these more common cases. Download the full case study…
Quasar RAT Leverages DLL Side-Loading to Fly Under the Radar
[ad_1] Oct 23, 2023NewsroomCyberattack / Malware The open-source remote access trojan known as Quasar RAT has been observed leveraging DLL side-loading to fly under the radar and stealthily siphon data from compromised Windows hosts. “This technique capitalizes on the inherent trust these files command within the Windows environment,” Uptycs researchers Tejaswini Sandapolla and Karthickkumar Kathiresan…
1Password Detects Suspicious Activity Following Okta Support Breach
[ad_1] Oct 24, 2023NewsroomCyber Attack / Password Management Popular password management solution 1Password said it detected suspicious activity on its Okta instance on September 29 following the support system breach, but reiterated that no user data was accessed. “We immediately terminated the activity, investigated, and found no compromise of user data or other sensitive systems,…