[ad_1] Aug 07, 2024Ravie LakshmananCloud Security / Cyber Espionage An unnamed media organization in South Asia was targeted in November 20233 using a previously undocumented Go-based backdoor called GoGra. “GoGra is written in Go and uses the Microsoft Graph API to interact with a command-and-control (C&C) server hosted on Microsoft mail services,” Symantec, part of…
Month: August 2024
Insider Threats in The SaaS World
[ad_1] Aug 06, 2024The Hacker NewsSaaS Security / Threat Detection Everyone loves the double-agent plot twist in a spy movie, but it’s a different story when it comes to securing company data. Whether intentional or unintentional, insider threats are a legitimate concern. According to CSA research, 26% of companies who reported a SaaS security incident…
INTERPOL Recovers $41 Million in Largest Ever BEC Scam in Singapore
[ad_1] Aug 06, 2024Ravie LakshmananEmail Security / Financial Fraud INTERPOL said it devised a “global stop-payment mechanism” that helped facilitate the largest-ever recovery of funds defrauded in a business email compromise (BEC) scam. The development comes after an unnamed commodity firm based in Singapore fell victim to a BEC scam in mid-July 2024. It refers…
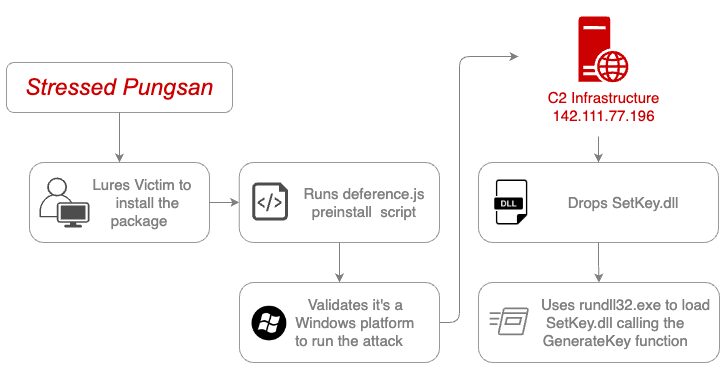
North Korean Hackers Moonstone Sleet Push Malicious JS Packages to npm Registry
[ad_1] Aug 06, 2024Ravie LakshmananMalware / Windows Security The North Korea-linked threat actor known as Moonstone Sleet has continued to push malicious npm packages to the JavaScript package registry with the aim of infecting Windows systems, underscoring the persistent nature of their campaigns. The packages in question, harthat-api and harthat-hash, were published on July 7,…
Kazakh Organizations Targeted by ‘Bloody Wolf’ Cyber Attacks
[ad_1] Aug 05, 2024Ravie LakshmananNetwork Security / Threat Intelligence Organizations in Kazakhstan are the target of a threat activity cluster dubbed Bloody Wolf that delivers a commodity malware called STRRAT (aka Strigoi Master). “The program selling for as little as $80 on underground resources allows the adversaries to take control of corporate computers and hijack…
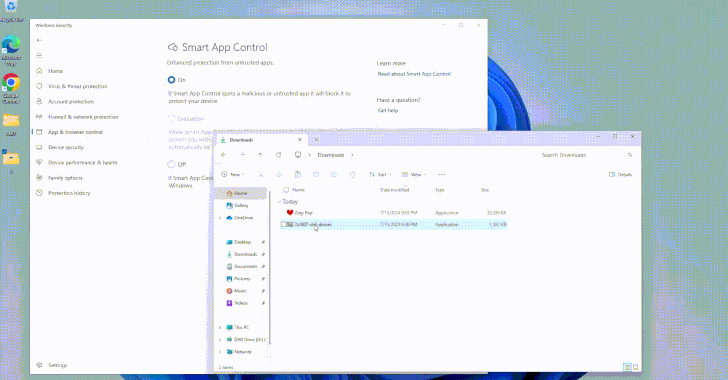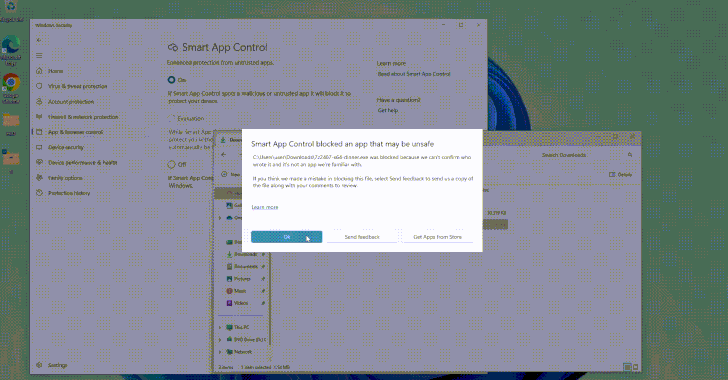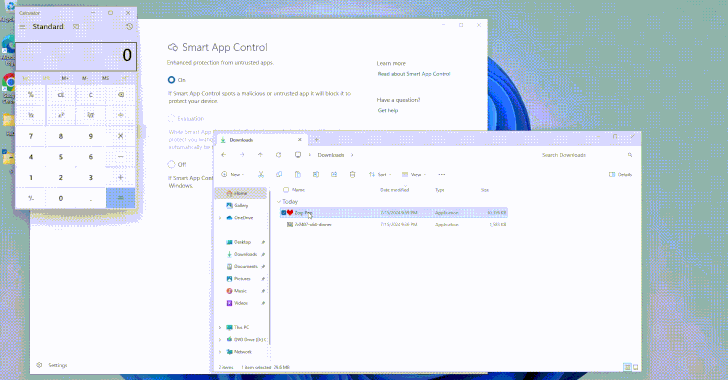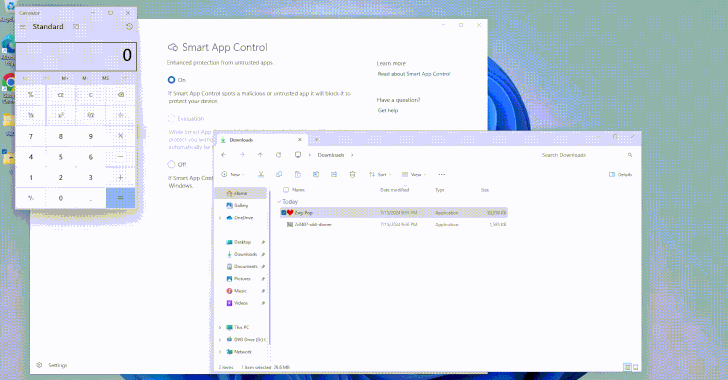
Researchers Uncover Flaws in Windows Smart App Control and SmartScreen
[ad_1] Aug 05, 2024Ravie LakshmananThreat Intelligence / Vulnerability Cybersecurity researchers have uncovered design weaknesses in Microsoft’s Windows Smart App Control and SmartScreen that could enable threat actors to gain initial access to target environments without raising any warnings. Smart App Control (SAC) is a cloud-powered security feature introduced by Microsoft in Windows 11 to block…
How it Impacts Cybersecurity Law
[ad_1] Aug 05, 2024The Hacker NewsCybersecurity Law / Data Privacy The Loper Bright decision has yielded impactful results: the Supreme Court has overturned forty years of administrative law, leading to potential litigation over the interpretation of ambiguous laws previously decided by federal agencies. This article explores key questions for cybersecurity professionals and leaders as we…
Cybercriminals Abusing Cloudflare Tunnels to Evade Detection and Spread Malware
[ad_1] Aug 02, 2024Ravie LakshmananMalware / Network Security Cybersecurity companies are warning about an uptick in the abuse of Clouflare’s TryCloudflare free service for malware delivery. The activity, documented by both eSentire and Proofpoint, entails the use of TryCloudflare to create a rate-limited tunnel that acts as a conduit to relay traffic from an attacker-controlled…
U.S. Releases High-Profile Russian Hackers in Diplomatic Prisoner Exchange
[ad_1] Aug 02, 2024Ravie LakshmananCyber Crime / Hacking News In a historic prisoner exchange between Belarus, Germany, Norway, Russia, Slovenia, and the U.S., two Russian nationals serving time for cybercrime activities have been freed and repatriated to their country. This includes Roman Valerevich Seleznev and Vladislav Klyushin, who are part of a group of eight…
New Windows Backdoor BITSLOTH Exploits BITS for Stealthy Communication
[ad_1] Aug 02, 2024Ravie LakshmananCyber Attack / Windows Security Cybersecurity researchers have discovered a previously undocumented Windows backdoor that leverages a built-in feature called Background Intelligent Transfer Service (BITS) as a command-and-control (C2) mechanism. The newly identified malware strain has been codenamed BITSLOTH by Elastic Security Labs, which made the discovery on June 25, 2024,…