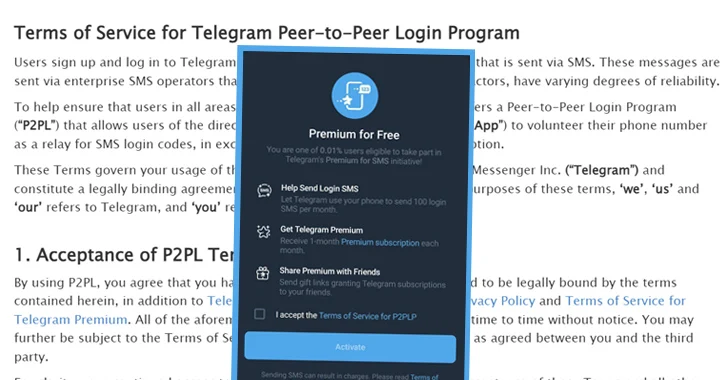
[ad_1] Mar 28, 2024NewsroomTechnology / Data Privacy In June 2017, a study of more than 3,000 Massachusetts Institute of Technology (MIT) students published by the National Bureau for Economic Research (NBER) found that 98% of them were willing to give away their friends’ email addresses in exchange for free pizza. “Whereas people say they care…
Month: March 2024
Hackers Actively Attacking Microsoft SharePoint Vulnerability
[ad_1] Mar 27, 2024NewsroomThreat Intelligence / Network Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a security flaw impacting the Microsoft Sharepoint Server to its Known Exploited Vulnerabilities (KEV) catalog based on evidence of active exploitation in the wild. The vulnerability, tracked as CVE-2023-24955 (CVSS score: 7.2), is a critical remote code…
Hackers Hit Indian Defense, Energy Sectors with Malware Posing as Air Force Invite
[ad_1] Mar 27, 2024NewsroomCyber Espionage / Data Breach Indian government entities and energy companies have been targeted by unknown threat actors with an aim to deliver a modified version of an open-source information stealer malware called HackBrowserData and exfiltrate sensitive information in some cases by using Slack as command-and-control (C2). “The information stealer was delivered…
New Phishing Attack Delivers Keylogger Disguised as Bank Payment Notice
[ad_1] Mar 27, 2024NewsroomVulnerability / Cybercrime A new phishing campaign has been observed leveraging a novel loader malware to deliver an information stealer and keylogger called Agent Tesla. Trustwave SpiderLabs said it identified a phishing email bearing this attack chain on March 8, 2024. The message masquerades as a bank payment notification, urging the user…
U.S. Charges 7 Chinese Nationals in Major 14-Year Cyber Espionage Operation
[ad_1] The U.S. Department of Justice (DoJ) on Monday unsealed indictments against seven Chinese nationals for their involvement in a hacking group that targeted U.S. and foreign critics, journalists, businesses, and political officials for about 14 years. The defendants include Ni Gaobin (倪高彬), Weng Ming (翁明), Cheng Feng (程锋), Peng Yaowen (彭耀文), Sun Xiaohui (孙小辉),…
Malicious NuGet Package Linked to Industrial Espionage Targets Developers
[ad_1] Mar 26, 2024NewsroomIndustrial Espionage / Threat Intelligence Threat hunters have identified a suspicious package in the NuGet package manager that’s likely designed to target developers working with tools made by a Chinese firm that specializes in industrial- and digital equipment manufacturing. The package in question is SqzrFramework480, which ReversingLabs said was first published on…
U.S. Sanctions 3 Cryptocurrency Exchanges for Helping Russia Evade Sanctions
[ad_1] Mar 26, 2024NewsroomMoney Laundering / Digital Currency The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) sanctioned three cryptocurrency exchanges for offering services used to evade economic restrictions imposed on Russia following its invasion of Ukraine in early 2022. This includes Bitpapa IC FZC LLC, Crypto Explorer DMCC (AWEX), and Obshchestvo…
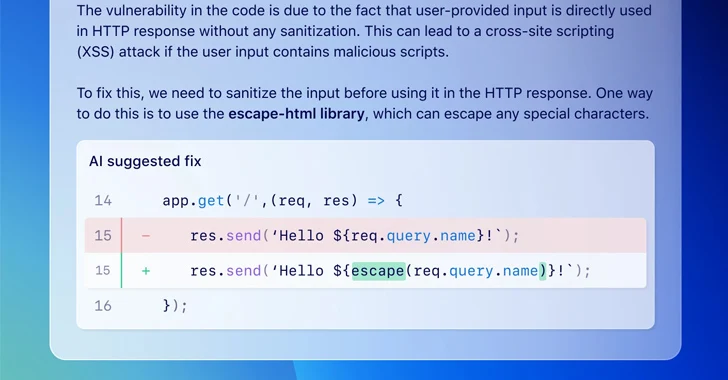
GitHub Launches AI-Powered Autofix Tool to Assist Devs in Patching Security Flaws
[ad_1] Mar 21, 2024NewsroomMachine Learning / Software Security GitHub on Wednesday announced that it’s making available a feature called code scanning autofix in public beta for all Advanced Security customers to provide targeted recommendations in an effort to avoid introducing new security issues. “Powered by GitHub Copilot and CodeQL, code scanning autofix covers more than…
How to Accelerate Vendor Risk Assessments in the Age of SaaS Sprawl
[ad_1] In today’s digital-first business environment dominated by SaaS applications, organizations increasingly depend on third-party vendors for essential cloud services and software solutions. As more vendors and services are added to the mix, the complexity and potential vulnerabilities within the SaaS supply chain snowball quickly. That’s why effective vendor risk management (VRM) is a critical…
AndroxGh0st Malware Targets Laravel Apps to Steal Cloud Credentials
[ad_1] Mar 21, 2024NewsroomThreat Intelligence / Vulnerability Cybersecurity researchers have shed light on a tool referred to as AndroxGh0st that’s used to target Laravel applications and steal sensitive data. “It works by scanning and taking out important information from .env files, revealing login details linked to AWS and Twilio,” Juniper Threat Labs researcher Kashinath T…