[ad_1] Meta Platforms said it took a series of steps to curtail malicious activity from eight different firms based in Italy, Spain, and the United Arab Emirates (U.A.E.) operating in the surveillance-for-hire industry. The findings are part of its Adversarial Threat Report for the fourth quarter of 2023. The spyware targeted iOS, Android, and Windows…
Month: February 2024
LockBit Ransomware’s Darknet Domains Seized in Global Law Enforcement Raid
[ad_1] Feb 20, 2024NewsroomDark Web / Cybercrime Update: The U.K. National Crime Agency (NCA) has confirmed the takedown of LockBit infrastructure. Read here for more details. An international law enforcement operation has led to the seizure of multiple darknet domains operated by LockBit, one of the most prolific ransomware groups, marking the latest in a…
How to Use Tines’s SOC Automation Capability Matrix
[ad_1] Created by John Tuckner and the team at workflow and automation platform Tines, the SOC Automation Capability Matrix (SOC ACM) is a set of techniques designed to help security operations teams understand their automation capabilities and respond more effectively to incidents. A customizable, vendor-agnostic tool featuring lists of automation opportunities, it’s been shared and…
Microsoft Releases PyRIT – A Red Teaming Tool for Generative AI
[ad_1] Feb 23, 2024NewsroomRed Teaming / Artificial Intelligence Microsoft has released an open access automation framework called PyRIT (short for Python Risk Identification Tool) to proactively identify risks in generative artificial intelligence (AI) systems. The red teaming tool is designed to “enable every organization across the globe to innovate responsibly with the latest artificial intelligence…
Iran and Hezbollah Hackers Launch Attacks to Influence Israel-Hamas Narrative
[ad_1] Hackers backed by Iran and Hezbollah staged cyber attacks designed to undercut public support for the Israel-Hamas war after October 2023. This includes destructive attacks against key Israeli organizations, hack-and-leak operations targeting entities in Israel and the U.S., phishing campaigns designed to steal intelligence, and information operations to turn public opinion against Israel. Iran…
Critical Flaw Impacts 25,000+ Sites
[ad_1] Feb 20, 2024NewsroomWebsite Security / PHP Code A critical security flaw in the Bricks theme for WordPress is being actively exploited by threat actors to run arbitrary PHP code on susceptible installations. The flaw, tracked as CVE-2024-25600 (CVSS score: 9.8), enables unauthenticated attackers to achieve remote code execution. It impacts all versions of the…
Critical Flaws Found in ConnectWise ScreenConnect Software
[ad_1] Feb 20, 2024NewsroomVulnerability / Network Security ConnectWise has released software updates to address two security flaws in its ScreenConnect remote desktop and access software, including a critical bug that could enable remote code execution on affected systems. The vulnerabilities are listed below – CVE-2024-1708 (CVSS score: 8.4) – Improper limitation of a pathname to…
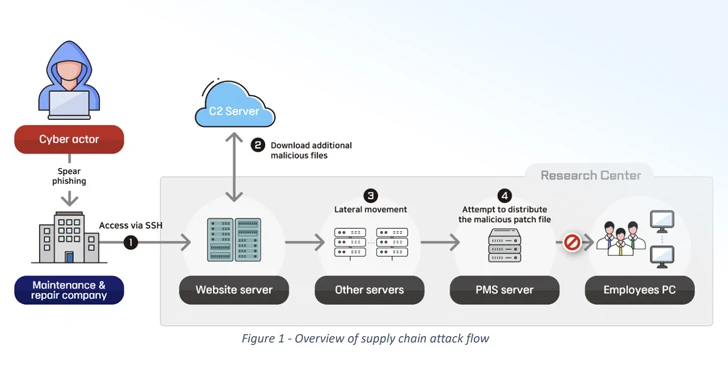
New Report Reveals North Korean Hackers Targeting Defense Firms Worldwide
[ad_1] Feb 20, 2024NewsroomHacking / Cyber Espionage North Korean state-sponsored threat actors have been attributed to a cyber espionage campaign targeting the defense sector across the world. In a joint advisory published by Germany’s Federal Office for the Protection of the Constitution (BfV) and South Korea’s National Intelligence Service (NIS), the agencies said the goal…
Researchers Detail Apple’s Recent Zero-Click Shortcuts Vulnerability
[ad_1] Feb 23, 2024NewsroomData Privacy / iOS Security Details have emerged about a now-patched high-severity security flaw in Apple’s Shortcuts app that could permit a shortcut to access sensitive information on the device without users’ consent. The vulnerability, tracked as CVE-2024-23204 (CVSS score: 7.5), was addressed by Apple on January 22, 2024, with the release…
SaaS Compliance through the NIST Cybersecurity Framework
[ad_1] The US National Institute of Standards and Technology (NIST) cybersecurity framework is one of the world’s most important guidelines for securing networks. It can be applied to any number of applications, including SaaS. One of the challenges facing those tasked with securing SaaS applications is the different settings found in each application. It makes…