[ad_1] Jan 20, 2025Ravie Lakshmanan As the digital world becomes more complicated, the lines between national security and cybersecurity are starting to fade. Recent cyber sanctions and intelligence moves show a reality where malware and fake news are used as tools in global politics. Every cyberattack now seems to have deeper political consequences. Governments are…
Month: January 2025
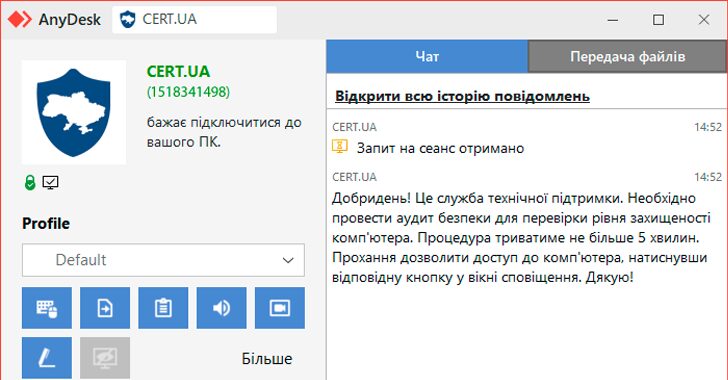
CERT-UA Warns of Cyber Scams Using Fake AnyDesk Requests for Fraudulent Security Audits
bj Kailee [ad_1] Jan 21, 2025Ravie LakshmananMalware / Cyber Threat The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of ongoing attempts by unknown threat actors to impersonate the cybersecurity agency by sending AnyDesk connection requests. The AnyDesk requests claim to be for conducting an audit to assess the “level of security,” CERT-UA added,…
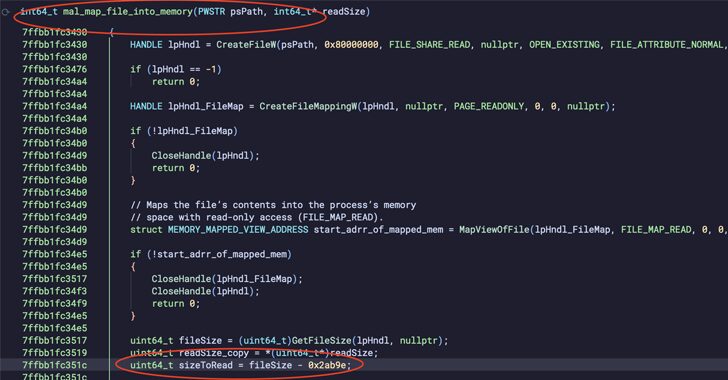
PNGPlug Loader Delivers ValleyRAT Malware Through Fake Software Installers
[ad_1] Jan 21, 2025Ravie LakshmananCyber Attack / Windows Security Cybersecurity researchers are calling attention to a series of cyber attacks that have targeted Chinese-speaking regions like Hong Kong, Taiwan, and Mainland China with a known malware called ValleyRAT. The attacks leverage a multi-stage loader dubbed PNGPlug to deliver the ValleyRAT payload, Intezer said in a…
Ex-CIA Analyst Pleads Guilty to Sharing Top-Secret Data with Unauthorized Parties
[ad_1] A former analyst working for the U.S. Central Intelligence Agency (CIA) pleaded guilty to transmitting top secret National Defense Information (NDI) to individuals who did not have the necessary authorization to receive it and attempted to cover up the activity. Asif William Rahman, 34, of Vienna, was an employee of the CIA since 2016…
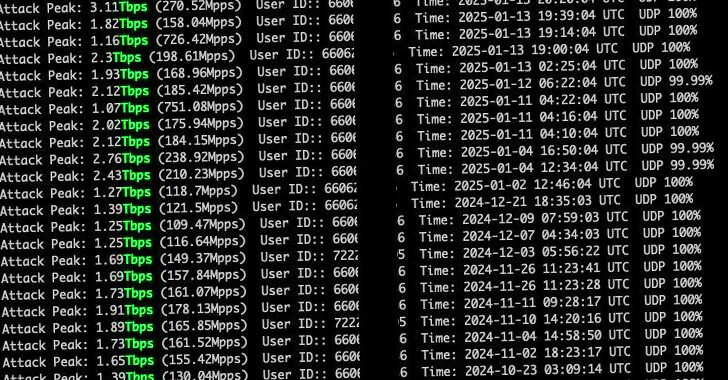
Mirai Botnet Launches Record 5.6 Tbps DDoS Attack with 13,000+ IoT Devices
[ad_1] Jan 22, 2025Ravie LakshmananBotnet / Network Security Web infrastructure and security company Cloudflare on Tuesday said it detected and blocked a 5.6 Terabit per second (Tbps) distributed denial-of-service (DDoS) attack, the largest ever attack to be reported to date. The UDP protocol-based attack took place on October 29, 2024, targeting one of its customers,…
Oracle Releases January 2025 Patch to Address 318 Flaws Across Major Products
[ad_1] Jan 22, 2025Ravie LakshmananVulnerability / Enterprise Security Oracle is urging customers to apply its January 2025 Critical Patch Update (CPU) to address 318 new security vulnerabilities spanning its products and services. The most severe of the flaws is a bug in the Oracle Agile Product Lifecycle Management (PLM) Framework (CVE-2025-21556, CVSS score: 9.9) that…
Custom Backdoor Exploiting Magic Packet Vulnerability in Juniper Routers
[ad_1] Jan 23, 2025Ravie LakshmananMalware / Enterprise Security Enterprise-grade Juniper Networks routers have become the target of a custom backdoor as part of a campaign dubbed J-magic. According to the Black Lotus Labs team at Lumen Technologies, the activity is so named for the fact that the backdoor continuously monitors for a “magic packet” sent…
The State of Web Exposure 2025
[ad_1] Are your websites leaking sensitive data? New research reveals that 45% of third-party apps access user info without proper authorization, and 53% of risk exposures in Retail are due to the excessive use of tracking tools. Learn how to uncover and mitigate these hidden threats and risks—download the full report here. New research by…
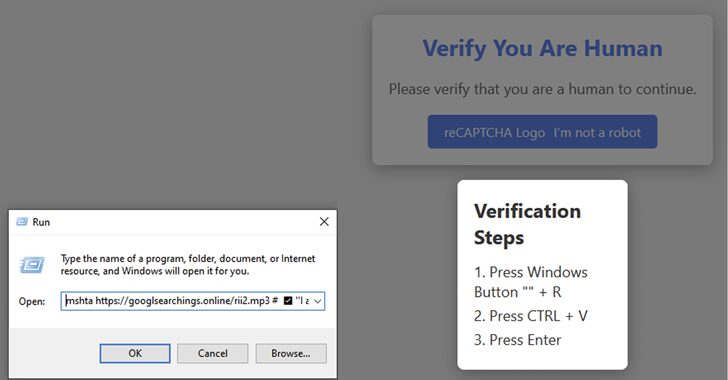
Fake CAPTCHA Campaign Spreads Lumma Stealer in Multi-Industry Attacks
[ad_1] Jan 23, 2025Ravie LakshmananPhishing / Malware Cybersecurity researchers are calling attention to a new malware campaign that leverages fake CAPTCHA verification checks to deliver the infamous Lumma information stealer. “The campaign is global, with Netskope Threat Labs tracking victims targeted in Argentina, Colombia, the United States, the Philippines, and other countries around the world,”…
Palo Alto Firewalls Found Vulnerable to Secure Boot Bypass and Firmware Exploits
[ad_1] Jan 23, 2025Ravie LakshmananFirmware Security / Vulnerability An exhaustive evaluation of three firewall models from Palo Alto Networks has uncovered a host of known security flaws impacting the devices’ firmware as well as misconfigured security features. “These weren’t obscure, corner-case vulnerabilities,” security vendor Eclypsium said in a report shared with The Hacker News. “Instead…