[ad_1] The growing demand for cybersecurity and compliance services presents a great opportunity for Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs) to offer virtual Chief Information Security Officer (vCISO) services—delivering high-level cybersecurity leadership without the cost of a full-time hire. However, transitioning to vCISO services is not without its challenges. Many service…
Month: February 2025
New Snake Keylogger Variant Leverages AutoIt Scripting to Evade Detection
[ad_1] Feb 19, 2025The Hacker NewsMalware / Threat Intelligence A new variant of the Snake Keylogger malware is being used to actively target Windows users located in China, Turkey, Indonesia, Taiwan, and Spain. Fortinet FortiGuard Labs said the new version of the malware has been behind over 280 million blocked infection attempts worldwide since the…
CISA Adds Palo Alto Networks and SonicWall Flaws to Exploited Vulnerabilities List
[ad_1] Feb 19, 2025Ravie LakshmananThreat Intelligence / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added two security flaws impacting Palo Alto Networks PAN-OS and SonicWall SonicOS SSLVPN to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The flaws are listed below – CVE-2025-0108 (CVSS score: 7.8) –…
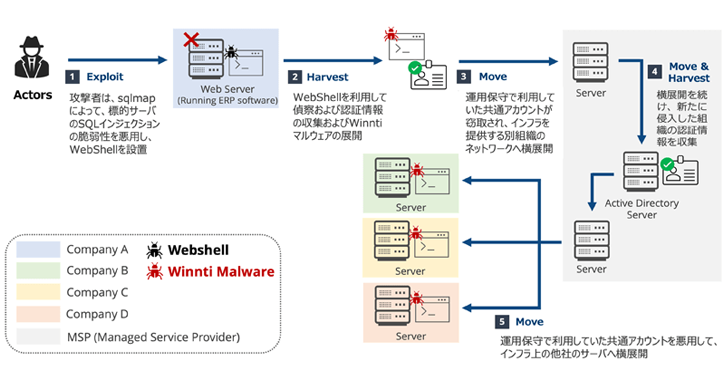
Winnti APT41 Targets Japanese Firms in RevivalStone Cyber Espionage Campaign
[ad_1] Feb 18, 2025Ravie LakshmananMalware / Network Security The China-linked threat actor known as Winnti has been attributed to a new campaign dubbed RevivalStone that targeted Japanese companies in the manufacturing, materials, and energy sectors in March 2024. The activity, detailed by Japanese cybersecurity company LAC, overlaps with a threat cluster tracked by Trend Micro…
Debunking the AI Hype: Inside Real Hacker Tactics
[ad_1] Feb 18, 2025The Hacker NewsArtificial Intelligence / Cyber Defense Is AI really reshaping the cyber threat landscape, or is the constant drumbeat of hype drowning out actual, more tangible, real-world dangers? According to Picus Labs’ Red Report 2025 which analyzed over one million malware samples, there’s been no significant surge, so far, in AI-driven…
New OpenSSH Flaws Enable Man-in-the-Middle and DoS Attacks — Patch Now
[ad_1] Feb 18, 2025Ravie LakshmananVulnerability / Network Security Two security vulnerabilities have been discovered in the OpenSSH secure networking utility suite that, if successfully exploited, could result in an active machine-in-the-middle (MitM) and a denial-of-service (DoS) attack, respectively, under certain conditions. The vulnerabilities, detailed by the Qualys Threat Research Unit (TRU), are listed below –…
Chinese Hackers Exploit MAVInject.exe to Evade Detection in Targeted Cyber Attacks
[ad_1] Feb 18, 2025Ravie LakshmananCyber Espionage / Malware The Chinese state-sponsored threat actor known as Mustang Panda has been observed employing a novel technique to evade detection and maintain control over infected systems. This involves the use of a legitimate Microsoft Windows utility called Microsoft Application Virtualization Injector (MAVInject.exe) to inject the threat actor’s malicious…
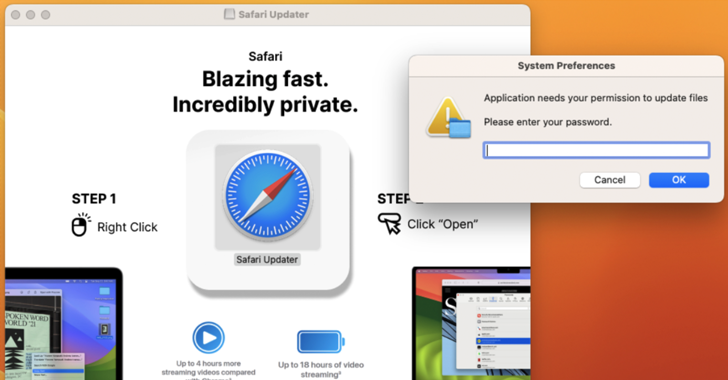
New FrigidStealer Malware Targets macOS Users via Fake Browser Updates
[ad_1] Feb 18, 2025Ravie LakshmananThreat Intelligence / Malware Cybersecurity researchers are alerting to a new campaign that leverages web injects to deliver a new Apple macOS malware known as FrigidStealer. The activity has been attributed to a previously undocumented threat actor known as TA2727, with the information stealers for other platforms such as Windows (Lumma…
Juniper Session Smart Routers Vulnerability Could Let Attackers Bypass Authentication
[ad_1] Feb 18, 2025Ravie LakshmananVulnerability / Network Security Juniper Networks has released security updates to address a critical security flaw impacting Session Smart Router, Session Smart Conductor, and WAN Assurance Router products that could be exploited to hijack control of susceptible devices. Tracked as CVE-2025-21589, the vulnerability carries a CVSS v3.1 score of 9.8 and…
Cybercriminals Exploit Onerror Event in Image Tags to Deploy Payment Skimmers
[ad_1] Feb 18, 2025Ravie LakshmananMalware / Website Hacking Cybersecurity researchers have flagged a credit card stealing malware campaign that has been observed targeting e-commerce sites running Magento by disguising the malicious content within image tags in HTML code in order to stay under the radar. MageCart is the name given to a malware that’s capable…