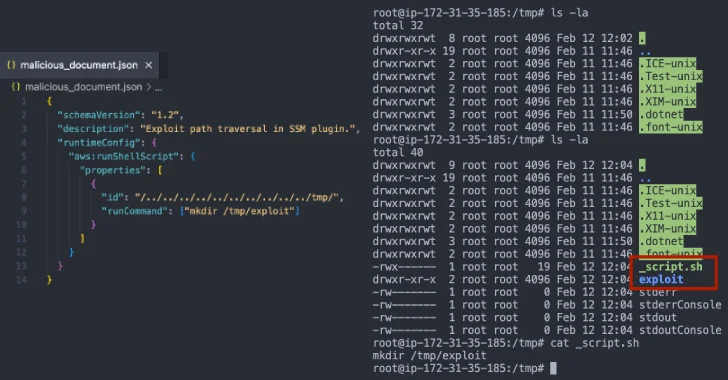
[ad_1] Apr 08, 2025Ravie LakshmananCloud Security / Vulnerability Cybersecurity researchers have disclosed details of a now-patched security flaw in the Amazon EC2 Simple Systems Manager (SSM) Agent that, if successfully exploited, could permit an attacker to achieve privilege escalation and code execution. The vulnerability could permit an attacker to create directories in unintended locations on…
Month: April 2025
UAC-0226 Deploys GIFTEDCROOK Stealer via Malicious Excel Files Targeting Ukraine
[ad_1] The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed a new set of cyber attacks targeting Ukrainian institutions with information-stealing malware. The activity is aimed at military formations, law enforcement agencies, and local self-government bodies, particularly those located near Ukraine’s eastern border, the agency said. The attacks involve distributing phishing emails containing a…
Agentic AI in the SOC
[ad_1] Security Operations Centers (SOCs) today face unprecedented alert volumes and increasingly sophisticated threats. Triaging and investigating these alerts are costly, cumbersome, and increases analyst fatigue, burnout, and attrition. While artificial intelligence has emerged as a go-to solution, the term “AI” often blurs crucial distinctions. Not all AI is built equal, especially in the SOC….
CISA Adds CrushFTP Vulnerability to KEV Catalog Following Confirmed Active Exploitation
[ad_1] Apr 08, 2025Ravie LakshmananCyber Attack / Vulnerability A recently disclosed critical security flaw impacting CrushFTP has been added by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to its Known Exploited Vulnerabilities (KEV) catalog after reports emerged of active exploitation in the wild. The vulnerability is a case of authentication bypass that could permit…
Google Releases Android Update to Patch Two Actively Exploited Vulnerabilities
[ad_1] Apr 08, 2025Ravie LakshmananMobile Security / Vulnerability Google has shipped patches for 62 vulnerabilities, two of which it said have been exploited in the wild. The two high-severity vulnerabilities are listed below – CVE-2024-53150 (CVSS score: 7.8) – An out-of-bounds flaw in the USB sub-component of Kernel that could result in information disclosure CVE-2024-53197…
CISA and FBI Warn Fast Flux is Powering Resilient Malware, C2, and Phishing Networks
[ad_1] Apr 07, 2025Ravie LakshmananMalware / Network Security Cybersecurity agencies from Australia, Canada, New Zealand, and the United States have published a joint advisory about the risks associated with a technique called fast flux that has been adopted by threat actors to obscure a command-and-control (C2) channel. “‘Fast flux’ is a technique used to obfuscate…
VPN Exploits, Oracle’s Silent Breach, ClickFix Comeback and More
[ad_1] Apr 07, 2025Ravie LakshmananThreat Intelligence / Cybersecurity Today, every unpatched system, leaked password, and overlooked plugin is a doorway for attackers. Supply chains stretch deep into the code we trust, and malware hides not just in shady apps — but in job offers, hardware, and cloud services we rely on every day. Hackers don’t…
Security Theater: Vanity Metrics Keep You Busy
[ad_1] Apr 07, 2025The Hacker News After more than 25 years of mitigating risks, ensuring compliance, and building robust security programs for Fortune 500 companies, I’ve learned that looking busy isn’t the same as being secure. It’s an easy trap for busy cybersecurity leaders to fall into. We rely on metrics that tell a story…
PoisonSeed Exploits CRM Accounts to Launch Cryptocurrency Seed Phrase Poisoning Attacks
[ad_1] Apr 07, 2025Ravie LakshmananCloud Security / Cryptocurrency A malicious campaign dubbed PoisonSeed is leveraging compromised credentials associated with customer relationship management (CRM) tools and bulk email providers to send spam messages containing cryptocurrency seed phrases in an attempt to drain victims’ digital wallets. “Recipients of the bulk spam are targeted with a cryptocurrency seed…
Mozilla Patches Critical Firefox Bug Similar to Chrome’s Recent Zero-Day Vulnerability
[ad_1] Mar 28, 2025Ravie LakshmananZero-Day / Browser Security Mozilla has released updates to address a critical security flaw impacting its Firefox browser for Windows, merely days after Google patched a similar flaw in Chrome that came under active exploitation as a zero-day. The security vulnerability, CVE-2025-2857, has been described as a case of an incorrect…