[ad_1] Apr 27, 2025Ravie LakshmananKubernetes / Cloud Security Microsoft has revealed that a threat actor it tracks as Storm-1977 has conducted password spraying attacks against cloud tenants in the education sector over the past year. “The attack involves the use of AzureChecker.exe, a Command Line Interface (CLI) tool that is being used by a wide…
Month: April 2025
ToyMaker Uses LAGTOY to Sell Access to CACTUS Ransomware Gangs for Double Extortion
[ad_1] Apr 26, 2025Ravie LakshmananMalware / Vulnerability Cybersecurity researchers have detailed the activities of an initial access broker (IAB) dubbed ToyMaker that has been observed handing over access to double extortion ransomware gangs like CACTUS. The IAB has been assessed with medium confidence to be a financially motivated threat actor, scanning for vulnerable systems and…
DslogdRAT Malware Deployed via Ivanti ICS Zero-Day CVE-2025-0282 in Japan Attacks
[ad_1] Apr 25, 2025Ravie LakshmananVulnerability / Network Security Cybersecurity researchers are warning about a new malware called DslogdRAT that’s installed following the exploitation of a now-patched security flaw in Ivanti Connect Secure (ICS). The malware, along with a web shell, were “installed by exploiting a zero-day vulnerability at that time, CVE-2025-0282, during attacks against organizations…
North Korean Hackers Spread Malware via Fake Crypto Firms and Job Interview Lures
[ad_1] North Korea-linked threat actors behind the Contagious Interview have set up front companies as a way to distribute malware during the fake hiring process. “In this new campaign, the threat actor group is using three front companies in the cryptocurrency consulting industry—BlockNovas LLC (blocknovas[.] com), Angeloper Agency (angeloper[.]com), and SoftGlide LLC (softglide[.]co)—to spread malware…
Why NHIs Are Security’s Most Dangerous Blind Spot
[ad_1] When we talk about identity in cybersecurity, most people think of usernames, passwords, and the occasional MFA prompt. But lurking beneath the surface is a growing threat that does not involve human credentials at all, as we witness the exponential growth of Non-Human Identities (NHIs). At the top of mind when NHIs are mentioned,…
SAP Confirms Critical NetWeaver Flaw Amid Suspected Zero-Day Exploitation by Hackers
[ad_1] Apr 25, 2025Ravie LakshmananVulnerability / Enterprise Security Threat actors are likely exploiting a new vulnerability in SAP NetWeaver to upload JSP web shells with the goal of facilitating unauthorized file uploads and code execution. “The exploitation is likely tied to either a previously disclosed vulnerability like CVE-2017-9844 or an unreported remote file inclusion (RFI)…
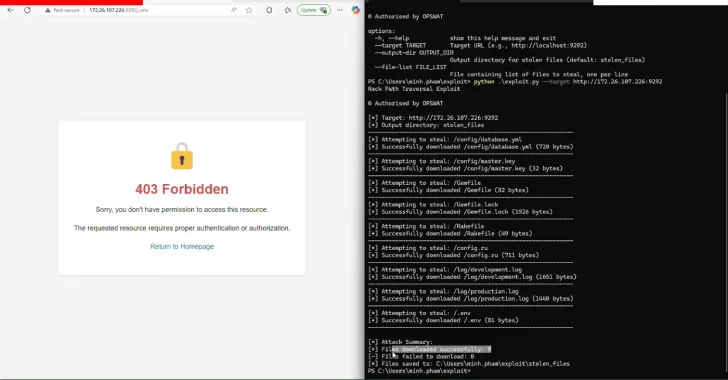
Researchers Identify Rack::Static Vulnerability Enabling Data Breaches in Ruby Servers
[ad_1] Apr 25, 2025Ravie LakshmananVulnerability / Data Breach Cybersecurity researchers have disclosed three security flaws in the Rack Ruby web server interface that, if successfully exploited, could enable attackers to gain unauthorized access to files, inject malicious data, and tamper with logs under certain conditions. The vulnerabilities, flagged by cybersecurity vendor OPSWAT, are listed below…
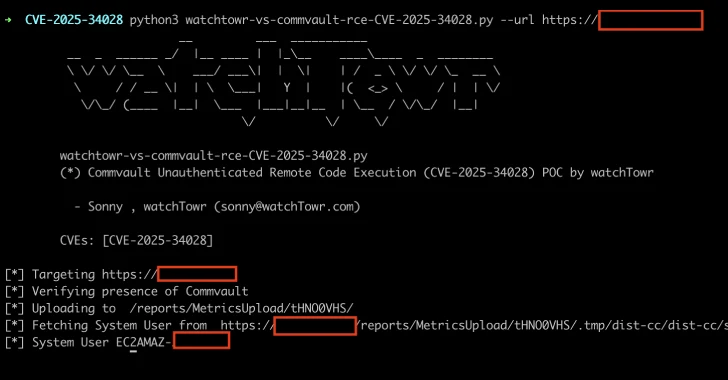
Critical Commvault Command Center Flaw Enables Attackers to Execute Code Remotely
[ad_1] Apr 24, 2025Ravie LakshmananData Breach / Vulnerability A critical security flaw has been disclosed in the Commvault Command Center that could allow arbitrary code execution on affected installations. The vulnerability, tracked as CVE-2025-34028, carries a CVSS score of 9.0 out of a maximum of 10.0. “A critical security vulnerability has been identified in the…
159 CVEs Exploited in Q1 2025 — 28.3% Within 24 Hours of Disclosure
[ad_1] Apr 24, 2025Ravie LakshmananVulnerability / Threat Intelligence As many as 159 CVE identifiers have been flagged as exploited in the wild in the first quarter of 2025, up from 151 in Q4 2024. “We continue to see vulnerabilities being exploited at a fast pace with 28.3% of vulnerabilities being exploited within 1-day of their…
Linux io_uring PoC Rootkit Bypasses System Call-Based Threat Detection Tools
[ad_1] Apr 24, 2025Ravie LakshmananEndpoint Security / Linux Cybersecurity researchers have demonstrated a proof-of-concept (PoC) rootkit dubbed Curing that leverages a Linux asynchronous I/O mechanism called io_uring to bypass traditional system call monitoring. This causes a “major blind spot in Linux runtime security tools,” ARMO said. “This mechanism allows a user application to perform various…