[ad_1] Oct 12, 2024Ravie LakshmananCryptocurrency / Cybercrime The U.S. Department of Justice (DoJ) has announced arrests and charges against several individuals and entities in connection with allegedly manipulating digital asset markets as part of a widespread fraud operation. The law enforcement action – codenamed Operation Token Mirrors – is the result of the U.S. Federal…
Month: October 2024
GitHub, Telegram Bots, and QR Codes Abused in New Wave of Phishing Attacks
[ad_1] A new tax-themed malware campaign targeting insurance and finance sectors has been observed leveraging GitHub links in phishing email messages as a way to bypass security measures and deliver Remcos RAT, indicating that the method is gaining traction among threat actors. “In this campaign, legitimate repositories such as the open-source tax filing software, UsTaxes,…
How Hybrid Password Attacks Work and How to Defend Against Them
[ad_1] Threat actors constantly change tactics to bypass cybersecurity measures, developing innovative methods to steal user credentials. Hybrid password attacks merge multiple cracking techniques to amplify their effectiveness. These combined approaches exploit the strengths of various methods, accelerating the password-cracking process. In this post, we’ll explore hybrid attacks — what they are and the most…
New Critical GitLab Vulnerability Could Allow Arbitrary CI/CD Pipeline Execution
[ad_1] Oct 11, 2024Ravie LakshmananDevOps / Vulnerability GitLab has released security updates for Community Edition (CE) and Enterprise Edition (EE) to address eight security flaws, including a critical bug that could allow running Continuous Integration and Continuous Delivery (CI/CD) pipelines on arbitrary branches. Tracked as CVE-2024-9164, the vulnerability carries a CVSS score of 9.6 out…
Experts Warn of Critical Unpatched Vulnerability in Linear eMerge E3 Systems
[ad_1] Oct 10, 2024Ravie LakshmananVulnerability / Enterprise Security Cybersecurity security researchers are warning about an unpatched vulnerability in Nice Linear eMerge E3 access controller systems that could allow for the execution of arbitrary operating system (OS) commands. The flaw, assigned the CVE identifier CVE-2024-9441, carries a CVSS score of 9.8 out of a maximum of…
OpenAI Blocks 20 Global Malicious Campaigns Using AI for Cybercrime and Disinformation
[ad_1] Oct 10, 2024Ravie LakshmananCybercrime / Disinformation OpenAI on Wednesday said it has disrupted more than 20 operations and deceptive networks across the world that attempted to use its platform for malicious purposes since the start of the year. This activity encompassed debugging malware, writing articles for websites, generating biographies for social media accounts, and…
Cybercriminals Use Unicode to Hide Mongolian Skimmer in E-Commerce Platforms
[ad_1] Oct 10, 2024Ravie LakshmananCybercrime / Malware Cybersecurity researchers have shed light on a new digital skimmer campaign that leverages Unicode obfuscation techniques to conceal a skimmer dubbed Mongolian Skimmer. “At first glance, the thing that stood out was the script’s obfuscation, which seemed a bit bizarre because of all the accented characters,” Jscrambler researchers…
Google Joins Forces with GASA and DNS RF to Tackle Online Scams at Scale
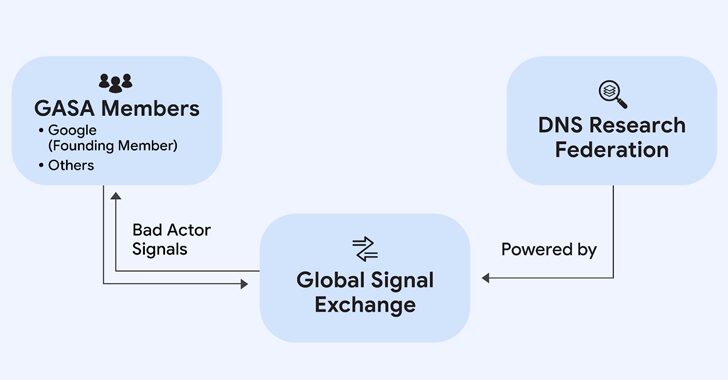
[ad_1] Oct 09, 2024Ravie LakshmananCybercrime / Threat Detection Google on Wednesday announced a new partnership with the Global Anti-Scam Alliance (GASA) and DNS Research Federation (DNS RF) to combat online scams. The initiative, which has been codenamed the Global Signal Exchange (GSE), is designed to create real-time insights into scams, fraud, and other forms of…
Researchers Uncover Major Security Vulnerabilities in Industrial MMS Protocol Libraries
[ad_1] Oct 09, 2024Ravie LakshmananIndustrial Security / Critical Infrastructure Details have emerged about multiple security vulnerabilities in two implementations of the Manufacturing Message Specification (MMS) protocol that, if successfully exploited, could have severe impacts in industrial environments. “The vulnerabilities could allow an attacker to crash an industrial device or in some cases, enable remote code…
N. Korean Hackers Use Fake Interviews to Infect Developers with Cross-Platform Malware
[ad_1] Oct 09, 2024Ravie LakshmananPhishing Attack / Malware Threat actors with ties to North Korea have been observed targeting job seekers in the tech industry to deliver updated versions of known malware families tracked as BeaverTail and InvisibleFerret. The activity cluster, tracked as CL-STA-0240, is part of a campaign dubbed Contagious Interview that Palo Alto…