[ad_1] Mar 17, 2025Ravie LakshmananWeb Security / Cyber Threat Malicious actors are exploiting Cascading Style Sheets (CSS), which are used to style and format the layout of web pages, to bypass spam filters and track users’ actions. That’s according to new findings from Cisco Talos, which said such malicious activities can compromise a victim’s security…
Month: March 2025
Unpatched Edimax Camera Flaw Exploited for Mirai Botnet Attacks Since Last Year
[ad_1] Mar 17, 2025Ravie LakshmananBotnet / Vulnerability An unpatched security flaw impacting the Edimax IC-7100 network camera is being exploited by threat actors to deliver Mirat botnet malware variants since at least May 2024. The vulnerability in question is CVE-2025-1316 (CVSS v4 score: 9.3), a critical operating system command injection flaw that an attacker could…
Router Hacks, PyPI Attacks, New Ransomware Decryptor, and More
[ad_1] Mar 17, 2025Ravie LakshmananCybersecurity / Hacking News From sophisticated nation-state campaigns to stealthy malware lurking in unexpected places, this week’s cybersecurity landscape is a reminder that attackers are always evolving. Advanced threat groups are exploiting outdated hardware, abusing legitimate tools for financial fraud, and finding new ways to bypass security defenses. Meanwhile, supply chain…
GitHub Action Compromise Puts CI/CD Secrets at Risk in Over 23,000 Repositories
[ad_1] Mar 17, 2025Ravie LakshmananVulnerability / Cloud Security Cybersecurity researchers are calling attention to an incident in which the popular GitHub Action tj-actions/changed-files was compromised to leak secrets from repositories using the continuous integration and continuous delivery (CI/CD) workflow. The incident involved the tj-actions/changed-files GitHub Action, which is used in over 23,000 repositories. It’s used…
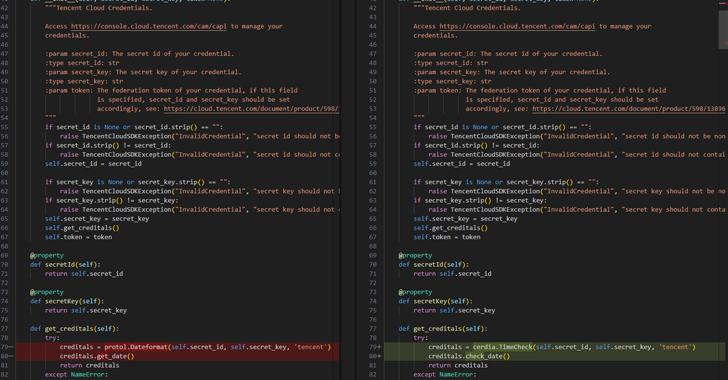
Malicious PyPI Packages Stole Cloud Tokens—Over 14,100 Downloads Before Removal
[ad_1] Mar 15, 2025Ravie Lakshmanan Malware / Supply Chain Security Cybersecurity researchers have warned of a malicious campaign targeting users of the Python Package Index (PyPI) repository with bogus libraries masquerading as “time” related utilities, but harboring hidden functionality to steal sensitive data such as cloud access tokens. Software supply chain security firm ReversingLabs said…
Alleged Israeli LockBit Developer Rostislav Panev Extradited to U.S. for Cybercrime Charges
[ad_1] Mar 14, 2025Ravie LakshmananCybercrime / Ransomware A 51-year-old dual Russian and Israeli national who is alleged to be a developer of the LockBit ransomware group has been extradited to the United States, nearly three months after he was formally charged in connection with the e-crime scheme. Rostislav Panev was previously arrested in Israel in…
GSMA Confirms End-to-End Encryption for RCS, Enabling Secure Cross-Platform Messaging
[ad_1] Mar 14, 2025Ravie LakshmananMobile Security / Encryption The GSM Association (GSMA) has formally announced support for end-to-end encryption (E2EE) for securing messages sent via the Rich Communications Services (RCS) protocol, bringing much-needed security protections to cross-platform messages shared between Android and iOS platforms. To that end, the new GSMA specifications for RCS include E2EE…
Why Most Microsegmentation Projects Fail—And How Andelyn Biosciences Got It Right
[ad_1] Most microsegmentation projects fail before they even get off the ground—too complex, too slow, too disruptive. But Andelyn Biosciences proved it doesn’t have to be that way. Microsegmentation: The Missing Piece in Zero Trust Security Security teams today are under constant pressure to defend against increasingly sophisticated cyber threats. Perimeter-based defenses alone can no…
See How Hackers Breach Networks and Demand a Ransom
[ad_1] Mar 14, 2025The Hacker NewsData Protection / Ransomware Cyber threats evolve daily. In this live webinar, learn exactly how ransomware attacks unfold—from the initial breach to the moment hackers demand payment. Join Joseph Carson, Delinea’s Chief Security Scientist and Advisory CISO, who brings 25 years of enterprise security expertise. Through a live demonstration, he…
New MassJacker Malware Targets Piracy Users, Hijacking Cryptocurrency Transactions
[ad_1] Mar 14, 2025Ravie LakshmananSoftware Security / Cybercrime Users searching for pirated software are the target of a new malware campaign that delivers a previously undocumented clipper malware called MassJacker, according to findings from CyberArk. Clipper malware is a type of cryware (as coined by Microsoft) that’s designed to monitor a victim’s clipboard content and…