[ad_1] Mar 07, 2025Ravie LakshmananThreat Intelligence /Vulnerability Threat actors of unknown provenance have been attributed to a malicious campaign predominantly targeting organizations in Japan since January 2025. “The attacker has exploited the vulnerability CVE-2024-4577, a remote code execution (RCE) flaw in the PHP-CGI implementation of PHP on Windows, to gain initial access to victim machines,”…
Month: March 2025
Safe{Wallet} Confirms North Korean TraderTraitor Hackers Stole $1.5 Billion in Bybit Heist
[ad_1] Mar 07, 2025Ravie LakshmananSecurity Breach / Cryptocurrency Safe{Wallet} has revealed that the cybersecurity incident that led to the Bybit $1.5 billion crypto heist is a “highly sophisticated, state-sponsored attack,” stating the North Korean threat actors behind the hack took steps to erase traces of the malicious activity in an effort to hamper investigation efforts….
Medusa Ransomware Hits 40+ Victims in 2025, Demands $100K–$15M Ransom
[ad_1] Mar 06, 2025Ravie LakshmananThreat Intelligence / Vulnerability The threat actors behind the Medusa ransomware have claimed nearly 400 victims since it first emerged in January 2023, with the financially motivated attacks witnessing a 42% increase between 2023 and 2024. In the first two months of 2025 alone, the group has claimed over 40 attacks,…
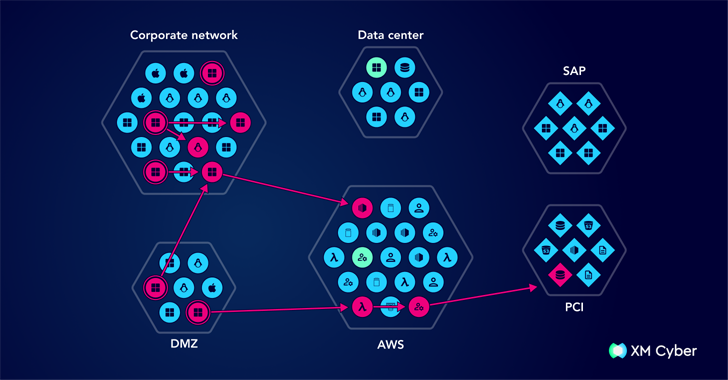
Outsmarting Cyber Threats with Attack Graphs
[ad_1] Cyber threats are growing more sophisticated, and traditional security approaches struggle to keep up. Organizations can no longer rely on periodic assessments or static vulnerability lists to stay secure. Instead, they need a dynamic approach that provides real-time insights into how attackers move through their environment. This is where attack graphs come in. By…
EncryptHub Deploys Ransomware and Stealer via Trojanized Apps, PPI Services, and Phishing
[ad_1] Mar 06, 2025Ravie LakshmananMalware / Ransomware The financially motivated threat actor known as EncryptHub has been observed orchestrating sophisticated phishing campaigns to deploy information stealers and ransomware, while also working on a new product called EncryptRAT. “EncryptHub has been observed targeting users of popular applications, by distributing trojanized versions,” Outpost24 KrakenLabs said in a…
Elastic Releases Urgent Fix for Critical Kibana Vulnerability Enabling Remote Code Execution
[ad_1] Mar 06, 2025Ravie LakshmananData Security / Software Security Elastic has rolled out security updates to address a critical security flaw impacting the Kibana data visualization dashboard software for Elasticsearch that could result in arbitrary code execution. The vulnerability, tracked as CVE-2025-25012, carries a CVSS score of 9.9 out of a maximum of 10.0. It…
Over 1,000 WordPress Sites Infected with JavaScript Backdoors Enabling Persistent Attacker Access
[ad_1] Mar 06, 2025Ravie LakshmananData Breach / Website Security Over 1,000 websites powered by WordPress have been infected with a third-party JavaScript code that injects four separate backdoors. “Creating four backdoors facilitates the attackers having multiple points of re-entry should one be detected and removed,” c/side researcher Himanshu Anand said in a Wednesday analysis. The…
U.S. Charges 12 Chinese Nationals in State-Backed Hacking Operations
[ad_1] The U.S. Department of Justice (DoJ) has announced charges against 12 Chinese nationals for their alleged participation in a wide-ranging scheme designed to steal data and suppress free speech and dissent globally. The individuals include two officers of the People’s Republic of China’s (PRC) Ministry of Public Security (MPS), eight employees of an ostensibly…
Identity: The New Cybersecurity Battleground
[ad_1] The rapid adoption of cloud services, SaaS applications, and the shift to remote work have fundamentally reshaped how enterprises operate. These technological advances have created a world of opportunity but also brought about complexities that pose significant security threats. At the core of these vulnerabilities lies Identity—the gateway to enterprise security and the number…
Chinese APT Lotus Panda Targets Governments With New Sagerunex Backdoor Variants
[ad_1] Mar 05, 2025Ravie LakshmananCyber Espionage / Network Security The threat actor known as Lotus Panda has been observed targeting government, manufacturing, telecommunications, and media sectors in the Philippines, Vietnam, Hong Kong, and Taiwan with updated versions of a known backdoor called Sagerunex. “Lotus Blossom has been using the Sagerunex backdoor since at least 2016…