[ad_1] Jan 09, 2025The Hacker NewsData Protection / Encryption Ransomware isn’t slowing down—it’s getting smarter. Encryption, designed to keep our online lives secure, is now being weaponized by cybercriminals to hide malware, steal data, and avoid detection. The result? A 10.3% surge in encrypted attacks over the past year and some of the most shocking…
Month: January 2025
U.S. Sanctions Chinese Cybersecurity Firm Over Treasury Hack Tied to Silk Typhoon
[ad_1] The U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) has imposed sanctions against a Chinese cybersecurity company and a Shanghai-based cyber actor for their alleged links to the Salt Typhoon group and the recent compromise of the federal agency. “People’s Republic of China-linked (PRC) malicious cyber actors continue to target U.S. government systems,…
Expired Domains Allowed Control Over 4,000 Backdoors on Compromised Systems
[ad_1] Jan 13, 2025Ravie LakshmananMalware / Domain Security No less than 4,000 unique web backdoors previously deployed by various threat actors have been hijacked by taking control of abandoned and expired infrastructure for as little as $20 per domain. Cybersecurity company watchTowr Labs said it pulled off the operation by registering over 40 domain names…
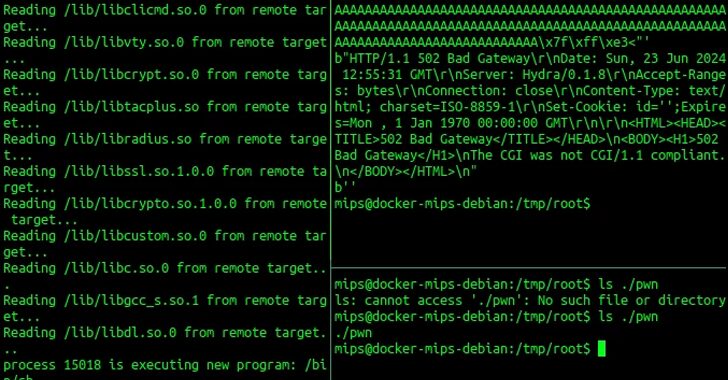
The Mechanization of Virtualized Attacks
[ad_1] Jan 13, 2025The Hacker NewsThreat Detection / Network Security In 2024, ransomware attacks targeting VMware ESXi servers reached alarming levels, with the average ransom demand skyrocketing to $5 million. With approximately 8,000 ESXi hosts exposed directly to the internet (according to Shodan), the operational and business impact of these attacks is profound. Most of…
Russian-Linked Hackers Target Kazakhstan in Espionage Campaign with HATVIBE Malware
[ad_1] Russia-linked threat actors have been attributed to an ongoing cyber espionage campaign targeting Kazakhstan as part of the Kremlin’s efforts to gather economic and political intelligence in Central Asia. The campaign has been assessed to be the work of an intrusion set dubbed UAC-0063, which likely shares overlap with APT28, a nation-state group affiliated…
Fortinet Warns of New Zero-Day Used in Attacks on Firewalls with Exposed Interfaces
[ad_1] Threat hunters are calling attention to a new campaign that has targeted Fortinet FortiGate firewall devices with management interfaces exposed on the public internet. “The campaign involved unauthorized administrative logins on management interfaces of firewalls, creation of new accounts, SSL VPN authentication through those accounts, and various other configuration changes,” cybersecurity firm Arctic Wolf…
Illicit HuiOne Telegram Market Surpasses Hydra, Hits $24 Billion in Crypto Transactions
[ad_1] Jan 14, 2025Ravie LakshmananCryptocurrency / Online Scam The Telegram-based online marketplace known as HuiOne Guarantee and its vendors have cumulatively received at least $24 billion in cryptocurrency, dwarfing the now-defunct Hydra to become the largest online illicit marketplace to have ever operated. The figures, released by blockchain analytics firm Elliptic, show that monthly inflows…
New ‘Sneaky 2FA’ Phishing Kit Targets Microsoft 365 Accounts with 2FA Code Bypass
[ad_1] Jan 17, 2025Ravie LakshmananCybersecurity / Threat Intelligence Cybersecurity researchers have detailed a new adversary-in-the-middle (AitM) phishing kit that’s capable of Microsoft 365 accounts with an aim to steal credentials and two-factor authentication (2FA) codes since at least October 2024. The nascent phishing kit has been dubbed Sneaky 2FA by French cybersecurity company Sekoia, which…
Python-Based Bots Exploiting PHP Servers Fuel Gambling Platform Proliferation
[ad_1] Jan 17, 2025Ravie LakshmananWeb Security / Botnet Cybersecurity researchers have exposed a new campaign that targets web servers running PHP-based applications to promote gambling platforms in Indonesia. “Over the past two months, a significant volume of attacks from Python-based bots has been observed, suggesting a coordinated effort to exploit thousands of web apps,” Imperva…
Critical Flaws in WGS-804HPT Switches Enable RCE and Network Exploitation
[ad_1] Jan 17, 2025Ravie LakshmananFirmware Security / Vulnerability Cybersecurity researchers have disclosed three security flaws in Planet Technology’s WGS-804HPT industrial switches that could be chained to achieve pre-authentication remote code execution on susceptible devices. “These switches are widely used in building and home automation systems for a variety of networking applications,” Claroty’s Tomer Goldschmidt said…