[ad_1] Jan 04, 2025Ravie LakshmananMalware / VPN Security Cybersecurity researchers have flagged a new malware called PLAYFULGHOST that comes with a wide range of information-gathering features like keylogging, screen capture, audio capture, remote shell, and file transfer/execution. The backdoor, according to Google’s Managed Defense team, shares functional overlaps with a known remote administration tool referred…
Month: January 2025
Update Old .NET Domains Before January 7, 2025 to Avoid Service Disruption
[ad_1] Jan 03, 2025Ravie LakshmananDevOps / Software Development Microsoft has announced that it’s making an “unexpected change” to the way .NET installers and archives are distributed, requiring developers to update their production and DevOps infrastructure. “We expect that most users will not be directly affected, however, it is critical that you validate if you are…
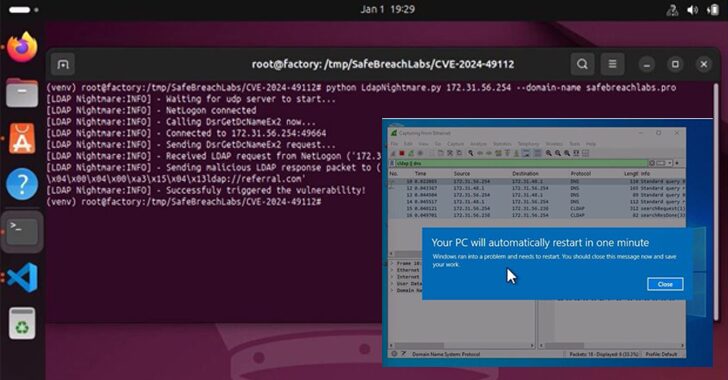
LDAPNightmare PoC Exploit Crashes LSASS and Reboots Windows Domain Controllers
[ad_1] Jan 03, 2025Ravie LakshmananWindows Server / Threat Mitigation A proof-of-concept (PoC) exploit has been released for a now-patched security flaw impacting Windows Lightweight Directory Access Protocol (LDAP) that could trigger a denial-of-service (DoS) condition. The out-of-bounds reads vulnerability is tracked as CVE-2024-49113 (CVSS score: 7.5). It was addressed by Microsoft as part of Patch…
New AI Jailbreak Method ‘Bad Likert Judge’ Boosts Attack Success Rates by Over 60%
[ad_1] Jan 03, 2025Ravie LakshmananMachine Learning / Vulnerability Cybersecurity researchers have shed light on a new jailbreak technique that could be used to get past a large language model’s (LLM) safety guardrails and produce potentially harmful or malicious responses. The multi-turn (aka many-shot) attack strategy has been codenamed Bad Likert Judge by Palo Alto Networks…
Apple to Pay Siri Users $20 Per Device in Settlement Over Accidental Siri Privacy Violations
[ad_1] Jan 03, 2025Ravie LakshmananTechnology / Data Privacy Apple has agreed to pay $95 million to settle a proposed class action lawsuit that accused the iPhone maker of invading users’ privacy using its voice-activated Siri assistant. The development was first reported by Reuters. The settlement applies to U.S.-based individuals current or former owners or purchasers…
A Growing Threat to Modern Security and How to Combat Them
[ad_1] Jan 02, 2025The Hacker NewsCloud Security / Threat Intelligence In the past year, cross-domain attacks have gained prominence as an emerging tactic among adversaries. These operations exploit weak points across multiple domains – including endpoints, identity systems and cloud environments – so the adversary can infiltrate organizations, move laterally and evade detection. eCrime groups…
Severe Security Flaws Patched in Microsoft Dynamics 365 and Power Apps Web API
[ad_1] Jan 02, 2025Ravie LakshmananVulnerability / Data Protection Details have emerged about three now-patched security vulnerabilities in Dynamics 365 and Power Apps Web API that could result in data exposure. The flaws, discovered by Melbourne-based cybersecurity company Stratus Security, have been addressed as of May 2024. Two of the three shortcomings reside in Power Platform’s…
Takeaways from the Campaign Targeting Browser Extensions
[ad_1] Dec 30, 2024The Hacker NewsBrowser Security / GenAI Security News has been making headlines over the weekend of the extensive attack campaign targeting browser extensions and injecting them with malicious code to steal user credentials. Currently, over 25 extensions, with an install base of over two million users, have been found to be compromised,…
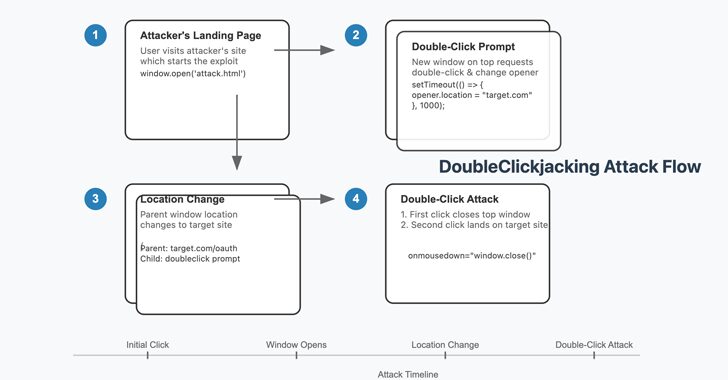
New “DoubleClickjacking” Exploit Bypasses Clickjacking Protections on Major Websites
[ad_1] Jan 01, 2025Ravie LakshmananWeb Security / Vulnerability Threat hunters have disclosed a new “widespread timing-based vulnerability class” that leverages a double-click sequence to facilitate clickjacking attacks and account takeovers in almost all major websites. The technique has been codenamed DoubleClickjacking by security researcher Paulos Yibelo. “Instead of relying on a single click, it takes…
Iranian and Russian Entities Sanctioned for Election Interference Using AI and Cyber Tactics
[ad_1] Jan 01, 2025Ravie LakshmananGenerative AI / Election Interference The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) on Tuesday leveled sanctions against two entities in Iran and Russia for their attempts to interfere with the November 2024 presidential election. The federal agency said the entities – a subordinate organization of Iran’s Islamic Revolutionary…