[ad_1] Jun 04, 2024NewsroomServer Security / Vulnerability Progress Software has rolled out updates to address a critical security flaw impacting the Telerik Report Server that could be potentially exploited by a remote attacker to bypass authentication and create rogue administrator users. The issue, tracked as CVE-2024-4358, carries a CVSS score of 9.8 out of a…
Month: June 2024
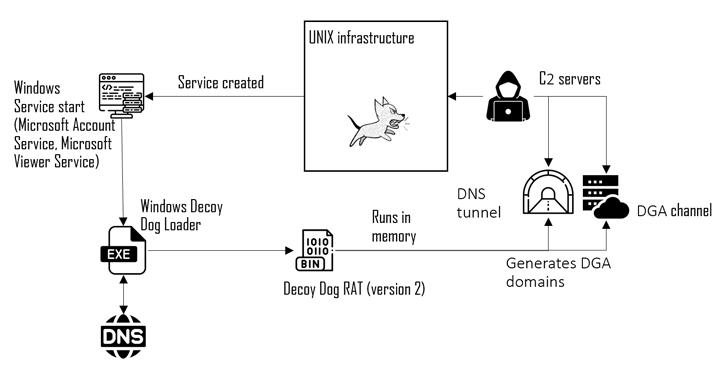
Russian Power Companies, IT Firms, and Govt Agencies Hit by Decoy Dog Trojan
[ad_1] Jun 04, 2024NewsroomCyber Attack / Malware Russian organizations are at the receiving end of cyber attacks that have been found to deliver a Windows version of a malware called Decoy Dog. Cybersecurity company Positive Technologies is tracking the activity cluster under the name Operation Lahat, attributing it to an advanced persistent threat (APT) group…
The Next Generation of RBI (Remote Browser Isolation)
[ad_1] Jun 04, 2024The Hacker NewsBrowser Security / Enterprise Security The landscape of browser security has undergone significant changes over the past decade. While Browser Isolation was once considered the gold standard for protecting against browser exploits and malware downloads, it has become increasingly inadequate and insecure in today’s SaaS-centric world. The limitations of Browser…
Oracle WebLogic Server OS Command Injection Flaw Under Active Attack
[ad_1] Jun 04, 2024NewsroomNetwork Security / Cryptocurrency The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a security flaw impacting the Oracle WebLogic Server to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. Tracked as CVE-2017-3506 (CVSS score: 7.4), the issue concerns an operating system (OS) command injection vulnerability that…
Researchers Uncover RAT-Dropping npm Package Targeting Gulp Users
[ad_1] Jun 03, 2024NewsroomSoftware Security / Supply Chain Cybersecurity researchers have uncovered a new suspicious package uploaded to the npm package registry that’s designed to drop a remote access trojan (RAT) on compromised systems. The package in question is glup-debugger-log, which targets users of the gulp toolkit by masquerading as a “logger for gulp and…
8 Key Findings for Enterprise Security
[ad_1] Jun 03, 2024The Hacker NewsCyber Threat Intelligence Threat actors are evolving, yet Cyber Threat Intelligence (CTI) remains confined to each isolated point solution. Organizations require a holistic analysis across external data, inbound and outbound threats and network activity. This will enable evaluating the true state of cybersecurity in the enterprise. Cato’s Cyber Threat Research…
Fake Browser Updates Deliver BitRAT and Lumma Stealer Malware
[ad_1] Fake web browser updates are being used to deliver remote access trojans (RATs) and information stealer malware such as BitRAT and Lumma Stealer (aka LummaC2). “Fake browser updates have been responsible for numerous malware infections, including those of the well-known SocGholish malware,” cybersecurity firm eSentire said in a new report. “In April 2024, we…
RedTail Crypto-Mining Malware Exploiting Palo Alto Networks Firewall Vulnerability
[ad_1] May 30, 2024NewsroomVulnerability / Cryptocurrency The threat actors behind the RedTail cryptocurrency mining malware have added a recently disclosed security flaw impacting Palo Alto Networks firewalls to its exploit arsenal. The addition of the PAN-OS vulnerability to its toolkit has been complemented by updates to the malware, which now incorporates new anti-analysis techniques, according…
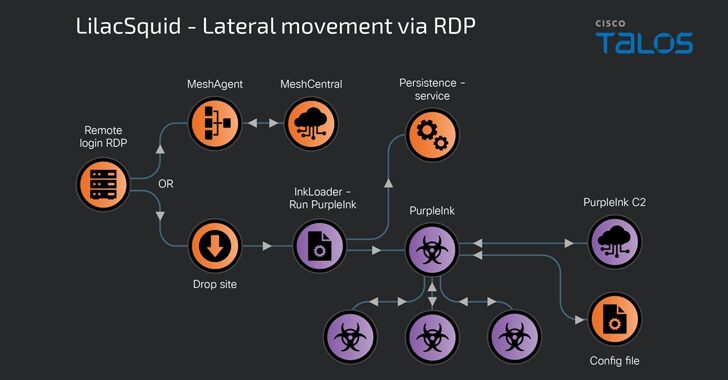
LilacSquid Targets IT, Energy, and Pharma Sectors
[ad_1] May 30, 2024NewsroomCyber Espionage / Threat Intelligence A previously undocumented cyber espionage-focused threat actor named LilacSquid has been linked to targeted attacks spanning various sectors in the United States (U.S.), Europe, and Asia as part of a data theft campaign since at least 2021. “The campaign is geared toward establishing long-term access to compromised…
OpenAI, Meta, and TikTok Crack Down on Covert Influence Campaigns, Some AI-Powered
[ad_1] OpenAI on Thursday disclosed that it took steps to cut off five covert influence operations (IO) originating from China, Iran, Israel, and Russia that sought to abuse its artificial intelligence (AI) tools to manipulate public discourse or political outcomes online while obscuring their true identity. These activities, which were detected over the past three…