[ad_1] Feb 23, 2024NewsroomPrivacy / Regulatory Compliance The U.S. Federal Trade Commission (FTC) has hit antivirus vendor Avast with a $16.5 million fine over charges that the firm sold users’ browsing data to advertisers after claiming its products would block online tracking. In addition, the company has been banned from selling or licensing any web…
Month: February 2024
Learn How to Build an Incident Response Playbook Against Scattered Spider in Real-Time
[ad_1] Feb 20, 2024The Hacker NewsWebinar / Incident Response In the tumultuous landscape of cybersecurity, the year 2023 left an indelible mark with the brazen exploits of the Scattered Spider threat group. Their attacks targeted the nerve centers of major financial and insurance institutions, culminating in what stands as one of the most impactful ransomware…
New Malicious PyPI Packages Caught Using Covert Side-Loading Tactics
[ad_1] Feb 20, 2024NewsroomMalware / Supply Chain Security Cybersecurity researchers have discovered two malicious packages on the Python Package Index (PyPI) repository that were found leveraging a technique called DLL side-loading to circumvent detection by security software and run malicious code. The packages, named NP6HelperHttptest and NP6HelperHttper, were each downloaded 537 and 166 times, respectively,…
Apple Unveils PQ3 Protocol – Post-Quantum Encryption for iMessage
[ad_1] Feb 22, 2024NewsroomQuantum Computing / Encryption Apple has announced a new post-quantum cryptographic protocol called PQ3 that it said will be integrated into iMessage to secure the messaging platform against future attacks arising from the threat of a practical quantum computer. “With compromise-resilient encryption and extensive defenses against even highly sophisticated quantum attacks, PQ3…
Russian Government Software Backdoored to Deploy Konni RAT Malware
[ad_1] Feb 22, 2024NewsroomMalware / Cyber Espionage An installer for a tool likely used by the Russian Consular Department of the Ministry of Foreign Affairs (MID) has been backdoored to deliver a remote access trojan called Konni RAT (aka UpDog). The findings come from German cybersecurity company DCSO, which linked the activity as originating from…
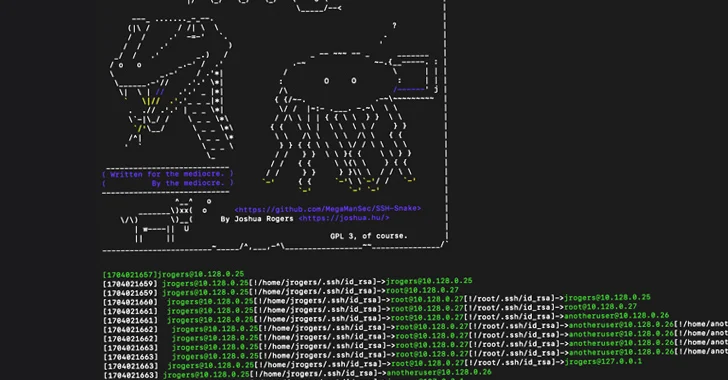
Cybercriminals Weaponizing Open-Source SSH-Snake Tool for Network Attacks
[ad_1] Feb 22, 2024NewsroomNetwork Security / Penetration Testing A recently open-sourced network mapping tool called SSH-Snake has been repurposed by threat actors to conduct malicious activities. “SSH-Snake is a self-modifying worm that leverages SSH credentials discovered on a compromised system to start spreading itself throughout the network,” Sysdig researcher Miguel Hernández said. “The worm automatically…
A New Age of Hacktivism
[ad_1] In the past 2 years, we have observed a significant surge in hacktivism activity due to ongoing wars and geopolitical conflicts in various regions. Since the war against Ukraine began, we have witnessed a notable mobilization of non-state and state-backed actors alike, forming new groups or joining existing hacker collectives. We understand hacktivism as…
LockBit Ransomware Operation Shut Down; Criminals Arrested; Decryption Keys Released
[ad_1] Feb 20, 2024NewsroomRansomware / Data Protection The U.K. National Crime Agency (NCA) on Tuesday confirmed that it obtained LockBit’s source code as well as a wealth of intelligence pertaining to its activities and their affiliates as part of a dedicated task force called Operation Cronos. “Some of the data on LockBit’s systems belonged to…
New Migo Malware Targeting Redis Servers for Cryptocurrency Mining
[ad_1] Feb 20, 2024NewsroomServer Security / Cryptojacking A novel malware campaign has been observed targeting Redis servers for initial access with the ultimate goal of mining cryptocurrency on compromised Linux hosts. “This particular campaign involves the use of a number of novel system weakening techniques against the data store itself,” Cado security researcher Matt Muir…
VMware Alert: Uninstall EAP Now
[ad_1] Feb 21, 2024NewsroomActive Directory / Vulnerability VMware is urging users to uninstall the deprecated Enhanced Authentication Plugin (EAP) following the discovery of a critical security flaw. Tracked as CVE-2024-22245 (CVSS score: 9.6), the vulnerability has been described as an arbitrary authentication relay bug. “A malicious actor could trick a target domain user with EAP…