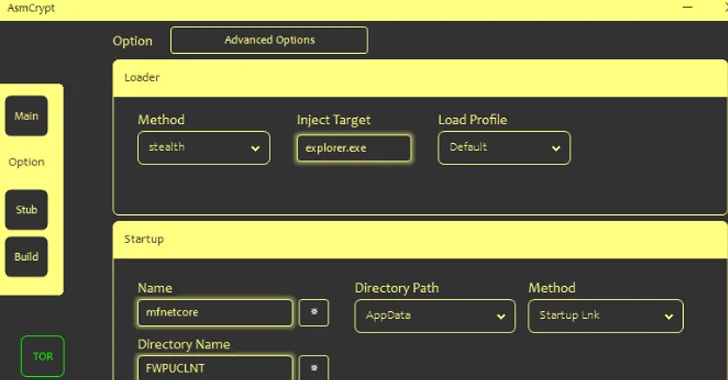
[ad_1] Threat actors are selling a new crypter and loader called ASMCrypt, which has been described as an “evolved version” of another loader malware known as DoubleFinger. “The idea behind this type of malware is to load the final payload without the loading process or the payload itself being detected by AV/EDR, etc.,” Kaspersky said…
Month: October 2023
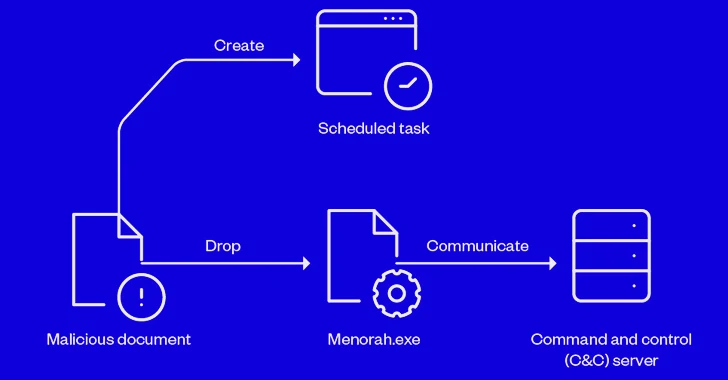
Iranian APT Group OilRig Using New Menorah Malware for Covert Operations
[ad_1] Sep 30, 2023NewsroomCyber Espionage / Malware Sophisticated cyber actors backed by Iran known as OilRig have been linked to a spear-phishing campaign that infects victims with a new strain of malware called Menorah. “The malware was designed for cyberespionage, capable of identifying the machine, reading and uploading files from the machine, and downloading another…
Zanubis Android Banking Trojan Poses as Peruvian Government App to Target Users
[ad_1] Oct 02, 2023NewsroomMalware / Cyber Threat An emerging Android banking trojan called Zanubis is now masquerading as a Peruvian government app to trick unsuspecting users into installing the malware. “Zanubis’s main infection path is through impersonating legitimate Peruvian Android applications and then tricking the user into enabling the Accessibility permissions in order to take…
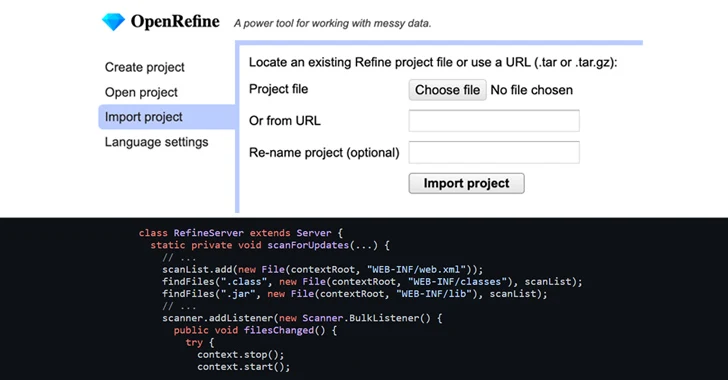
OpenRefine’s Zip Slip Vulnerability Could Let Attackers Execute Malicious Code
[ad_1] Oct 02, 2023NewsroomVulnerability / Cyber Attack A high-severity security flaw has been disclosed in the open-source OpenRefine data cleanup and transformation tool that could result in arbitrary code execution on affected systems. Tracked as CVE-2023-37476 (CVSS score: 7.8), the vulnerability is a Zip Slip vulnerability that could have adverse impacts when importing a specially…
A Year-Long Web Skimming Campaign Targeting Online Payment Businesses
[ad_1] Oct 02, 2023NewsroomWebb Security / Payment Security A financially motivated campaign has been targeting online payment businesses in the Asia Pacific, North America, and Latin America with web skimmers for more than a year. The BlackBerry Research and Intelligence Team is tracking the activity under the name Silent Skimmer, attributing it to an actor…
Unveiling the Silent Killer of Cyber Security Risk Across Industries
[ad_1] Introduction In today’s interconnected digital ecosystem, Application Programming Interfaces (APIs) play a pivotal role in enabling seamless communication and data exchange between various software applications and systems. APIs act as bridges, facilitating the sharing of information and functionalities. However, as the use of APIs continues to rise, they have become an increasingly attractive target…
Scattered Spider Getting SaaS-y in the Cloud
[ad_1] LUCR-3 overlaps with groups such as Scattered Spider, Oktapus, UNC3944, and STORM-0875 and is a financially motivated attacker that leverages the Identity Provider (IDP) as initial access into an environment with the goal of stealing Intellectual Property (IP) for extortion. LUCR-3 targets Fortune 2000 companies across various sectors, including but not limited to Software,…
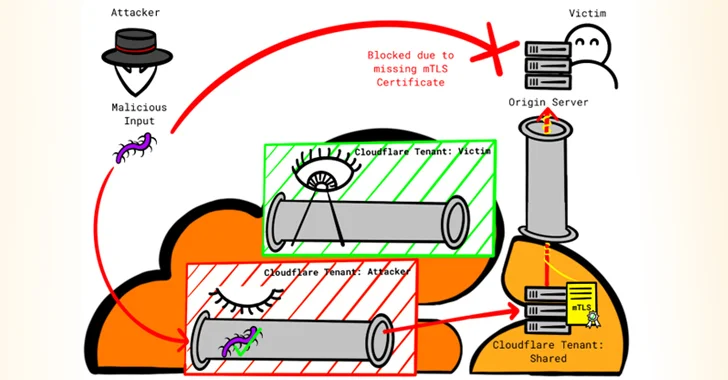
Researcher Reveals New Techniques to Bypass Cloudflare’s Firewall and DDoS Protection
[ad_1] Firewall and distributed denial-of-service (DDoS) attack prevention mechanisms in Cloudflare can be circumvented by exploiting gaps in cross-tenant security controls, defeating the very purpose of these safeguards, it has emerged. “Attackers can utilize their own Cloudflare accounts to abuse the per-design trust-relationship between Cloudflare and the customers’ websites, rendering the protection mechanism ineffective,” Certitude…
Protecting your IT infrastructure with Security Configuration Assessment (SCA)
[ad_1] Oct 03, 2023The Hacker NewsNetwork Security / XDR / SIEM Security Configuration Assessment (SCA) is critical to an organization’s cybersecurity strategy. SCA aims to discover vulnerabilities and misconfigurations that malicious actors exploit to gain unauthorized access to systems and data. Regular security configuration assessments are essential in maintaining a secure and compliant environment, as…
API Security Trends 2023 – Have Organizations Improved their Security Posture?
[ad_1] Oct 03, 2023The Hacker NewsAPI Security / Data Security APIs, also known as application programming interfaces, serve as the backbone of modern software applications, enabling seamless communication and data exchange between different systems and platforms. They provide developers with an interface to interact with external services, allowing them to integrate various functionalities into their…