[ad_1] The Open Web Application Security Project has recently introduced a new Top 10 project – the Non-Human Identity (NHI) Top 10. For years, OWASP has provided security professionals and developers with essential guidance and actionable frameworks through its Top 10 projects, including the widely used API and Web Application security lists. Non-human identity security…
Month: January 2025
GamaCopy Mimics Gamaredon Tactics in Cyber Espionage Targeting Russian Entities
[ad_1] Jan 27, 2025Ravie LakshmananCyber Espionage / Threat Intelligence A previously unknown threat actor has been observed copying the tradecraft associated with the Kremlin-aligned Gamaredon hacking group in its cyber attacks targeting Russian-speaking entities. The campaign has been attributed to a threat cluster dubbed GamaCopy, which is assessed to share overlaps with another hacking group…
MintsLoader Delivers StealC Malware and BOINC in Targeted Cyber Attacks
[ad_1] Jan 27, 2025Ravie LakshmananMalware / SEO Poisoning Threat hunters have detailed an ongoing campaign that leverages a malware loader called MintsLoader to distribute secondary payloads such as the StealC information stealer and a legitimate open-source network computing platform called BOINC. “MintsLoader is a PowerShell based malware loader that has been seen delivered via spam…
Meta’s Llama Framework Flaw Exposes AI Systems to Remote Code Execution Risks
[ad_1] A high-severity security flaw has been disclosed in Meta’s Llama large language model (LLM) framework that, if successfully exploited, could allow an attacker to execute arbitrary code on the llama-stack inference server. The vulnerability, tracked as CVE-2024-50050, has been assigned a CVSS score of 6.3 out of 10.0. Supply chain security firm Snyk, on…
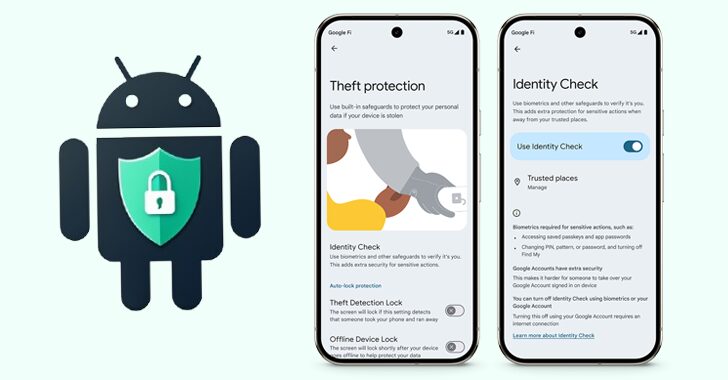
Android’s New Identity Check Feature Locks Device Settings Outside Trusted Locations
[ad_1] Jan 24, 2025Ravie LakshmananBiometric / Mobile Security Google has launched a new feature called Identity Check for supported Android devices that locks sensitive settings behind biometric authentication when outside of trusted locations. “When you turn on Identity Check, your device will require explicit biometric authentication to access certain sensitive resources when you’re outside of…
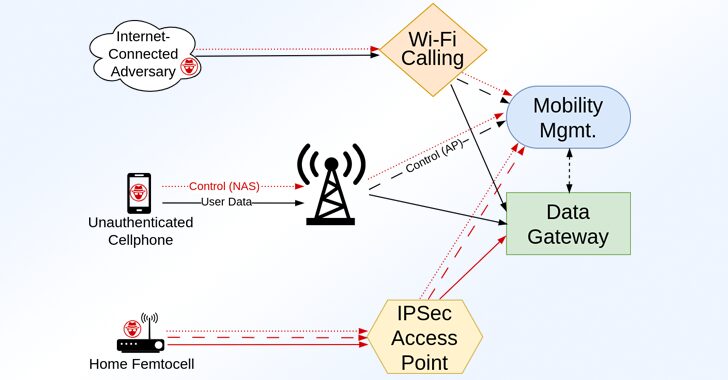
Over 100 Security Flaws Found in LTE and 5G Network Implementations
[ad_1] Jan 24, 2025Ravie LakshmananTelecom Security / Vulnerability A group of academics has disclosed details of over 100 security vulnerabilities impacting LTE and 5G implementations that could be exploited by an attacker to disrupt access to service and even gain a foothold into the cellular core network. The 119 vulnerabilities, assigned 97 unique CVE identifiers,…
2025 State of SaaS Backup and Recovery Report
[ad_1] The modern workplace has undergone a seismic transformation over recent years, with hybrid work becoming the norm and businesses rapidly adopting cloud-based Software-as-a-Service (SaaS) applications to facilitate it. SaaS applications like Microsoft 365 and Google Workspace have now become the backbone of business operations, enabling seamless collaboration and productivity. However, this dependence on SaaS…
DoJ Indicts 5 Individuals for $866K North Korean IT Worker Scheme Violations
[ad_1] The U.S. Department of Justice (DoJ) on Thursday indicted two North Korean nationals, a Mexican national, and two of its own citizens for their alleged involvement in the ongoing fraudulent information technology (IT) worker scheme that seeks to generate revenue for the Democratic People’s Republic of Korea (DPRK) in violation of international sanctions. The…
How Satori Secures Sensitive Data From Production to AI
[ad_1] Every week seems to bring news of another data breach, and it’s no surprise why: securing sensitive data has become harder than ever. And it’s not just because companies are dealing with orders of magnitude more data. Data flows and user roles are constantly shifting, and data is stored across multiple technologies and cloud…
CISA Adds Five-Year-Old jQuery XSS Flaw to Exploited Vulnerabilities List
[ad_1] Jan 24, 2025Ravie LakshmananVulnerability / JavaScript The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday placed a now-patched security flaw impacting the popular jQuery JavaScript library to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The medium-severity vulnerability is CVE-2020-11023 (CVSS score: 6.1/6.9), a nearly five-year-old cross-site scripting (XSS)…