[ad_1] Apr 01, 2025Ravie LakshmananMobile Security / Vulnerability Apple on Monday backported fixes for three vulnerabilities that have come under active exploitation in the wild to older models and previous versions of the operating systems. The vulnerabilities in question are listed below – CVE-2025-24085 (CVSS score: 7.3) – A use-after-free bug in the Core Media…
Category: Cyber News
Lucid PhaaS Hits 169 Targets in 88 Countries Using iMessage and RCS Smishing
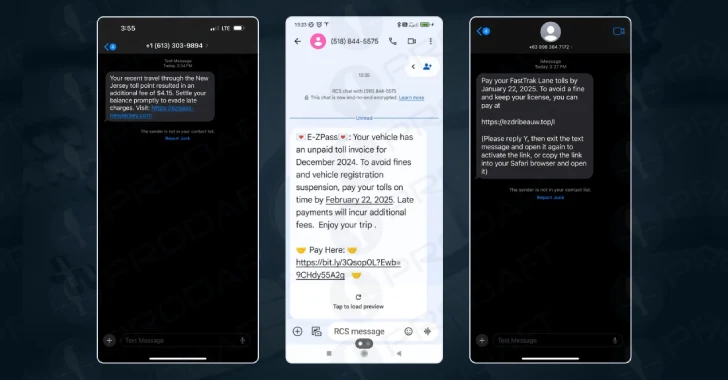
[ad_1] A new sophisticated phishing-as-a-service (PhaaS) platform called Lucid has targeted 169 entities in 88 countries using smishing messages propagated via Apple iMessage and Rich Communication Services (RCS) for Android. Lucid’s unique selling point lies in its weaponizing of legitimate communication platforms to sidestep traditional SMS-based detection mechanisms. “Its scalable, subscription-based model enables cybercriminals to…
Enterprise Gmail Users Can Now Send End-to-End Encrypted Emails to Any Platform
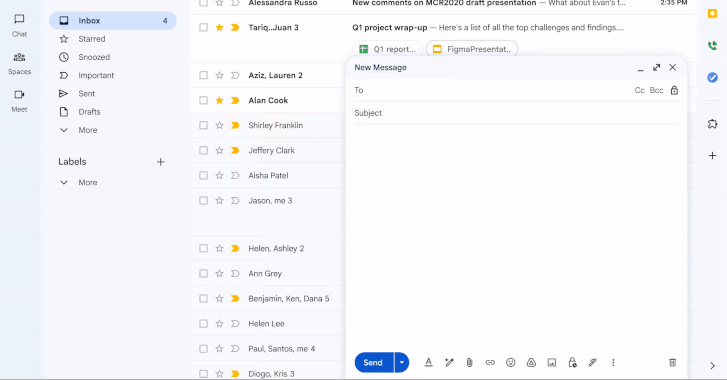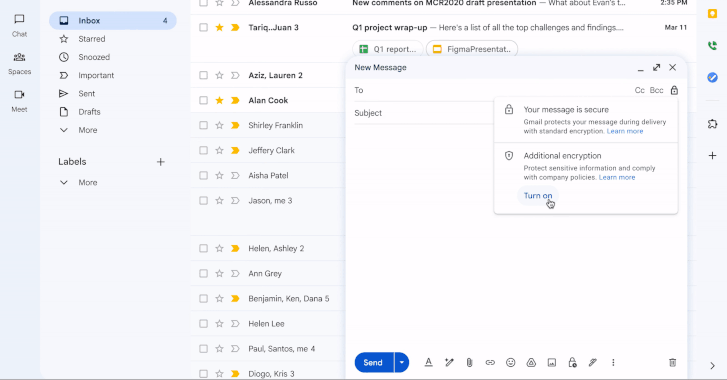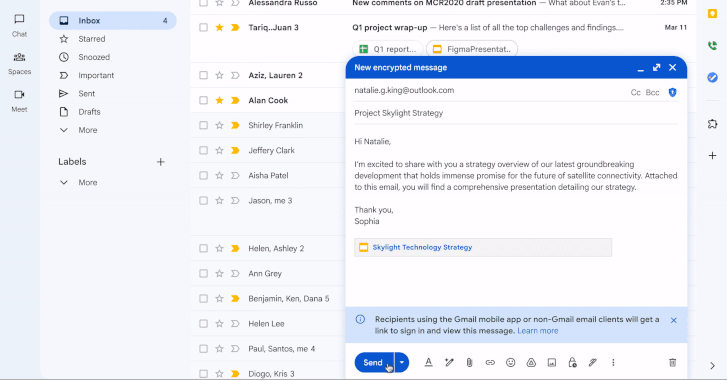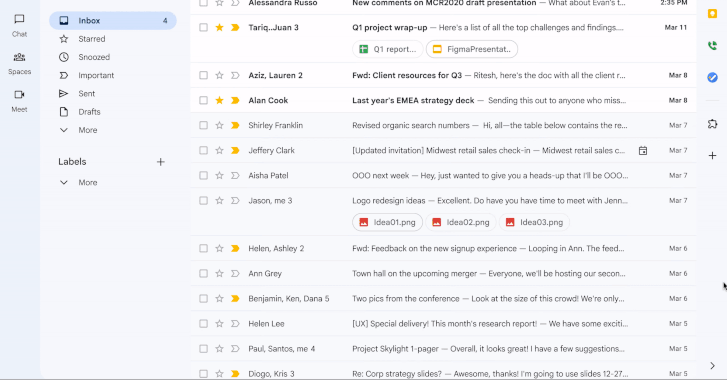
[ad_1] Apr 01, 2025Ravie LakshmananEncryption / Email Security On the 21st birthday of Gmail, Google has announced a major update that allows enterprise users to send end-to-end encrypted (E2EE) to any user in any email inbox in a few clicks. The feature is rolling out starting today in beta, allowing users to send E2EE emails…
New Malware Loaders Use Call Stack Spoofing, GitHub C2, and .NET Reactor for Stealth
[ad_1] Apr 02, 2025Ravie LakshmananThreat Detection / Malware Cybersecurity researchers have discovered an updated version of a malware loader called Hijack Loader that implements new features to evade detection and establish persistence on compromised systems. “Hijack Loader released a new module that implements call stack spoofing to hide the origin of function calls (e.g., API…
How SSL Misconfigurations Impact Your Attack Surface
[ad_1] Apr 02, 2025The Hacker NewsWeb Security / Attack Surface When assessing an organization’s external attack surface, encryption-related issues (especially SSL misconfigurations) receive special attention. Why? Their widespread use, configuration complexity, and visibility to attackers as well as users make them more likely to be exploited. This highlights how important your SSL configurations are in…
Europol Dismantles Kidflix With 72,000 CSAM Videos Seized in Major Operation
[ad_1] In one of the largest coordinated law enforcement operations, authorities have dismantled Kidflix, a streaming platform that offered child sexual abuse material (CSAM). “A total of 1.8 million users worldwide logged on to the platform between April 2022 and March 2025,” Europol said in a statement. “On March 11, 2025, the server, which contained…
Legacy Stripe API Exploited to Validate Stolen Payment Cards in Web Skimmer Campaign
[ad_1] Apr 03, 2025Ravie LakshmananCybersecurity / Threat Intelligence Threat hunters are warning of a sophisticated web skimmer campaign that leverages a legacy application programming interface (API) from payment processor Stripe to validate stolen payment information prior to exfiltration. “This tactic ensures that only valid card data is sent to the attackers, making the operation more…
SpotBugs Access Token Theft Identified as Root Cause of GitHub Supply Chain Attack
[ad_1] Apr 04, 2025Ravie LakshmananVulnerability / Open Source, The cascading supply chain attack that initially targeted Coinbase before becoming more widespread to single out users of the “tj-actions/changed-files” GitHub Action has been traced further back to the theft of a personal access token (PAT) related to SpotBugs. “The attackers obtained initial access by taking advantage…
OPSEC Failure Exposes Coquettte’s Malware Campaigns on Bulletproof Hosting Servers
[ad_1] Apr 04, 2025Ravie LakshmananThreat Intelligence / Malware A novice cybercrime actor has been observed leveraging the services of a Russian bulletproof hosting (BPH) provider called Proton66 to facilitate their operations. The findings come from DomainTools, which detected the activity after it discovered a phony website named cybersecureprotect[.]com hosted on Proton66 that masqueraded as an…
Have We Reached a Distroless Tipping Point?
[ad_1] There’s a virtuous cycle in technology that pushes the boundaries of what’s being built and how it’s being used. A new technology development emerges and captures the world’s attention. People start experimenting and discover novel applications, use cases, and approaches to maximize the innovation’s potential. These use cases generate significant value, fueling demand for…