[ad_1] Apr 04, 2025Ravie LakshmananThreat Intelligence / Malware A novice cybercrime actor has been observed leveraging the services of a Russian bulletproof hosting (BPH) provider called Proton66 to facilitate their operations. The findings come from DomainTools, which detected the activity after it discovered a phony website named cybersecureprotect[.]com hosted on Proton66 that masqueraded as an…
Month: April 2025
Have We Reached a Distroless Tipping Point?
[ad_1] There’s a virtuous cycle in technology that pushes the boundaries of what’s being built and how it’s being used. A new technology development emerges and captures the world’s attention. People start experimenting and discover novel applications, use cases, and approaches to maximize the innovation’s potential. These use cases generate significant value, fueling demand for…
Critical Flaw in Apache Parquet Allows Remote Attackers to Execute Arbitrary Code
[ad_1] Apr 04, 2025Ravie LakshmananVulnerability / Cloud Security A maximum severity security vulnerability has been disclosed in Apache Parquet’s Java Library that, if successfully exploited, could allow a remote attacker to execute arbitrary code on susceptible instances. Apache Parquet is a free and open-source columnar data file format that’s designed for efficient data processing and…
Critical Ivanti Flaw Actively Exploited to Deploy TRAILBLAZE and BRUSHFIRE Malware
[ad_1] Apr 04, 2025Ravie LakshmananMalware / Vulnerability Ivanti has disclosed details of a now-patched critical security vulnerability impacting its Connect Secure that has come under active exploitation in the wild. The vulnerability, tracked as CVE-2025-22457 (CVSS score: 9.0), concerns a case of a stack-based buffer overflow that could be exploited to execute arbitrary code on…
CERT-UA Reports Cyberattacks Targeting Ukrainian State Systems with WRECKSTEEL Malware
[ad_1] Apr 04, 2025Ravie LakshmananCritical Infrastructure / Malware The Computer Emergency Response Team of Ukraine (CERT-UA) has revealed that no less than three cyber attacks were recorded against state administration bodies and critical infrastructure facilities in the country with an aim to steal sensitive data. who is sophie rain jskoe426 The campaign, the agency said,…
Triada Malware Preloaded on Counterfeit Android Phones Infects 2,600+ Devices
[ad_1] Apr 03, 2025Ravie LakshmananThreat Intelligence / Mobile Security Counterfeit versions of popular smartphone models that are sold at reduced prices have been found to be preloaded with a modified version of an Android malware called Triada. “More than 2,600 users in different countries have encountered the new version of Triada, the majority in Russia,”…
Google Patches Quick Share Vulnerability Enabling Silent File Transfers Without Consent
[ad_1] Apr 03, 2025Ravie LakshmananData Privacy / Vulnerability Cybersecurity researchers have disclosed details of a new vulnerability impacting Google’s Quick Share data transfer utility for Windows that could be exploited to achieve a denial-of-service (DoS) or send arbitrary files to a target’s device without their approval. The flaw, tracked as CVE-2024-10668 (CVSS score: 5.9), is…
Breaking Through the Security and Compliance Gridlock
[ad_1] AI holds the promise to revolutionize all sectors of enterpriseーfrom fraud detection and content personalization to customer service and security operations. Yet, despite its potential, implementation often stalls behind a wall of security, legal, and compliance hurdles. Imagine this all-too-familiar scenario: A CISO wants to deploy an AI-driven SOC to handle the overwhelming volume…
AI Threats Are Evolving Fast — Learn Practical Defense Tactics in this Expert Webinar
[ad_1] Apr 03, 2025The Hacker News The rules have changed. Again. Artificial intelligence is bringing powerful new tools to businesses. But it’s also giving cybercriminals smarter ways to attack. They’re moving quicker, targeting more precisely, and slipping past old defenses without being noticed. And here’s the harsh truth: If your security strategy hasn’t evolved with…
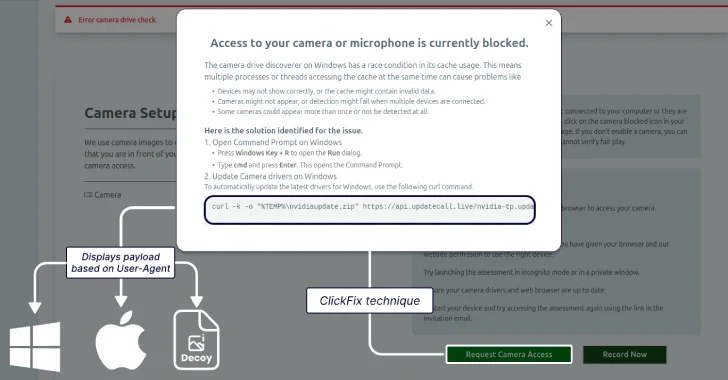
Lazarus Group Targets Job Seekers With ClickFix Tactic to Deploy GolangGhost Malware
[ad_1] The North Korean threat actors behind Contagious Interview have adopted the increasingly popular ClickFix social engineering tactic to lure job seekers in the cryptocurrency sector to deliver a previously undocumented Go-based backdoor called GolangGhost on Windows and macOS systems. The new activity, assessed to be a continuation of the campaign, has been codenamed ClickFake…