[ad_1] Attack surfaces are growing faster than security teams can keep up – to stay ahead, you need to know what’s exposed and where attackers are most likely to strike. With cloud adoption dramatically increasing the ease of exposing new systems and services to the internet, prioritizing threats and managing your attack surface from an…
Month: February 2025
Now Targets 1,030 Sites and 73 Financial Institutions
[ad_1] Feb 03, 2025Ravie LakshmananFinancial Security / Malware Brazilian Windows users are the target of a campaign that delivers a banking malware known as Coyote. “Once deployed, the Coyote Banking Trojan can carry out various malicious activities, including keylogging, capturing screenshots, and displaying phishing overlays to steal sensitive credentials,” Fortinet FortiGuard Labs researcher Cara Lin…
Top Cybersecurity Threats, Tools and Tips [27 February]
[ad_1] Feb 03, 2025Ravie LakshmananCybersecurity / Recap This week, our news radar shows that every new tech idea comes with its own challenges. A hot AI tool is under close watch, law enforcement is shutting down online spots that help cybercriminals, and teams are busy fixing software bugs that could let attackers in. From better…
PyPI Introduces Archival Status to Alert Users About Unmaintained Python Packages
[ad_1] Feb 03, 2025Ravie LakshmananOpen Source / Software Security The maintainers of the Python Package Index (PyPI) registry have announced a new feature that allows package developers to archive a project as part of efforts to improve supply chain security. “Maintainers can now archive a project to let users know that the project is not…
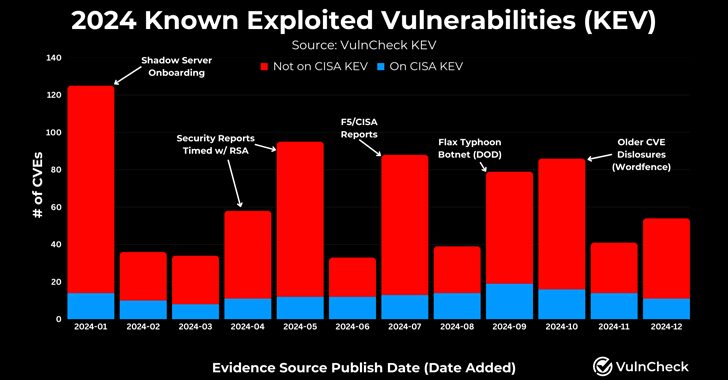
768 CVEs Exploited in 2024, Reflecting a 20% Increase from 639 in 2023
[ad_1] Feb 03, 2025Ravie LakshmananVulnerability / Network Security As many as 768 vulnerabilities with designated CVE identifiers were reported as exploited in the wild in 2024, up from 639 CVEs in 2023, registering a 20% increase year-over-year. Describing 2024 as “another banner year for threat actors targeting the exploitation of vulnerabilities,” VulnCheck said 23.6% of…
Crazy Evil Gang Targets Crypto with StealC, AMOS, and Angel Drainer Malware
[ad_1] A Russian-speaking cybercrime gang known as Crazy Evil has been linked to over 10 active social media scams that leverage a wide range of tailored lures to deceive victims and trick them into installing malware such as StealC, Atomic macOS Stealer (aka AMOS), and Angel Drainer. “Specializing in identity fraud, cryptocurrency theft, and information-stealing…
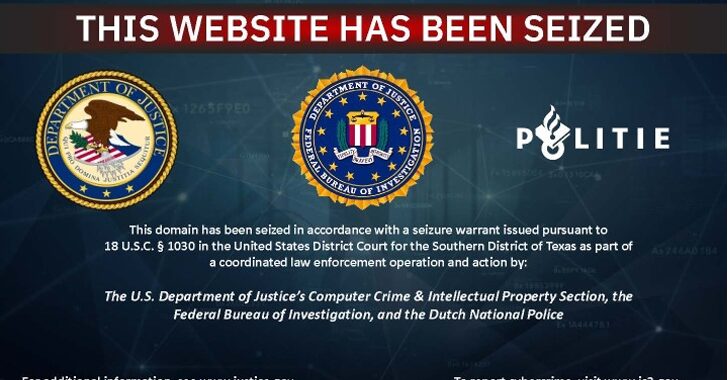
U.S. and Dutch Authorities Dismantle 39 Domains Linked to BEC Fraud Network
[ad_1] Feb 01, 2025Ravie LakshmananCybercrime / Fraud Prevention U.S. and Dutch law enforcement agencies have announced that they have dismantled 39 domains and their associated servers as part of efforts to disrupt a network of online marketplaces originating from Pakistan. The action, which took place on January 29, 2025, has been codenamed Operation Heart Blocker….
BeyondTrust Zero-Day Breach Exposed 17 SaaS Customers via Compromised API Key
[ad_1] Feb 01, 2025Ravie LakshmananVulnerability / Zero-Day BeyondTrust has revealed it completed an investigation into a recent cybersecurity incident that targeted some of the company’s Remote Support SaaS instances by making use of a compromised API key. The company said the breach involved 17 Remote Support SaaS customers and that the API key was used…
Meta Confirms Zero-Click WhatsApp Spyware Attack Targeting 90 Journalists, Activists
[ad_1] Feb 01, 2025Ravie LakshmananPrivacy / Surveillance Meta-owned WhatsApp on Friday said it disrupted a campaign that involved the use of spyware to target journalists and civil society members. The campaign, which targeted around 90 members, involved the use of spyware from an Israeli company known as Paragon Solutions. The attackers were neutralized in December…
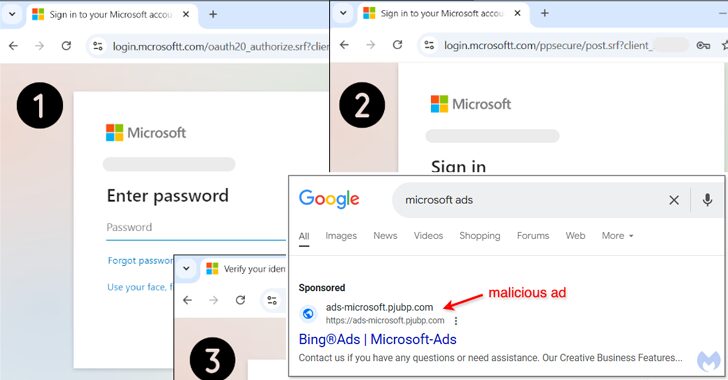
Malvertising Scam Uses Fake Google Ads to Hijack Microsoft Advertising Accounts
[ad_1] Feb 01, 2025Ravie LakshmananMalvertising / Mobile Security Cybersecurity researchers have discovered a malvertising campaign that’s targeting Microsoft advertisers with bogus Google ads that aim to take them to phishing pages that are capable of harvesting their credentials. “These malicious ads, appearing on Google Search, are designed to steal the login information of users trying…