[ad_1] Jan 22, 2025The Hacker NewsRisk Assessment / Browser Security As GenAI tools and SaaS platforms become a staple component in the employee toolkit, the risks associated with data exposure, identity vulnerabilities, and unmonitored browsing behavior have skyrocketed. Forward-thinking security teams are looking for security controls and strategies to address these risks, but they do…
Month: January 2025
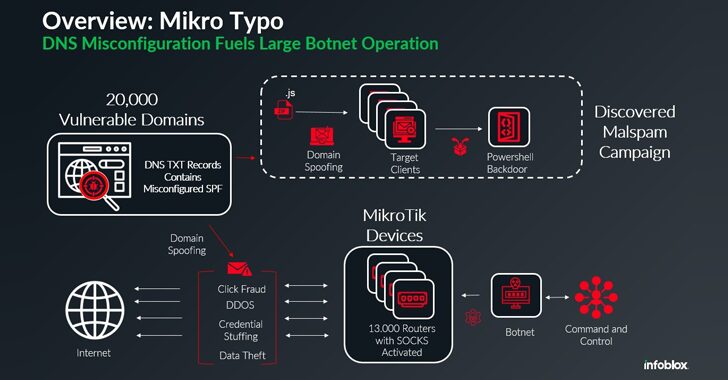
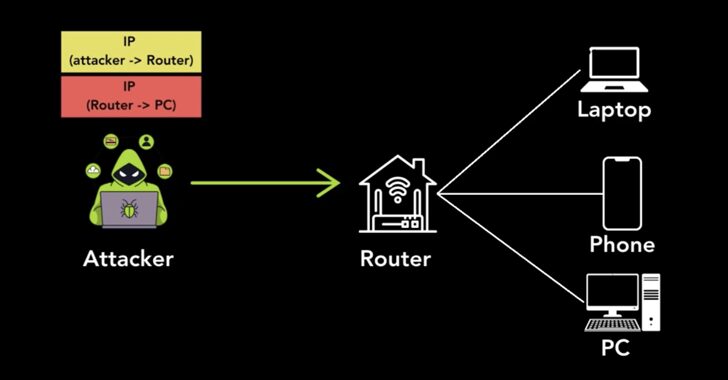
13,000 MikroTik Routers Hijacked by Botnet for Malspam and Cyberattacks
[ad_1] Jan 21, 2025Ravie LakshmananEmail Security / Botnet A global network of about 13,000 hijacked Mikrotik routers has been employed as a botnet to propagate malware via spam campaigns, the latest addition to a list of botnets powered by MikroTik devices. The activity “take[s] advantage of misconfigured DNS records to pass email protection techniques,” Infoblox…
Mirai Variant Murdoc Botnet Exploits AVTECH IP Cameras and Huawei Routers
[ad_1] Jan 21, 2025Ravie LakshmananBotnet / Vulnerability Cybersecurity researchers have warned of a new large-scale campaign that exploits security flaws in AVTECH IP cameras and Huawei HG532 routers to rope the devices into a Mirai botnet variant dubbed Murdoc Botnet. The ongoing activity “demonstrates enhanced capabilities, exploiting vulnerabilities to compromise devices and establish expansive botnet…
Setting New Standards for Visibility and Control in Penetration Testing Projects
[ad_1] Imagine receiving a penetration test report that leaves you with more questions than answers. Questions like, “Were all functionalities of the web app tested?” or ” Were there any security issues that could have been identified during testing?” often go unresolved, raising concerns about the thoroughness of the security testing. This frustration is common…
DoNot Team Linked to New Tanzeem Android Malware Targeting Intelligence Collection
[ad_1] Jan 20, 2025Ravie LakshmananAndroid / Malware The Threat actor known as DoNot Team has been linked to a new Android malware as part of highly targeted cyber attacks. The artifacts in question, named Tanzeem (meaning “organization” in Urdu) and Tanzeem Update, were spotted in October and December 2024 by cybersecurity company Cyfirma. The apps…
Unsecured Tunneling Protocols Expose 4.2 Million Hosts, Including VPNs and Routers
[ad_1] Jan 20, 2025Ravie LakshmananNetwork Security / Vulnerability New research has uncovered security vulnerabilities in multiple tunneling protocols that could allow attackers to perform a wide range of attacks. “Internet hosts that accept tunneling packets without verifying the sender’s identity can be hijacked to perform anonymous attacks and provide access to their networks,” Top10VPN said…
Hackers Deploy Malicious npm Packages to Steal Solana Wallet Keys via Gmail SMTP
[ad_1] Jan 20, 2025Ravie LakshmananSupply Chain Attack / Solana Cybersecurity researchers have identified three sets of malicious packages across the npm and Python Package Index (PyPI) repository that come with capabilities to steal data and even delete sensitive data from infected systems. The list of identified packages is below – @async-mutex/mutex, a typosquat of async-mute…
Critical RCE Flaw in GFI KerioControl Allows Remote Code Execution via CRLF Injection
[ad_1] Jan 09, 2025Ravie LakshmananVulnerability / Threat Intelligence Threat actors are attempting to take advantage of a recently disclosed security flaw impacting GFI KerioControl firewalls that, if successfully exploited, could allow malicious actors to achieve remote code execution (RCE). The vulnerability in question, CVE-2024-52875, refers to a carriage return line feed (CRLF) injection attack, paving…
TikTok Goes Dark in the U.S. as Federal Ban Takes Effect January 19, 2025
[ad_1] Jan 19, 2025Ravie LakshmananSocial Media / Data Privacy Popular video-sharing social network TikTok has officially gone dark in the United States, 2025, as a federal ban on the app comes into effect on January 19, 2025. “We regret that a U.S. law banning TikTok will take effect on January 19 and force us to…
MirrorFace Leverages ANEL and NOOPDOOR in Multi-Year Cyberattacks on Japan
[ad_1] Jan 09, 2025Ravie LakshmananCybersecurity / Malware Japan’s National Police Agency (NPA) and National Center of Incident Readiness and Strategy for Cybersecurity (NCSC) accused a China-linked threat actor named MirrorFace of orchestrating a persistent attack campaign targeting organizations, businesses, and individuals in the country since 2019. The primary objective of the attack campaign is to…