[ad_1] Like antivirus software, vulnerability scans rely on a database of known weaknesses. That’s why websites like VirusTotal exist, to give cyber practitioners a chance to see whether a malware sample is detected by multiple virus scanning engines, but this concept hasn’t existed in the vulnerability management space. The benefits of using multiple scanning engines…
Month: May 2024
Ukrainian REvil Hacker Sentenced to 13 Years and Ordered to Pay $16 Million
[ad_1] May 02, 2024NewsroomRansomware / Cyber Crime A Ukrainian national has been sentenced to more than 13 years in prison and ordered to pay $16 million in restitution for carrying out thousands of ransomware attacks and extorting victims. Yaroslav Vasinskyi (aka Rabotnik), 24, along with his co-conspirators part of the REvil ransomware group orchestrated more…
Popular Android Apps Like Xiaomi, WPS Office Vulnerable to File Overwrite Flaw
[ad_1] May 02, 2024NewsroomVulnerability / Android Several popular Android applications available in Google Play Store are susceptible to a path traversal-affiliated vulnerability codenamed the Dirty Stream attack that could be exploited by a malicious app to overwrite arbitrary files in the vulnerable app’s home directory. “The implications of this vulnerability pattern include arbitrary code execution…
Four Critical Vulnerabilities Expose HPE Aruba Devices to RCE Attacks
[ad_1] May 03, 2024NewsroomVulnerability / Software Security HPE Aruba Networking (formerly Aruba Networks) has released security updates to address critical flaws impacting ArubaOS that could result in remote code execution (RCE) on affected systems. Of the 10 security defects, four are rated critical in severity – CVE-2024-26304 (CVSS score: 9.8) – Unauthenticated Buffer Overflow Vulnerability…
Google Announces Passkeys Adopted by Over 400 Million Accounts
[ad_1] May 03, 2024NewsroomPasswordless / Encryption Google on Thursday announced that passkeys are being used by over 400 million Google accounts, authenticating users more than 1 billion times over the past two years. “Passkeys are easy to use and phishing resistant, only relying on a fingerprint, face scan or a pin making them 50% faster…
NSA, FBI Alert on N. Korean Hackers Spoofing Emails from Trusted Sources
[ad_1] May 03, 2024NewsroomEmail Security / Malware The U.S. government on Thursday published a new cybersecurity advisory warning of North Korean threat actors’ attempts to send emails in a manner that makes them appear like they are from legitimate and trusted parties. The joint bulletin was published by the National Security Agency (NSA), the Federal…
New Guide Explains How to Eliminate the Risk of Shadow SaaS and Protect Corporate Data
[ad_1] May 03, 2024The Hacker NewsSaaS Security / Browser Security SaaS applications are dominating the corporate landscape. Their increased use enables organizations to push the boundaries of technology and business. At the same time, these applications also pose a new security risk that security leaders need to address, since the existing security stack does not…
Hackers Increasingly Abusing Microsoft Graph API for Stealthy Malware Communications
[ad_1] May 03, 2024NewsroomCloud Security / Threat Intelligence Threat actors have been increasingly weaponizing Microsoft Graph API for malicious purposes with the aim of evading detection. This is done to “facilitate communications with command-and-control (C&C) infrastructure hosted on Microsoft cloud services,” the Symantec Threat Hunter Team, part of Broadcom, said in a report shared with…
Expert-Led Webinar – Uncovering Latest DDoS Tactics and Learn How to Fight Back
[ad_1] May 03, 2024The Hacker NewsLive Webinar / Server Security In today’s rapidly evolving digital landscape, the threat of Distributed Denial of Service (DDoS) attacks looms more significant than ever. As these cyber threats grow in sophistication, understanding and countering them becomes crucial for any business seeking to protect its online presence. To address this…
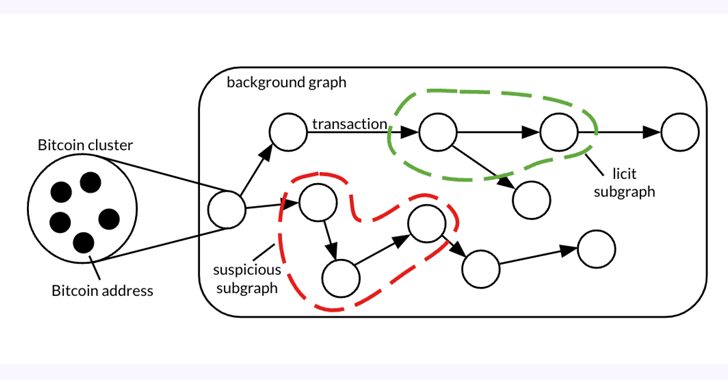
Bitcoin Forensic Analysis Uncovers Money Laundering Clusters and Criminal Proceeds
[ad_1] May 01, 2024NewsroomFinancial Crime / Forensic Analysis A forensic analysis of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters associated with illicit activity and money laundering, including detecting criminal proceeds sent to a crypto exchange and previously unknown wallets belonging to a Russian darknet market. The findings come from Elliptic…