[ad_1] Nov 20, 2024Ravie LakshmananLinux / Vulnerability Multiple decade-old security vulnerabilities have been disclosed in the needrestart package installed by default in Ubuntu Server (since version 21.04) that could allow a local attacker to gain root privileges without requiring user interaction. The Qualys Threat Research Unit (TRU), which identified and reported the flaws early last…
Category: Cyber News
Hackers Exploiting NFCGate to Steal Funds via Mobile Payments
[ad_1] Nov 20, 2024Ravie LakshmananPayment Security / Cybercrime Threat actors are increasingly banking on a new technique that leverages near-field communication (NFC) to cash out victim’s funds at scale. The technique, codenamed Ghost Tap by ThreatFabric, enables cybercriminals to cash-out money from stolen credit cards linked to mobile payment services such as Google Pay or…
NHIs Are the Future of Cybersecurity: Meet NHIDR
[ad_1] Nov 20, 2024The Hacker NewsIdentity Security / Cyber Defense The frequency and sophistication of modern cyberattacks are surging, making it increasingly challenging for organizations to protect sensitive data and critical infrastructure. When attackers compromise a non-human identity (NHI), they can swiftly exploit it to move laterally across systems, identifying vulnerabilities and compromising additional NHIs…
Apple Releases Urgent Updates to Patch Actively Exploited Zero-Day Vulnerabilities
[ad_1] Nov 20, 2024Ravie LakshmananZero Day / Vulnerability Apple has released security updates for iOS, iPadOS, macOS, visionOS, and its Safari web browser to address two zero-day flaws that have come under active exploitation in the wild. The flaws are listed below – CVE-2024-44308 – A vulnerability in JavaScriptCore that could lead to arbitrary code…
Ngioweb Botnet Fuels NSOCKS Residential Proxy Network Exploiting IoT Devices
[ad_1] The malware known as Ngioweb has been used to fuel a notorious residential proxy service called NSOCKS, as well as by other services such as VN5Socks and Shopsocks5, new findings from Lumen Technologies reveal. “At least 80% of NSOCKS bots in our telemetry originate from the Ngioweb botnet, mainly utilizing small office/home office (SOHO)…
Why Privileged Access Security Must Be a Top Priority
[ad_1] Nov 19, 2024The Hacker NewsInsider Threat / Credential Security Privileged accounts are well-known gateways for potential security threats. However, many organizations focus solely on managing privileged access—rather than securing the accounts and users entrusted with it. This emphasis is perhaps due to the persistent challenges of Privileged Access Management (PAM) deployments. Yet, as the…
The Problem of Permissions and Non-Human Identities
[ad_1] According to research from GitGuardian and CyberArk, 79% of IT decision-makers reported having experienced a secrets leak, up from 75% in the previous year’s report. At the same time, the number of leaked credentials has never been higher, with over 12.7 million hardcoded credentials in public GitHub repositories alone. One of the more troubling…
New Stealthy BabbleLoader Malware Spotted Delivering WhiteSnake and Meduza Stealers
[ad_1] Nov 18, 2024Ravie LakshmananThreat Intelligence / Ransomware Cybersecurity researchers have shed light on a new stealthy malware loader called BabbleLoader that has been observed in the wild delivering information stealer families such as WhiteSnake and Meduza. BabbleLoader is an “extremely evasive loader, packed with defensive mechanisms, that is designed to bypass antivirus and sandbox…
THN Recap: Top Cybersecurity Threats, Tools, and Practices (Nov 11
[ad_1] Nov 18, 2024Ravie LakshmananCybersecurity / Infosec What do hijacked websites, fake job offers, and sneaky ransomware have in common? They’re proof that cybercriminals are finding smarter, sneakier ways to exploit both systems and people. This week makes one thing clear: no system, no person, no organization is truly off-limits. Attackers are getting smarter, faster,…
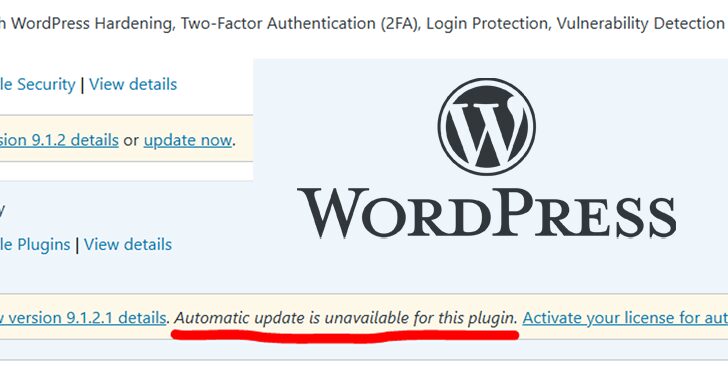
Critical WordPress Plugin Vulnerability Exposes Over 4 Million Sites
[ad_1] Nov 18, 2024Ravie LakshmananVulnerability / Website Security A critical authentication bypass vulnerability has been disclosed in the Really Simple Security (formerly Really Simple SSL) plugin for WordPress that, if successfully exploited, could grant an attacker to remotely gain full administrative access to a susceptible site. The vulnerability, tracked as CVE-2024-10924 (CVSS score: 9.8), impacts…