[ad_1] Microsoft is warning of several phishing campaigns that are leveraging tax-related themes to deploy malware and steal credentials. “These campaigns notably use redirection methods such as URL shorteners and QR codes contained in malicious attachments and abuse legitimate services like file-hosting services and business profile pages to avoid detection,” Microsoft said in a report…
Month: April 2025
Outlaw Group Uses SSH Brute-Force to Deploy Cryptojacking Malware on Linux Servers
[ad_1] Apr 02, 2025Ravie LakshmananCryptojacking / Malware Cybersecurity researchers have shed light on an “auto-propagating” cryptocurrency mining botnet called Outlaw (aka Dota) that’s known for targeting SSH servers with weak credentials. “Outlaw is a Linux malware that relies on SSH brute-force attacks, cryptocurrency mining, and worm-like propagation to infect and maintain control over systems,” Elastic…
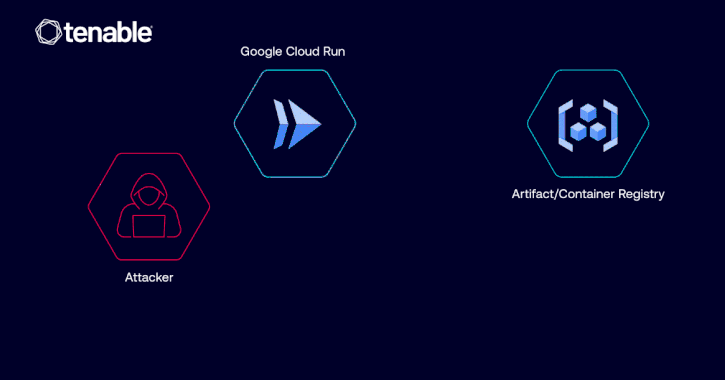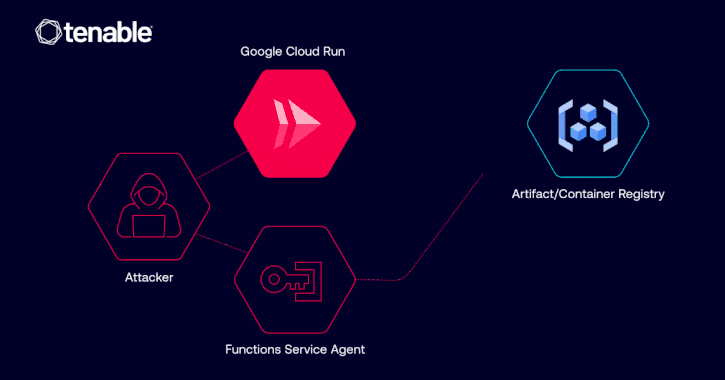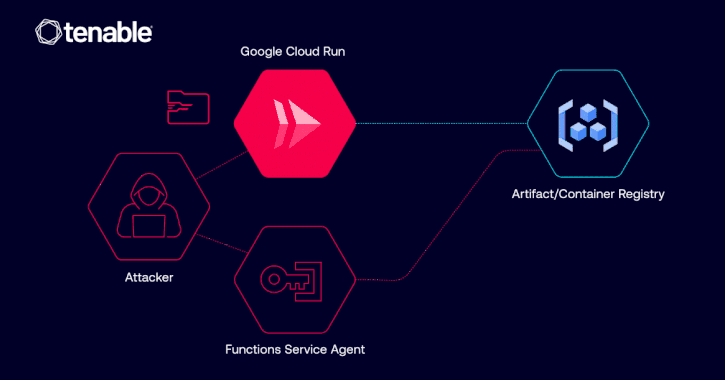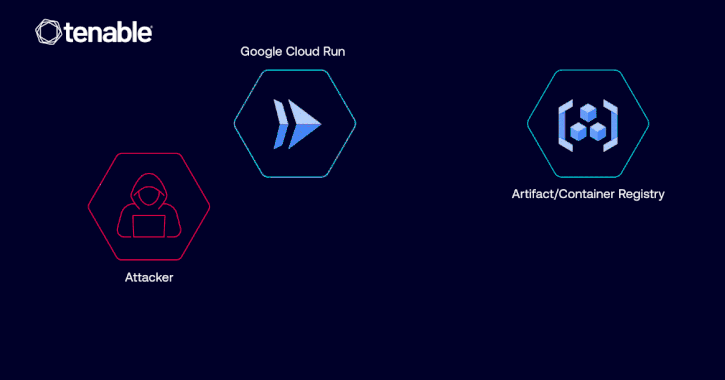
Google Fixed Cloud Run Vulnerability Allowing Unauthorized Image Access via IAM Misuse
[ad_1] Apr 02, 2025Ravie LakshmananCloud Security / Vulnerability Cybersecurity researchers have disclosed details of a now-patched privilege escalation vulnerability in Google Cloud Platform (GCP) Cloud Run that could have allowed a malicious actor to access container images and even inject malicious code. “The vulnerability could have allowed such an identity to abuse its Google Cloud…
A Step by Step Guide for Service Providers
[ad_1] Apr 02, 2025The Hacker NewsCompliance / Data Protection Introduction As the cybersecurity landscape evolves, service providers play an increasingly vital role in safeguarding sensitive data and maintaining compliance with industry regulations. The National Institute of Standards and Technology (NIST) offers a comprehensive set of frameworks that provide a clear path to achieving robust cybersecurity…
FIN7 Deploys Anubis Backdoor to Hijack Windows Systems via Compromised SharePoint Sites
[ad_1] Apr 02, 2025Ravie LakshmananRansomware / Email Security The financially motivated threat actor known as FIN7 has been linked to a Python-based backdoor called Anubis (not to be confused with an Android banking trojan of the same name) that can grant them remote access to compromised Windows systems. “This malware allows attackers to execute remote…
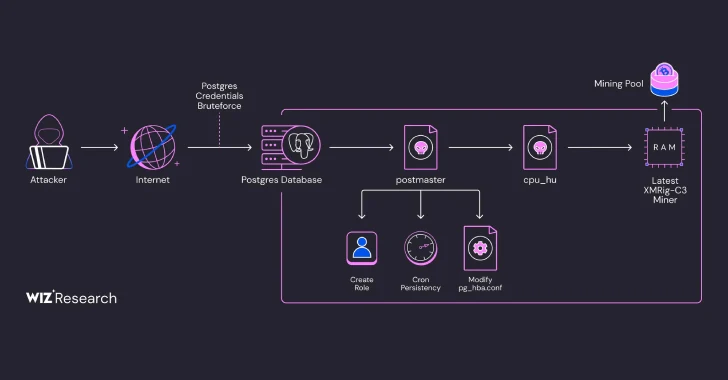
Over 1,500 PostgreSQL Servers Compromised in Fileless Cryptocurrency Mining Campaign
[ad_1] Apr 01, 2025Ravie LakshmananCryptojacking / Cloud Security Exposed PostgreSQL instances are the target of an ongoing campaign designed to gain unauthorized access and deploy cryptocurrency miners. Cloud security firm Wiz said the activity is a variant of an intrusion set that was first flagged by Aqua Security in August 2024 that involved the use…