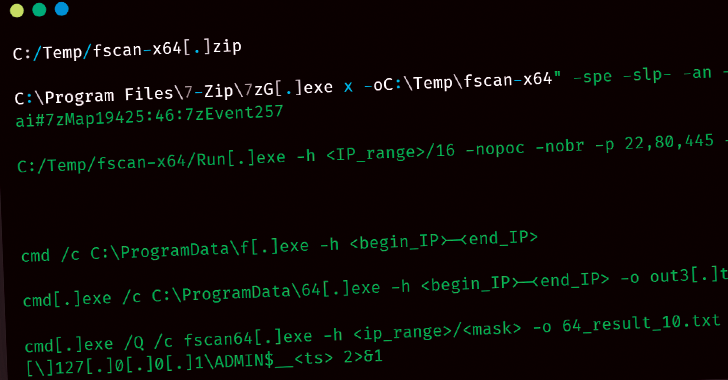
[ad_1] Mar 21, 2025Ravie LakshmananThreat Hunting / Vulnerability Threat hunters have uncovered a new threat actor named UAT-5918 that has been attacking critical infrastructure entities in Taiwan since at least 2023. “UAT-5918, a threat actor believed to be motivated by establishing long-term access for information theft, uses a combination of web shells and open-sourced tooling…
Month: March 2025
Medusa Ransomware Uses Malicious Driver to Disable Anti-Malware with Stolen Certificates
[ad_1] Mar 21, 2025Ravie LakshmananRansomware / BYOVD The threat actors behind the Medusa ransomware-as-a-service (RaaS) operation have been observed using a malicious driver dubbed ABYSSWORKER as part of a bring your own vulnerable driver (BYOVD) attack designed to disable anti-malware tools. Elastic Security Labs said it observed a Medusa ransomware attack that delivered the encryptor…
10 Critical Network Pentest Findings IT Teams Overlook
[ad_1] Mar 21, 2025The Hacker NewsNetwork Security / Vulnerability After conducting over 10,000 automated internal network penetration tests last year, vPenTest has uncovered a troubling reality that many businesses still have critical security gaps that attackers can easily exploit. Organizations often assume that firewalls, endpoint protection, and SIEMs are enough to keep them secure. But…
10-Month Campaign, 7 Global Targets, 5 Malware Families
[ad_1] Mar 21, 2025Ravie LakshmananCybercrime / Cyber Espionage The China-linked advanced persistent threat (APT) group. known as Aquatic Panda has been linked to a “global espionage campaign” that took place in 2022 targeting seven organizations. These entities include governments, catholic charities, non-governmental organizations (NGOs), and think tanks across Taiwan, Hungary, Turkey, Thailand, France, and the…
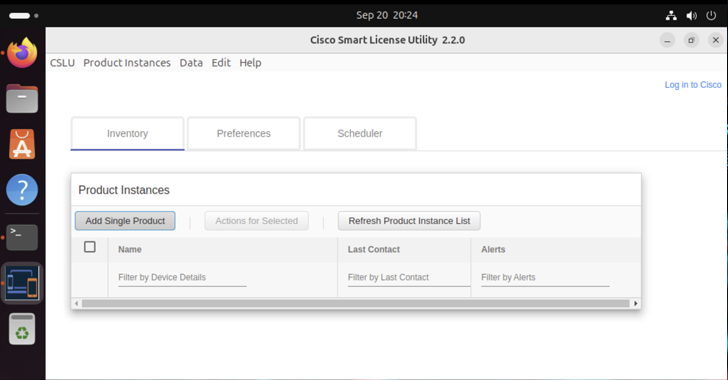
Ongoing Cyber Attacks Exploit Critical Vulnerabilities in Cisco Smart Licensing Utility
[ad_1] Mar 21, 2025Ravie LakshmananCyber Attack / Vulnerability Two now-patched security flaws impacting Cisco Smart Licensing Utility are seeing active exploitation attempts, according to SANS Internet Storm Center. The two critical-rated vulnerabilities in question are listed below – CVE-2024-20439 (CVSS score: 9.8) – The presence of an undocumented static user credential for an administrative account…
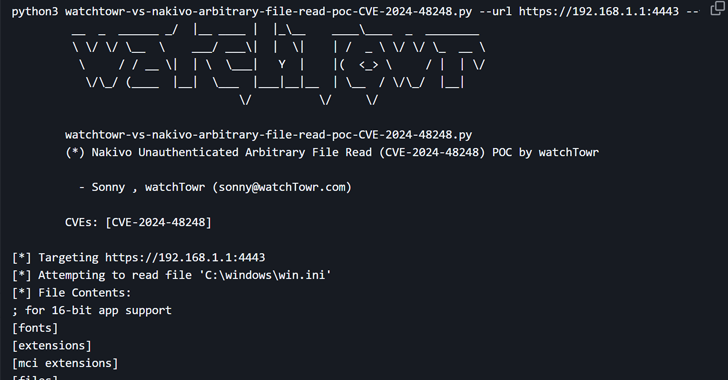
CISA Adds NAKIVO Vulnerability to KEV Catalog Amid Active Exploitation
[ad_1] Mar 20, 2025Ravie LakshmananCybersecurity / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a high-severity security flaw impacting NAKIVO Backup & Replication software to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. The vulnerability in question is CVE-2024-48248 (CVSS score: 8.6), an absolute path traversal bug that could…
Why Continuous Compliance Monitoring Is Essential For IT Managed Service Providers
[ad_1] Regulatory compliance is no longer just a concern for large enterprises. Small and mid-sized businesses (SMBs) are increasingly subject to strict data protection and security regulations, such as HIPAA, PCI-DSS, CMMC, GDPR, and the FTC Safeguards Rule. However, many SMBs struggle to maintain compliance due to limited IT resources, evolving regulatory requirements, and complex…
YouTube Game Cheats Spread Arcane Stealer Malware to Russian-Speaking Users
[ad_1] Mar 20, 2025Ravie LakshmananMalware / Threat Analysis YouTube videos promoting game cheats are being used to deliver a previously undocumented stealer malware called Arcane likely targeting Russian-speaking users. “What’s intriguing about this malware is how much it collects,” Kaspersky said in an analysis. “It grabs account information from VPN and gaming clients, and all…
Veeam and IBM Release Patches for High-Risk Flaws in Backup and AIX Systems
[ad_1] Mar 20, 2025Ravie LakshmananVulnerability / Software Update Veeam has released security updates to address a critical security flaw impacting its Backup & Replication software that could lead to remote code execution. The vulnerability, tracked as CVE-2025-23120, carries a CVSS score of 9.9 out of 10.0. It affects 12.3.0.310 and all earlier version 12 builds….
How to Protect Your Business from Cyber Threats: Mastering the Shared Responsibility Model
[ad_1] Cybersecurity isn’t just another checkbox on your business agenda. It’s a fundamental pillar of survival. As organizations increasingly migrate their operations to the cloud, understanding how to protect your digital assets becomes crucial. The shared responsibility model, exemplified through Microsoft 365’s approach, offers a framework for comprehending and implementing effective cybersecurity [ad_2]