[ad_1] Nov 14, 2024Ravie LakshmananMalware / Vulnerability A newly patched security flaw impacting Windows NT LAN Manager (NTLM) was exploited as a zero-day by a suspected Russia-linked actor as part of cyber attacks targeting Ukraine. The vulnerability in question, CVE-2024-43451 (CVSS score: 6.5), refers to an NTLM hash disclosure spoofing vulnerability that could be exploited…
Month: November 2024
Iranian Hackers Deploy WezRat Malware in Attacks Targeting Israeli Organizations
[ad_1] Nov 15, 2024Ravie LakshmananCyber Espionage / Malware Cybersecurity researchers have shed light on a new remote access trojan and information stealer used by Iranian state-sponsored actors to conduct reconnaissance of compromised endpoints and execute malicious commands. Cybersecurity company Check Point has codenamed the malware WezRat, stating it has been detected in the wild since…
Vietnamese Hacker Group Deploys New PXA Stealer Targeting Europe and Asia
[ad_1] Nov 15, 2024Ravie LakshmananMalware / Credential Theft A Vietnamese-speaking threat actor has been linked to an information-stealing campaign targeting government and education entities in Europe and Asia with a new Python-based malware called PXA Stealer. The malware “targets victims’ sensitive information, including credentials for various online accounts, VPN and FTP clients, financial information, browser…
Join This Webinar on Crypto Agility and Best Practices
[ad_1] Nov 15, 2024The Hacker NewsWebinar / Cyber Security In the fast-paced digital world, trust is everything—but what happens when that trust is disrupted? Certificate revocations, though rare, can send shockwaves through your operations, impacting security, customer confidence, and business continuity. Are you prepared to act swiftly when the unexpected happens? Join DigiCert’s exclusive webinar,…
Researchers Warn of Privilege Escalation Risks in Google’s Vertex AI ML Platform
[ad_1] Nov 15, 2024Ravie LakshmananArtificial Intelligence / Vulnerability Cybersecurity researchers have disclosed two security flaws in Google’s Vertex machine learning (ML) platform that, if successfully exploited, could allow malicious actors to escalate privileges and exfiltrate models from the cloud. “By exploiting custom job permissions, we were able to escalate our privileges and gain unauthorized access…
How AI Is Transforming IAM and Identity Security
[ad_1] In recent years, artificial intelligence (AI) has begun revolutionizing Identity Access Management (IAM), reshaping how cybersecurity is approached in this crucial field. Leveraging AI in IAM is about tapping into its analytical capabilities to monitor access patterns and identify anomalies that could signal a potential security breach. The focus has expanded beyond merely managing…
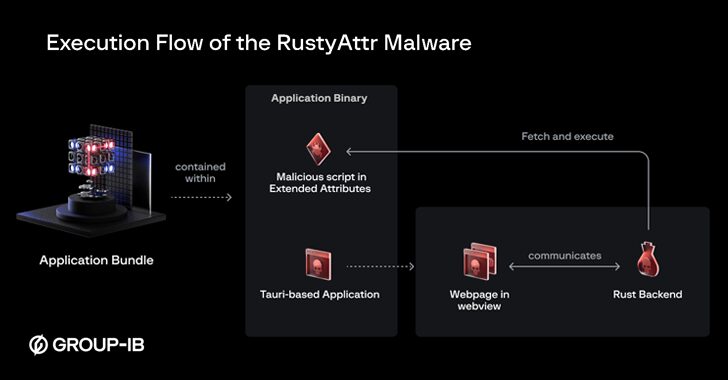
New RustyAttr Malware Targets macOS Through Extended Attribute Abuse
[ad_1] Nov 14, 2024Ravie LakshmananCryptojacking / Threat Intelligence Threat actors have been found leveraging a new technique that abuses extended attributes for macOS files to smuggle a new malware called RustyAttr. The Singaporean cybersecurity company has attributed the novel activity with moderate confidence to the infamous North Korea-linked Lazarus Group, citing infrastructure and tactical overlaps…
High-Severity Flaw in PostgreSQL Allows Hackers to Exploit Environment Variables
[ad_1] Nov 15, 2024Ravie LakshmananVulnerability / Database Security Cybersecurity researchers have disclosed a high-severity security flaw in the PostgreSQL open-source database system that could allow unprivileged users to alter environment variables, and potentially lead to code execution or information disclosure. The vulnerability, tracked as CVE-2024-10979, carries a CVSS score of 8.8. Environment variables are user-defined…
Bitfinex Hacker Sentenced to 5 Years, Guilty of Laundering $10.5 Billion in Bitcoin
[ad_1] Ilya Lichtenstein, who pleaded guilty to the 2016 hack of cryptocurrency stock exchange Bitfinex, has been sentenced to five years in prison, the U.S. Department of Justice (DoJ) announced Thursday. Lichtenstein was charged for his involvement in a money laundering scheme that led to the theft of nearly 120,000 bitcoins (valued at over $10.5…
CISA Flags Two Actively Exploited Palo Alto Flaws; New RCE Attack Confirmed
[ad_1] Nov 15, 2024Ravie LakshmananNetwork Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday warned that two more flaws impacting the Palo Alto Networks Expedition have come under active exploitation in the wild. To that, it has added the vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, requiring Federal Civilian Executive…