[ad_1] Jan 16, 2025Ravie LakshmananMalware / Ransomware Threat actors have been observed concealing malicious code in images to deliver malware such as VIP Keylogger and 0bj3ctivity Stealer as part of separate campaigns. “In both campaigns, attackers hid malicious code in images they uploaded to archive[.]org, a file-hosting website, and used the same .NET loader to…
Month: January 2025
Researchers Find Exploit Allowing NTLMv1 Despite Active Directory Restrictions
[ad_1] Jan 16, 2025Ravie LakshmananActive Directory / Vulnerability Cybersecurity researchers have found that the Microsoft Active Directory Group Policy that’s designed to disable NT LAN Manager (NTLM) v1 can be trivially bypassed by a misconfiguration. “A simple misconfiguration in on-premise applications can override the Group Policy, effectively negating the Group Policy designed to stop NTLMv1…
Russian Star Blizzard Shifts Tactics to Exploit WhatsApp QR Codes for Credential Harvesting
[ad_1] Jan 16, 2025Ravie LakshmananSpear Phishing / Threat Intelligence The Russian threat actor known as Star Blizzard has been linked to a new spear-phishing campaign that targets victims’ WhatsApp accounts, signaling a departure from its longstanding tradecraft in a likely attempt to evade detection. “Star Blizzard’s targets are most commonly related to government or diplomacy…
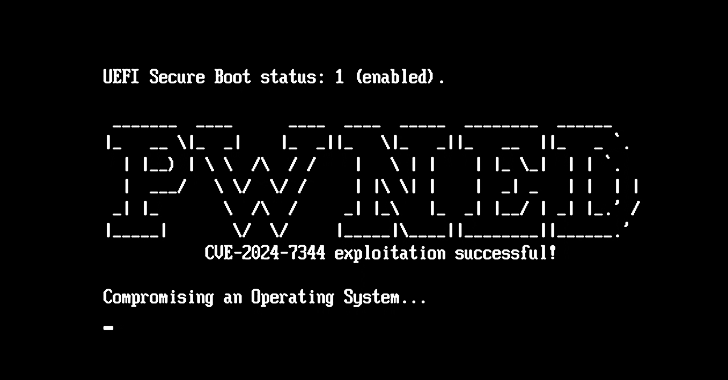
New UEFI Secure Boot Vulnerability Could Allow Attackers to Load Malicious Bootkits
[ad_1] Jan 16, 2025Ravie LakshmananVulnerability / Cybersecurity Details have emerged about a now-patched security vulnerability that could allow a bypass of the Secure Boot mechanism in Unified Extensible Firmware Interface (UEFI) systems. The vulnerability, assigned the CVE identifier CVE-2024-7344 (CVSS score: 6.7), resides in a UEFI application signed by Microsoft’s “Microsoft Corporation UEFI CA 2011”…
The $10 Cyber Threat Responsible for the Biggest Breaches of 2024
[ad_1] You can tell the story of the current state of stolen credential-based attacks in three numbers: Stolen credentials were the #1 attacker action in 2023/24, and the breach vector for 80% of web app attacks. (Source: Verizon). Cybersecurity budgets grew again in 2024, with organizations now spending almost $1,100 per user (Source: Forrester). Stolen…
Ready to Simplify Trust Management? Join Free Webinar to See DigiCert ONE in Action
[ad_1] Jan 16, 2025The Hacker NewsCertificate Management / Compliance The digital world is exploding. IoT devices are multiplying like rabbits, certificates are piling up faster than you can count, and compliance requirements are tightening by the day. Keeping up with it all can feel like trying to juggle chainsaws while riding a unicycle. Traditional trust…
Python-Based Malware Powers RansomHub Ransomware to Exploit Network Flaws
[ad_1] Jan 16, 2025Ravie LakshmananEndpoint Security / Ransomware Cybersecurity researchers have detailed an attack that involved a threat actor utilizing a Python-based backdoor to maintain persistent access to compromised endpoints and then leveraged this access to deploy the RansomHub ransomware throughout the target network. According to GuidePoint Security, initial access is said to have been…
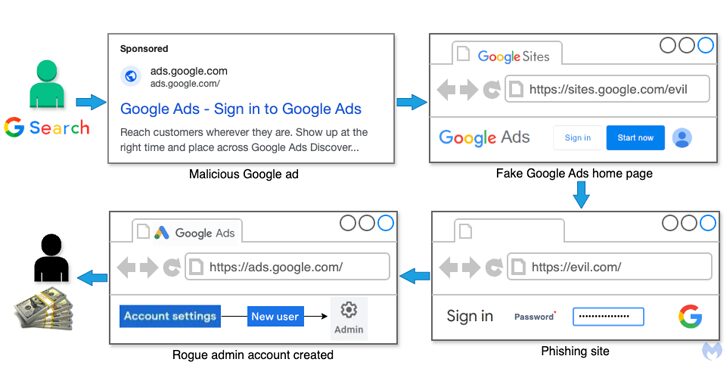
Google Ads Users Targeted in Malvertising Scam Stealing Credentials and 2FA Codes
[ad_1] Jan 15, 2025Ravie LakshmananMalvertising / Malware Cybersecurity researchers have alerted to a new malvertising campaign that’s targeting individuals and businesses advertising via Google Ads by attempting to phish for their credentials via fraudulent ads on Google. “The scheme consists of stealing as many advertiser accounts as possible by impersonating Google Ads and redirecting victims…
North Korean IT Worker Fraud Linked to 2016 Crowdfunding Scam and Fake Domains
[ad_1] Jan 15, 2025Ravie LakshmananBlockchain / Cryptocurrency Cybersecurity researchers have identified infrastructure links between the North Korean threat actors behind the fraudulent IT worker schemes and a 2016 crowdfunding scam. The new evidence suggests that Pyongyang-based threamoret groups may have pulled off illicit money-making scams that predate the use of IT workers, SecureWorks Counter Threat…
FBI Deletes PlugX Malware from 4,250 Hacked Computers in Multi-Month Operation
[ad_1] Jan 15, 2025Ravie LakshmananMalware / Threat Intelligence The U.S. Department of Justice (DoJ) on Tuesday disclosed that a court-authorized operation allowed the Federal Bureau of Investigation (FBI) to delete PlugX malware from over 4,250 infected computers as part of a “multi-month law enforcement operation.” PlugX, also known as Korplug, is a remote access trojan…