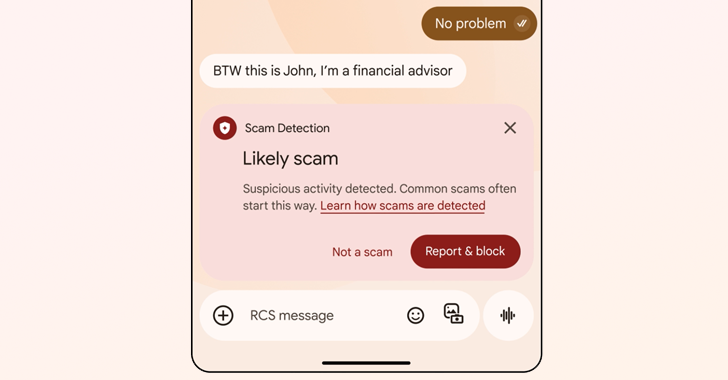
[ad_1] Mar 05, 2025Ravie LakshmananMobile Security / Artificial Intelligence Google has announced the rollout of artificial intelligence (AI)-powered scam detection features to secure Android device users and their personal information. “These features specifically target conversational scams, which can often appear initially harmless before evolving into harmful situations,” Google said. “And more phone calling scammers are…
Month: March 2025
Dark Caracal Uses Poco RAT to Target Spanish-Speaking Enterprises in Latin America
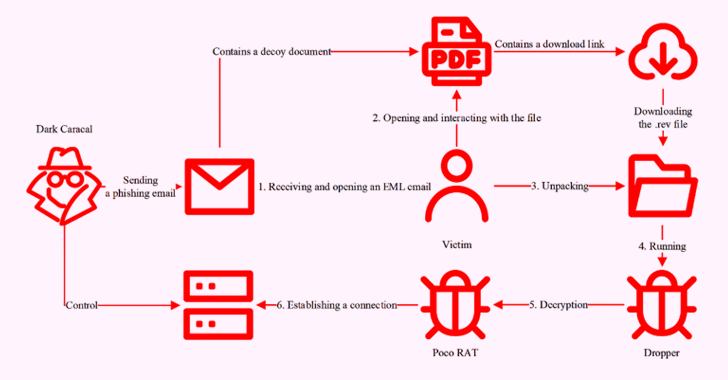
[ad_1] Mar 05, 2025Ravie LakshmananCyber Espionage / Malware The threat actor known as Dark Caracal has been attributed to a campaign that deployed a remote access trojan called Poco RAT in attacks targeting Spanish-speaking targets in Latin America in 2024. The findings come from Russian cybersecurity company Positive Technologies, which described the malware as loaded…
Defending against USB drive attacks with Wazuh
[ad_1] USB drive attacks constitute a significant cybersecurity risk, taking advantage of the everyday use of USB devices to deliver malware and circumvent traditional network security measures. These attacks lead to data breaches, financial losses, and operational disruptions, with lasting impacts on an organization’s reputation. An example is the Stuxnet worm discovered in 2010, a…
China-Linked Silk Typhoon Expands Cyber Attacks to IT Supply Chains for Initial Access
[ad_1] Mar 05, 2025Ravie LakshmananNetwork Security / Data Breach The China-lined threat actor behind the zero-day exploitation of security flaws in Microsoft Exchange servers in January 2021 has shifted its tactics to target the information technology (IT) supply chain as a means to obtain initial access to corporate networks. That’s according to new findings from…
Seven Malicious Go Packages Found Deploying Malware on Linux and macOS Systems
[ad_1] Mar 05, 2025Ravie LakshmananOpen Source / Malware Cybersecurity researchers are alerting of an ongoing malicious campaign targeting the Go ecosystem with typosquatted modules that are designed to deploy loader malware on Linux and Apple macOS systems. “The threat actor has published at least seven packages impersonating widely used Go libraries, including one (github[.]com/shallowmulti/hypert) that…
Over 4,000 ISP IPs Targeted in Brute-Force Attacks to Deploy Info Stealers and Cryptominers
[ad_1] Mar 04, 2025Ravie LakshmananNetwork Security / Ransomware Internet service providers (ISPs) in China and the West Coast of the United States have become the target of a mass exploitation campaign that deploys information stealers and cryptocurrency miners on compromised hosts. The findings come from the Splunk Threat Research Team, which said the activity also…
Researchers Link CACTUS Ransomware Tactics to Former Black Basta Affiliates
[ad_1] Mar 04, 2025Ravie LakshmananCybercrime / Threat Intelligence Threat actors deploying the Black Basta and CACTUS ransomware families have been found to rely on the same BackConnect (BC) module for maintaining persistent control over infected hosts, a sign that affiliates previously associated with Black Basta may have transitioned to CACTUS. “Once infiltrated, it grants attackers…
VMware Security Flaws Exploited in the Wild—Broadcom Releases Urgent Patches
[ad_1] Mar 04, 2025Ravie LakshmananVulnerability / Cloud Security Broadcom has released security updates to address three actively exploited security flaws in VMware ESXi, Workstation, and Fusion products that could lead to code execution and information disclosure. The list of vulnerabilities is as follows – CVE-2025-22224 (CVSS score: 9.3) – A Time-of-Check Time-of-Use (TOCTOU) vulnerability that…
Suspected Iranian Hackers Used Compromised Indian Firm’s Email to Target U.A.E. Aviation Sector
[ad_1] Mar 04, 2025Ravie LakshmananCyber Espionage / Malware Threat hunters are calling attention to a new highly-targeted phishing campaign that singled out “fewer than five” entities in the United Arab Emirates (U.A.E.) to deliver a previously undocumented Golang backdoor dubbed Sosano. The malicious activity was specifically directed against aviation and satellite communications organizations, according to…
How New AI Agents Will Transform Credential Stuffing Attacks
[ad_1] Credential stuffing attacks had a huge impact in 2024, fueled by a vicious circle of infostealer infections and data breaches. But things could be about to get worse still with Computer-Using Agents, a new kind of AI agent that enables low-cost, low-effort automation of common web tasks — including those frequently performed by attackers….