[ad_1] Oct 13, 2023NewsroomAPT / Malware The advanced persistent threat (APT) actor known as ToddyCat has been linked to a new set of malicious tools that are designed for data exfiltration, offering a deeper insight into the hacking crew’s tactics and capabilities. The findings come from Kaspersky, which first shed light on the adversary last…
Month: October 2023
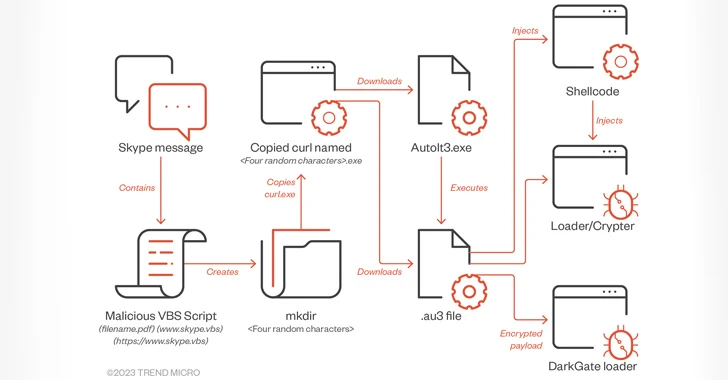
DarkGate Malware Spreading via Messaging Services Posing as PDF Files
[ad_1] Oct 13, 2023NewsroomMalware / Cyber Threat A piece of malware known as DarkGate has been observed being spread via instant messaging platforms such as Skype and Microsoft Teams. In these attacks, the messaging apps are used to deliver a Visual Basic for Applications (VBA) loader script that masquerades as a PDF document, which, when…
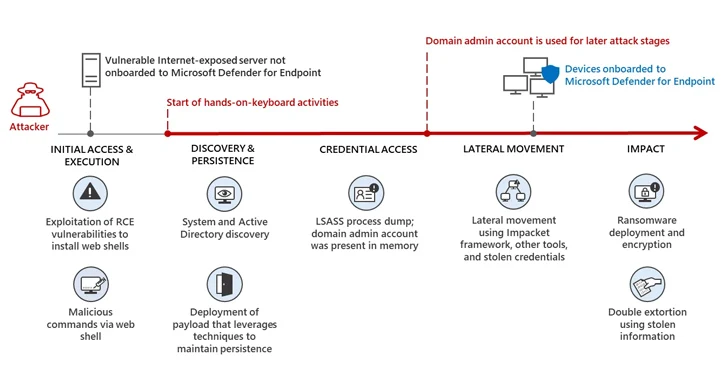
Microsoft Defender Thwarts Large-Scale Akira Ransomware Attack
[ad_1] Oct 12, 2023NewsroomThreat Intelligence / Microsoft on Wednesday said that a user containment feature in Microsoft Defender for Endpoint helped thwart a “large-scale remote encryption attempt” made by Akira ransomware actors targeting an unknown industrial organization in early June 2023. The tech giant’s threat intelligence team is tracking the operator as Storm-1567. The attack…
Malicious NuGet Package Targeting .NET Developers with SeroXen RAT
[ad_1] A malicious package hosted on the NuGet package manager for the .NET Framework has been found to deliver a remote access trojan called SeroXen RAT. The package, named Pathoschild.Stardew.Mod.Build.Config and published by a user named Disti, is a typosquat of a legitimate package called Pathoschild.Stardew.ModBuildConfig, software supply chain security firm Phylum said in a…
How to Guard Your Data from Exposure in ChatGPT
[ad_1] Oct 12, 2023The Hacker NewsData Security / Artificial Intelligence ChatGPT has transformed the way businesses generate textual content, which can potentially result in a quantum leap in productivity. However, Generative AI innovation also introduces a new dimension of data exposure risk, when employees inadvertently type or paste sensitive business data into ChatGPT, or similar…
ShellBot Uses Hex IPs to Evade Detection in Attacks on Linux SSH Servers
[ad_1] Oct 12, 2023Newsroom The threat actors behind ShellBot are leveraging IP addresses transformed into its hexadecimal notation to infiltrate poorly managed Linux SSH servers and deploy the DDoS malware. “The overall flow remains the same, but the download URL used by the threat actor to install ShellBot has changed from a regular IP address…
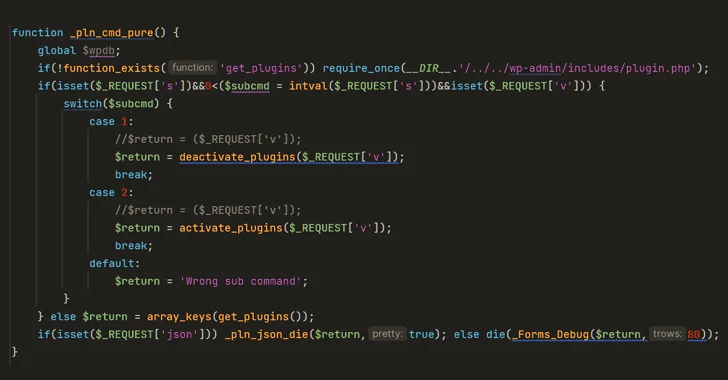
Researchers Uncover Malware Posing as WordPress Caching Plugin
[ad_1] Oct 12, 2023NewsroomWebsite Security / WordPress Cybersecurity researchers have shed light on a new sophisticated strain of malware that masquerades a WordPress plugin to stealthily create administrator accounts and remotely control a compromised site. “Complete with a professional looking opening comment implying it is a caching plugin, this rogue code contains numerous functions, adds…
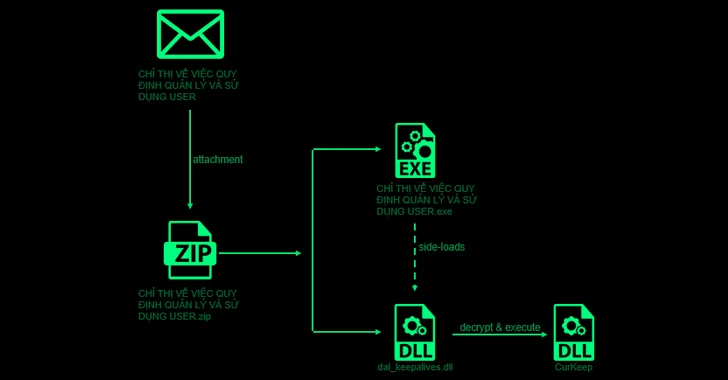
Researchers Uncover Ongoing Attacks Targeting Asian Governments and Telecom Giants
[ad_1] Oct 12, 2023NewsroomCyber Attack / Malware High-profile government and telecom entities in Asia have been targeted as part of an ongoing campaign since 2021 that’s designed to deploy basic backdoors and loaders for delivering next-stage malware. Cybersecurity company Check Point is tracking the activity under the name Stayin’ Alive. Targets include organizations located in…
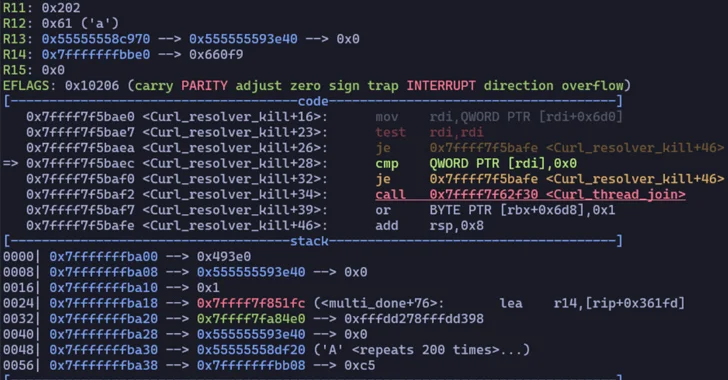
Two High-Risk Security Flaws Discovered in Curl Library
[ad_1] Oct 12, 2023NewsroomVulnerability / Software Security Patches have been released for two security flaws impacting the Curl data transfer library, the most severe of which could potentially result in code execution. The list of vulnerabilities is as follows – CVE-2023-38545 (CVSS score: 7.5) – SOCKS5 heap-based buffer overflow vulnerability CVE-2023-38546 (CVSS score: 5.0) –…
Take an Offensive Approach to Password Security by Continuously Monitoring for Breached Passwords
[ad_1] Oct 11, 2023The Hacker NewsPassword Security / Data Safety Passwords are at the core of securing access to an organization’s data. However, they also come with security vulnerabilities that stem from their inconvenience. With a growing list of credentials to keep track of, the average end-user can default to shortcuts. Instead of creating a…