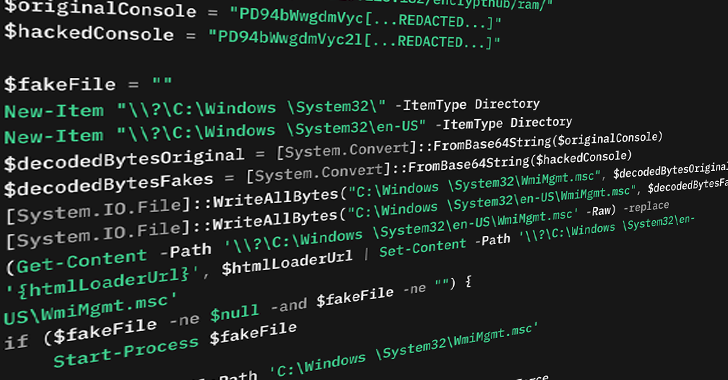
[ad_1] Mar 26, 2025Ravie LakshmananWindows Security / Vulnerability The threat actor known as EncryptHub exploited a recently-patched security vulnerability in Microsoft Windows as a zero-day to deliver a wide range of malware families, including backdoors and information stealers such as Rhadamanthys and StealC. “In this attack, the threat actor manipulates .msc files and the Multilingual…
Month: March 2025
Malicious npm Package Modifies Local ‘ethers’ Library to Launch Reverse Shell Attacks
[ad_1] Mar 26, 2025Ravie LakshmananSupply Chain Attack / Malware Cybersecurity researchers have discovered two malicious packages on the npm registry that are designed to infect another locally installed package, underscoring the continued evolution of software supply chain attacks targeting the open-source ecosystem. The packages in question are ethers-provider2 and ethers-providerz, with the former downloaded 73…
Hackers Using E-Crime Tool Atlantis AIO for Credential Stuffing on 140+ Platforms
[ad_1] Mar 26, 2025Ravie LakshmananPassword Security / Cybercrime Threat actors are leveraging an e-crime tool called Atlantis AIO Multi-Checker to automate credential stuffing attacks, according to findings from Abnormal Security. Atlantis AIO “has emerged as a powerful weapon in the cybercriminal arsenal, enabling attackers to test millions of stolen credentials in rapid succession,” the cybersecurity…
New Security Flaws Found in VMware Tools and CrushFTP — High Risk, No Workaround
[ad_1] Mar 26, 2025Ravie LakshmananVulnerability / Data Security Broadcom has issued security patches to address a high-severity security flaw in VMware Tools for Windows that could lead to an authentication bypass. Tracked as CVE-2025-22230, the vulnerability is rated 7.8 on the ten-point Common Vulnerability Scoring System (CVSS). “VMware Tools for Windows contains an authentication bypass…
Google Releases Chrome Patch for Exploit Used in Russian Espionage Attacks
[ad_1] Mar 26, 2025Ravie LakshmananBrowser Security / Vulnerability Google has released out-of-band fixes to address a high-severity security flaw in its Chrome browser for Windows that it said has been exploited in the wild as part of attacks targeting organizations in Russia. The vulnerability, tracked as CVE-2025-2783, has been described as a case of “incorrect…
Chinese Hackers Breach Asian Telecom, Remain Undetected for Over 4 Years
[ad_1] Mar 25, 2025Ravie LakshmananCyber Espionage / Network Security A major telecommunications company located in Asia was allegedly breached by Chinese state-sponsored hackers who spent over four years inside its systems, according to a new report from incident response firm Sygnia. The cybersecurity company is tracking the activity under the name Weaver Ant, describing the…
Researchers Uncover ~200 Unique C2 Domains Linked to Raspberry Robin Access Broker
[ad_1] Mar 25, 2025Ravie LakshmananThreat Intelligence / Malware A new investigation has unearthed nearly 200 unique command-and-control (C2) domains associated with a malware called Raspberry Robin. “Raspberry Robin (also known as Roshtyak or Storm-0856) is a complex and evolving threat actor that provides initial access broker (IAB) services to numerous criminal groups, many of which…
Keeping Pace with an Expanding Attack Surface
[ad_1] Organizations now use an average of 112 SaaS applications—a number that keeps growing. In a 2024 study, 49% of 644 respondents who frequently used Microsoft 365 believed that they had less than 10 apps connected to the platform, despite the fact that aggregated data indicated over 1,000+ Microsoft 365 SaaS-to-SaaS connections on average per…
Hackers Use .NET MAUI to Target Indian and Chinese Users with Fake Banking, Social Apps
[ad_1] Mar 25, 2025Ravie LakshmananMobile Security / Data Theft Cybersecurity researchers are calling attention to an Android malware campaign that leverages Microsoft’s .NET Multi-platform App UI (.NET MAUI) framework to create bogus banking and social media apps targeting Indian and Chinese-speaking users. “These threats disguise themselves as legitimate apps, targeting users to steal sensitive information,”…
INTERPOL Arrests 306 Suspects, Seizes 1,842 Devices in Cross-Border Cybercrime Bust
[ad_1] Law enforcement authorities in seven African countries have arrested 306 suspects and confiscated 1,842 devices as part of an international operation codenamed Red Card that took place between November 2024 and February 2025. The coordinated effort “aims to disrupt and dismantle cross-border criminal networks which cause significant harm to individuals and businesses,” INTERPOL said,…