[ad_1] Jan 14, 2025Ravie LakshmananEndpoint Security / Vulnerability Microsoft has shed light on a now-patched security flaw impacting Apple macOS that, if successfully exploited, could have allowed an attacker running as “root” to bypass the operating system’s System Integrity Protection (SIP) and install malicious kernel drivers by loading third-party kernel extensions. The vulnerability in question…
Month: January 2025
4 Reasons Your SaaS Attack Surface Can No Longer be Ignored
[ad_1] What do identity risks, data security risks and third-party risks all have in common? They are all made much worse by SaaS sprawl. Every new SaaS account adds a new identity to secure, a new place where sensitive data can end up, and a new source of third party risk. Learn how you can…
CISA Adds Second BeyondTrust Flaw to KEV Catalog Amid Active Attacks
[ad_1] Jan 14, 2025Ravie LakshmananVulnerability / Cybersecurity The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added a second security flaw impacting BeyondTrust Privileged Remote Access (PRA) and Remote Support (RS) products to the Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. The vulnerability in question is CVE-2024-12686 (CVSS…
Top Cybersecurity Threats, Tools and Tips [13 January]
[ad_1] Jan 13, 2025Ravie Lakshmanan The cyber world’s been buzzing this week, and it’s all about staying ahead of the bad guys. From sneaky software bugs to advanced hacking tricks, the risks are real, but so are the ways to protect yourself. In this recap, we’ll break down what’s happening, why it matters, and what…
Hackers Exploit Aviatrix Controller Vulnerability to Deploy Backdoors and Crypto Miners
[ad_1] Jan 13, 2025Ravie LakshmananVulnerability / Cloud Security A recently disclosed critical security flaw impacting the Aviatrix Controller cloud networking platform has come under active exploitation in the wild to deploy backdoors and cryptocurrency miners. Cloud security firm Wiz said it’s currently responding to “multiple incidents” involving the weaponization of CVE-2024-50603 (CVSS score: 10.0), a…
WordPress Skimmers Evade Detection by Injecting Themselves into Database Tables
[ad_1] Cybersecurity researchers are warning of a new stealthy credit card skimmer campaign that targets WordPress e-commerce checkout pages by inserting malicious JavaScript code into a database table associated with the content management system (CMS). “This credit card skimmer malware targeting WordPress websites silently injects malicious JavaScript into database entries to steal sensitive payment details,”…
CrowdStrike Warns of Phishing Scam Targeting Job Seekers with XMRig Cryptominer
[ad_1] Jan 10, 2025Ravie LakshmananCryptomining / Malware Cybersecurity company CrowdStrike is alerting of a phishing campaign that exploits its own branding to distribute a cryptocurrency miner that’s disguised as an employee CRM application as part of a supposed recruitment process. “The attack begins with a phishing email impersonating CrowdStrike recruitment, directing recipients to a malicious…
RedDelta Deploys PlugX Malware to Target Mongolia and Taiwan in Espionage Campaigns
[ad_1] Jan 10, 2025Ravie LakshmananCyber Espionage / Cyber Attack Mongolia, Taiwan, Myanmar, Vietnam, and Cambodia have been targeted by the China-nexus RedDelta threat actor to deliver a customized version of the PlugX backdoor between July 2023 and December 2024. “The group used lure documents themed around the 2024 Taiwanese presidential candidate Terry Gou, the Vietnamese…
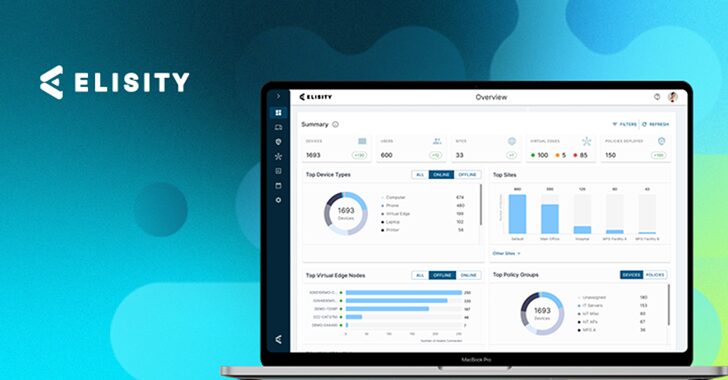
Microsegmentation For all Users, Workloads and Devices by Elisity
[ad_1] Network segmentation remains a critical security requirement, yet organizations struggle with traditional approaches that demand extensive hardware investments, complex policy management, and disruptive network changes. Healthcare and manufacturing sectors face particular challenges as they integrate diverse endpoints – from legacy medical devices to IoT sensors – onto their production networks. These devices often lack…
AI-Driven Ransomware FunkSec Targets 85 Victims Using Double Extortion Tactics
[ad_1] Cybersecurity researchers have shed light on a nascent artificial intelligence (AI) assisted ransomware family called FunkSec that sprang forth in late 2024, and has claimed more than 85 victims to date. “The group uses double extortion tactics, combining data theft with encryption to pressure victims into paying ransoms,” Check Point Research said in a…