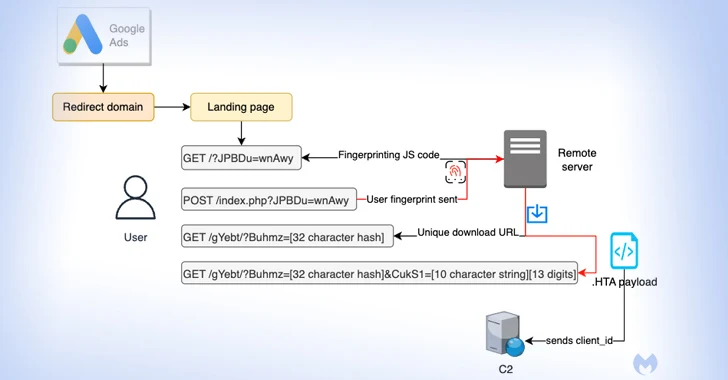
[ad_1] Oct 20, 2023NewsroomMalvertising / Cyber Threat Details have emerged about a malvertising campaign that leverages Google Ads to direct users searching for popular software to fictitious landing pages and distribute next-stage payloads. Malwarebytes, which discovered the activity, said it’s “unique in its way to fingerprint users and distribute time sensitive payloads.” The attack singles…
Month: October 2023
Google Play Protect Introduces Real-Time Code-Level Scanning for Android Malware
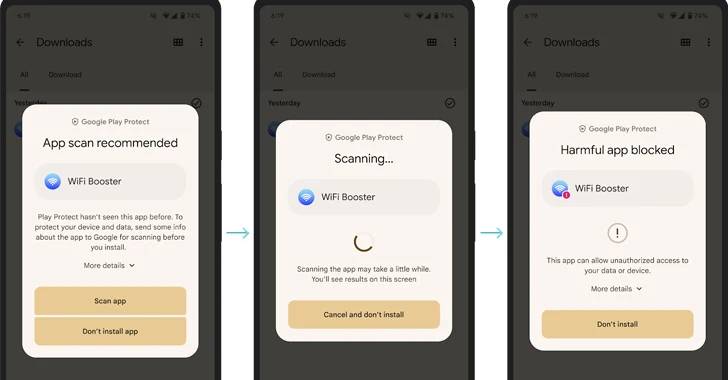
[ad_1] Oct 19, 2023NewsroomMobile Security / Technology Google has announced an update to its Play Protect with support for real-time scanning at the code level to tackle novel malicious apps prior to downloading and installing them on Android devices. “Google Play Protect will now recommend a real-time app scan when installing apps that have never…
Sophisticated MATA Framework Strikes Eastern European Oil and Gas Companies
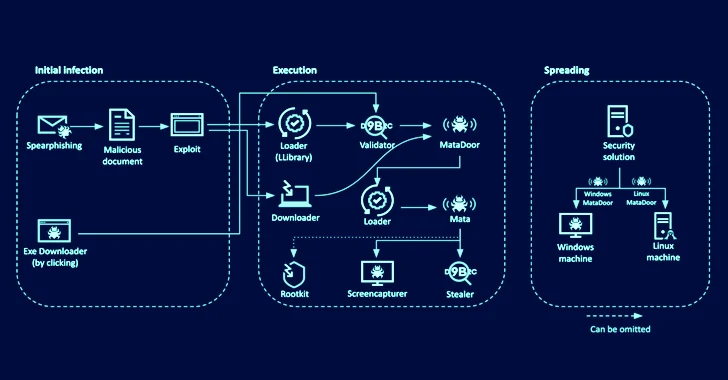
[ad_1] An updated version of a sophisticated backdoor framework called MATA has been used in attacks aimed at over a dozen Eastern European companies in the oil and gas sector and defense industry as part of a cyber espionage operation that took place between August 2022 and May 2023. “The actors behind the attack used…
How Often Should I Scan?
[ad_1] The time between a vulnerability being discovered and hackers exploiting it is narrower than ever – just 12 days. So it makes sense that organizations are starting to recognize the importance of not leaving long gaps between their scans, and the term “continuous vulnerability scanning” is becoming more popular. Hackers won’t wait for your…
Iran-Linked OilRig Targets Middle East Governments in 8-Month Cyber Campaign
[ad_1] Oct 19, 2023NewsroomCyber Attack / Cyber Espionage The Iran-linked OilRig threat actor targeted an unnamed Middle East government between February and September 2023 as part of an eight-month-long campaign. The attack led to the theft of files and passwords and, in one instance, resulted in the deployment of a PowerShell backdoor called PowerExchange, the…
Microsoft Warns of North Korean Attacks Exploiting JetBrains TeamCity Flaw
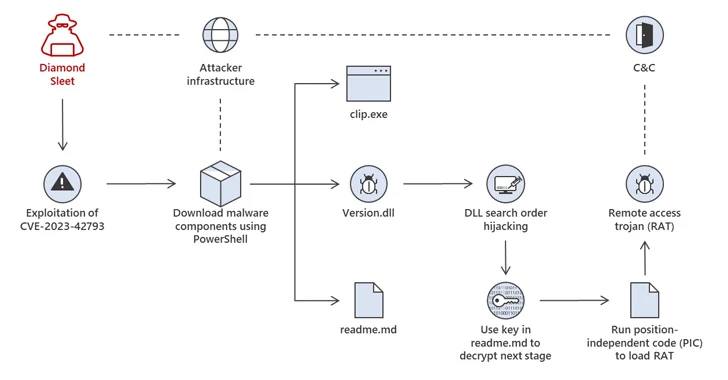
[ad_1] Oct 19, 2023Newsroom North Korean threat actors are actively exploiting a critical security flaw in JetBrains TeamCity to opportunistically breach vulnerable servers, according to Microsoft. The attacks, which entail the exploitation of CVE-2023-42793 (CVSS score: 9.8), have been attributed to Diamond Sleet (aka Labyrinth Chollima) and Onyx Sleet (aka Andariel or Silent Chollima). It’s…
Google TAG Detects State-Backed Threat Actors Exploiting WinRAR Flaw
[ad_1] Oct 19, 2023NewsroomCyber Threat / Vulnerability A number of state-back threat actors from Russia and China have been observed exploiting a recent security flaw in the WinRAR archiver tool for Windows as part of their operations. The vulnerability in question is CVE-2023-38831 (CVSS score: 7.8), which allows attackers to execute arbitrary code when a…
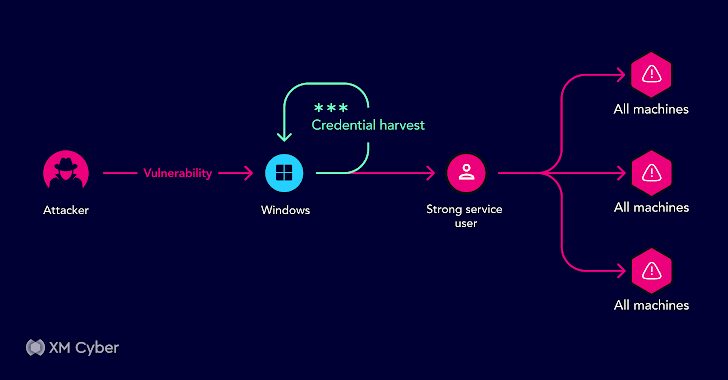
Unraveling Real-Life Attack Paths – Key Lessons Learned
[ad_1] In the ever-evolving landscape of cybersecurity, attackers are always searching for vulnerabilities and exploits within organizational environments. They don’t just target single weaknesses; they’re on the hunt for combinations of exposures and attack methods that can lead them to their desired objective. Despite the presence of numerous security tools, organizations often have to deal…
Lazarus Group Targeting Defense Experts with Fake Interviews via Trojanized VNC Apps
[ad_1] Oct 18, 2023NewsroomCyber Attack / Malware The North Korea-linked Lazarus Group (aka Hidden Cobra or TEMP.Hermit) has been observed using trojanized versions of Virtual Network Computing (VNC) apps as lures to target the defense industry and nuclear engineers as part of a long-running campaign known as Operation Dream Job. “The threat actor tricks job…
Critical Citrix NetScaler Flaw Exploited to Target from Government, Tech Firms
[ad_1] Oct 18, 2023NewsroomEnterprise Security / Vulnerability Citrix is warning of exploitation of a recently disclosed critical security flaw in NetScaler ADC and Gateway appliances that could result in exposure of sensitive information. Tracked as CVE-2023-4966 (CVSS score: 9.4), the vulnerability impacts the following supported versions – NetScaler ADC and NetScaler Gateway 14.1 before 14.1-8.50…