[ad_1] Feb 24, 2025Ravie LakshmananCloud Security / Encryption Google Cloud has announced quantum-safe digital signatures in Google Cloud Key Management Service (Cloud KMS) for software-based keys as a way to bulletproof encryption systems against the threat posed by cryptographically-relevant quantum computers. The feature, currently in preview, coexists with the National Institute of Standards and Technology’s…
Month: February 2025
From $1.5B Crypto Heist to AI Misuse & Apple’s Data Dilemma
[ad_1] Feb 24, 2025Ravie Lakshmanan Welcome to your weekly roundup of cyber news, where every headline gives you a peek into the world of online battles. This week, we look at a huge crypto theft, reveal some sneaky AI scam tricks, and discuss big changes in data protection. Let these stories spark your interest and…
Bybit Confirms Record-Breaking $1.46 Billion Crypto Heist in Sophisticated Cold Wallet Attack
[ad_1] Feb 22, 2025Ravie LakshmananFinancial Crime / Cryptocurrency Cryptocurrency exchange Bybit on Friday revealed that a “sophisticated” attack led to the theft of over $1.46 billion worth of cryptocurrency from one of its Ethereum cold (offline) wallets, making it the largest ever single crypto heist in history. “The incident occurred when our ETH multisig cold…
OpenAI Bans Accounts Misusing ChatGPT for Surveillance and Influence Campaigns
[ad_1] Feb 22, 2025Ravie LakshmananDisinformation / Artificial Intelligence OpenAI on Friday revealed that it banned a set of accounts that used its ChatGPT tool to develop a suspected artificial intelligence (AI)-powered surveillance tool. The social media listening tool is said to likely originate from China and is powered by one of Meta’s Llama models, with…
CISA Flags Craft CMS Vulnerability CVE-2025-23209 Amid Active Attacks
[ad_1] Feb 21, 2025Ravie LakshmananWeb Security / Vulnerability A high-severity security flaw impacting the Craft content management system (CMS) has been added by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerability in question is CVE-2025-23209 (CVSS score: 8.1), which impacts…
Data Leak Exposes TopSec’s Role in China’s Censorship-as-a-Service Operations
[ad_1] Feb 21, 2025Ravie LakshmananSurveillance / Content Monitoring An analysis of a data leak from a Chinese cybersecurity company TopSec has revealed that it likely offers censorship-as-a-service solutions to prospective customers, including a state-owned enterprise in the country. Founded in 1995, TopSec ostensibly offers services such as Endpoint Detection and Response (EDR) and vulnerability scanning….
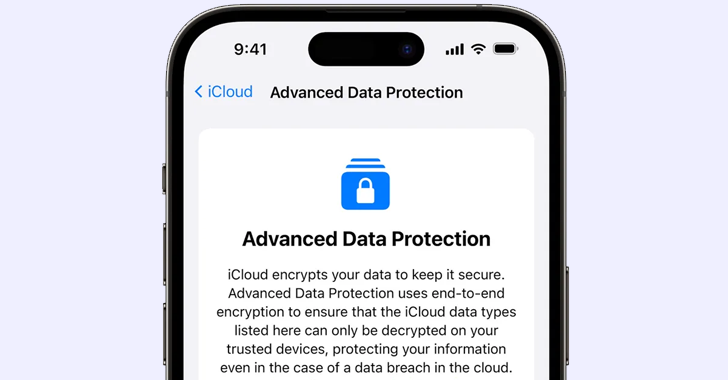
Apple Drops iCloud’s Advanced Data Protection in the U.K. Amid Encryption Backdoor Demands
[ad_1] Feb 21, 2025Ravie LakshmananData Protection / Encryption Apple is removing its Advanced Data Protection (ADP) feature for iCloud from the United Kingdom with immediate effect following government demands for backdoor access to encrypted user data. The development was first reported by Bloomberg. ADP for iCloud is an optional setting that ensures that users’ trusted…
AI-Powered Deception is a Menace to Our Societies
[ad_1] Wherever there’s been conflict in the world, propaganda has never been far away. Travel back in time to 515 BC and read the Behistun Inscription, an autobiography by Persian King Darius that discusses his rise to power. More recently, see how different newspapers report on wars, where it’s said, ‘The first casualty is the…
Cybercriminals Can Now Clone Any Brand’s Site in Minutes Using Darcula PhaaS v3
[ad_1] The threat actors behind the Darcula phishing-as-a-service (PhaaS) platform appear to be readying a new version that allows prospective customers and cyber crooks to clone any brand’s legitimate website and create a phishing version, further bringing down the technical expertise required to pull off phishing attacks at scale. The latest iteration of the phishing…
Learn How to Identify High-Risk Identity Gaps and Slash Security Debt in 2025
[ad_1] Feb 21, 2025The Hacker NewsIdentity Security / Threat Prevention In today’s rapidly evolving digital landscape, weak identity security isn’t just a flaw—it’s a major risk that can expose your business to breaches and costly downtime. Many organizations are overwhelmed by an excess of user identities and aging systems, making them vulnerable to attacks. Without…