[ad_1] Cybersecurity company SentinelOne has revealed that a China-nexus threat cluster dubbed PurpleHaze conducted reconnaissance attempts against its infrastructure and some of its high-value customers. “We first became aware of this threat cluster during a 2024 intrusion conducted against an organization previously providing hardware logistics services for SentinelOne employees,” security researchers Tom Hegel, Aleksandar Milenkoski,…
Month: April 2025
Google Reports 75 Zero-Days Exploited in 2024 — 44% Targeted Enterprise Security Products
[ad_1] Apr 29, 2025Ravie LakshmananEnterprise Security / Vulnerability Google has revealed that it observed 75 zero-day vulnerabilities exploited in the wild in 2024, down from 98 in 2023. Of the 75 zero-days, 44% of them targeted enterprise products. As many as 20 flaws were identified in security software and appliances. “Zero-day exploitation of browsers and…
Securing Microsoft Copilot with Reco
[ad_1] Find out how Reco keeps Microsoft 365 Copilot safe by spotting risky prompts, protecting data, managing user access, and identifying threats – all while keeping productivity high. Microsoft 365 Copilot promises to boost productivity by turning natural language prompts into actions. Employees can generate reports, comb through data, or get instant answers just by…
CISA Adds Actively Exploited Broadcom and Commvault Flaws to KEV Database
[ad_1] Apr 29, 2025Ravie LakshmananVulnerability / Web Security The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added two high-severity security flaws impacting Broadcom Brocade Fabric OS and Commvault Web Server to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation in the wild. The vulnerabilities in question are listed below –…
Malware Attack Targets World Uyghur Congress Leaders via Trojanized UyghurEdit++ Tool
[ad_1] Apr 29, 2025Ravie LakshmananCybersecurity / Malware In a new campaign detected in March 2025, senior members of the World Uyghur Congress (WUC) living in exile have been targeted by a Windows-based malware that’s capable of conducting surveillance. The spear-phishing campaign involved the use of a trojanized version of a legitimate open-source word processing and…
Earth Kurma Targets Southeast Asia With Rootkits and Cloud-Based Data Theft Tools
[ad_1] Government and telecommunications sectors in Southeast Asia have become the target of a “sophisticated” campaign undertaken by a new advanced persistent threat (APT) group called Earth Kurma since June 2024. The attacks, per Trend Micro, have leveraged custom malware, rootkits, and cloud storage services for data exfiltration. The Philippines, Vietnam, Thailand, and Malaysia are…
Breaking Down 5 Real Vulns
[ad_1] Not every security vulnerability is high risk on its own – but in the hands of an advanced attacker, even small weaknesses can escalate into major breaches. These five real vulnerabilities, uncovered by Intruder’s bug-hunting team, reveal how attackers turn overlooked flaws into serious security incidents. 1. Stealing AWS Credentials with a Redirect Server-Side…
Critical SAP Exploit, AI-Powered Phishing, Major Breaches, New CVEs & More
[ad_1] Apr 28, 2025Ravie LakshmananCybersecurity / Hacking News What happens when cybercriminals no longer need deep skills to breach your defenses? Today’s attackers are armed with powerful tools that do the heavy lifting — from AI-powered phishing kits to large botnets ready to strike. And they’re not just after big corporations. Anyone can be a…
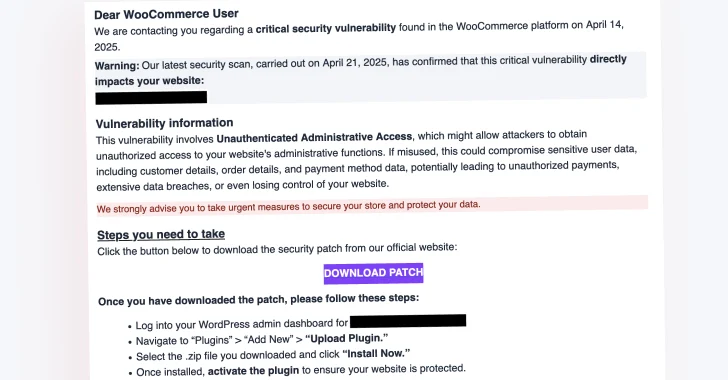
WooCommerce Users Targeted by Fake Patch Phishing Campaign Deploying Site Backdoors
[ad_1] Apr 28, 2025Ravie LakshmananWebsite Security / Malware Cybersecurity researchers are warning about a large-scale phishing campaign targeting WooCommerce users with a fake security alert urging them to download a “critical patch” but deploy a backdoor instead. WordPress security company Patchstack described the activity as sophisticated and a variant of another campaign observed in December…
Hackers Exploit Critical Craft CMS Flaws; Hundreds of Servers Likely Compromised
[ad_1] Apr 28, 2025Ravie LakshmananWeb Application Security / Vulnerability Threat actors have been observed exploiting two newly disclosed critical security flaws in Craft CMS in zero-day attacks to breach servers and gain unauthorized access. The attacks, first observed by Orange Cyberdefense SensePost on February 14, 2025, involve chaining the below vulnerabilities – CVE-2024-58136 (CVSS score:…