[ad_1] Feb 28, 2025Ravie LakshmananFinancial Fraud / Cyber Espionage The threat actor known as Sticky Werewolf has been linked to targeted attacks primarily in Russia and Belarus with the aim of delivering the Lumma Stealer malware by means of a previously undocumented implant. Cybersecurity company Kaspersky is tracking the activity under the name Angry Likho,…
Month: February 2025
Fake CAPTCHA PDFs Spread Lumma Stealer via Webflow, GoDaddy, and Other Domains
[ad_1] Cybersecurity researchers have uncovered a widespread phishing campaign that uses fake CAPTCHA images shared via PDF documents hosted on Webflow’s content delivery network (CDN) to deliver the Lumma stealer malware. Netskope Threat Labs said it discovered 260 unique domains hosting 5,000 phishing PDF files that redirect victims to malicious websites. “The attacker uses SEO…
Amnesty Finds Cellebrite’s Zero-Day Used to Unlock Serbian Activist’s Android Phone
[ad_1] Feb 28, 2025Ravie LakshmananMobile Security / Zero-Day A 23-year-old Serbian youth activist had their Android phone targeted by a zero-day exploit developed by Cellebrite to unlock the device, according to a new report from Amnesty International. “The Android phone of one student protester was exploited and unlocked by a sophisticated zero-day exploit chain targeting…
a Double-Edged Sword for IT Teams – Essential Yet Exploitable
[ad_1] Remote Desktop Protocol (RDP) is an amazing technology developed by Microsoft that lets you access and control another computer over a network. It’s like having your office computer with you wherever you go. For businesses, this means IT staff can manage systems remotely, and employees can work from home or anywhere, making RDP a…
Microsoft Exposes LLMjacking Cybercriminals Behind Azure AI Abuse Scheme
[ad_1] Feb 28, 2025Ravie LakshmananAPI Security / AI Security Microsoft on Thursday unmasked four of the individuals that it said were behind an Azure Abuse Enterprise scheme that involves leveraging unauthorized access to generative artificial intelligence (GenAI) services in order to produce offensive and harmful content. The campaign, called LLMjacking, has targeted various AI offerings,…
12,000+ API Keys and Passwords Found in Public Datasets Used for LLM Training
[ad_1] A dataset used to train large language models (LLMs) has been found to contain nearly 12,000 live secrets, which allow for successful authentication. The findings once again highlight how hard-coded credentials pose a severe security risk to users and organizations alike, not to mention compounding the problem when LLMs end up suggesting insecure coding…
New TgToxic Banking Trojan Variant Evolves with Anti-Analysis Upgrades
[ad_1] Feb 27, 2025Ravie LakshmananCybercrime / Android Cybersecurity researchers have discovered an updated version of an Android malware called TgToxic (aka ToxicPanda), indicating that the threat actors behind it are continuously making changes in response to public reporting. “The modifications seen in the TgToxic payloads reflect the actors’ ongoing surveillance of open source intelligence and…
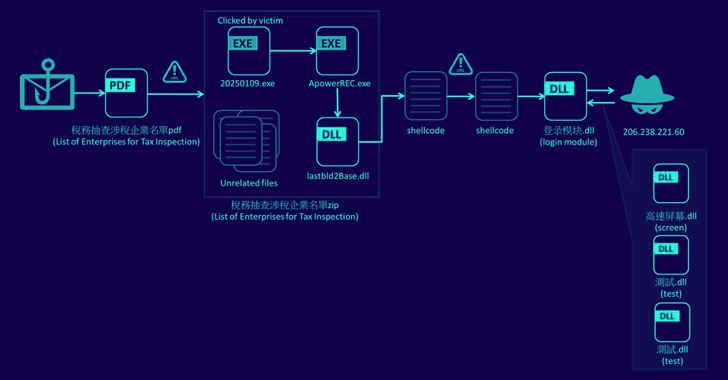
Silver Fox APT Uses Winos 4.0 Malware in Cyber Attacks Against Taiwanese Organizations
[ad_1] Feb 27, 2025Ravie LakshmananMalware / Threat Intelligence A new campaign is targeting companies in Taiwan with malware known as Winos 4.0 as part of phishing emails masquerading as the country’s National Taxation Bureau. The campaign, detected last month by Fortinet FortiGuard Labs, marks a departure from previous attack chains that have leveraged malicious game-related…
89% of Enterprise GenAI Usage Is Invisible to Organizations Exposing Critical Security Risks, New Report Reveals
[ad_1] Feb 27, 2025The Hacker NewsArtificial Intelligence / Browser Security Organizations are either already adopting GenAI solutions, evaluating strategies for integrating these tools into their business plans, or both. To drive informed decision-making and effective planning, the availability of hard data is essential—yet such data remains surprisingly scarce. The “Enterprise GenAI Data Security Report 2025”…
Space Pirates Targets Russian IT Firms With New LuckyStrike Agent Malware
[ad_1] Feb 27, 2025Ravie LakshmananMalware / Network Security The threat actor known as Space Pirates has been linked to a malicious campaign targeting Russian information technology (IT) organizations with a previously undocumented malware called LuckyStrike Agent. The activity was detected in November 2024 by Solar, the cybersecurity arm of Russian state-owned telecom company Rostelecom. It’s…