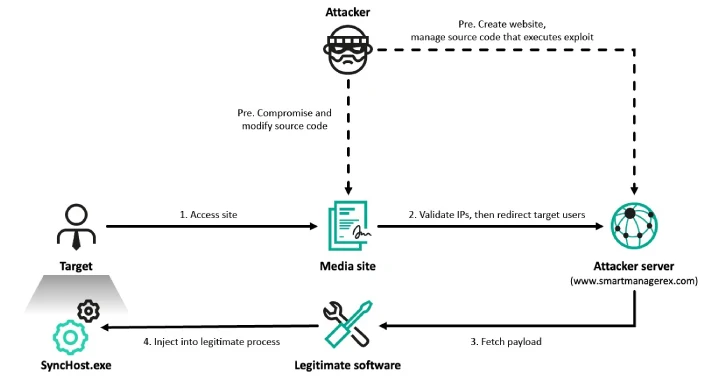
[ad_1] Apr 24, 2025Ravie LakshmananMalware / Threat Intelligence At least six organizations in South Korea have been targeted by the prolific North Korea-linked Lazarus Group as part of a campaign dubbed Operation SyncHole. The activity targeted South Korea’s software, IT, financial, semiconductor manufacturing, and telecommunications industries, according to a report from Kaspersky published today. The…
Month: April 2025
Darcula Adds GenAI to Phishing Toolkit, Lowering the Barrier for Cybercriminals
[ad_1] Apr 24, 2025Ravie LakshmananPhishing / Cybercrime The threat actors behind the Darcula phishing-as-a-service (PhaaS) platform have released new updates to their cybercrime suite with generative artificial intelligence (GenAI) capabilities. “This addition lowers the technical barrier for creating phishing pages, enabling less tech-savvy criminals to deploy customized scams in minutes,” Netcraft said in a new…
From Risk Scoring to Dynamic Policy Enforcement Without Network Redesign
[ad_1] The Evolving Healthcare Cybersecurity Landscape Healthcare organizations face unprecedented cybersecurity challenges in 2025. With operational technology (OT) environments increasingly targeted and the convergence of IT and medical systems creating an expanded attack surface, traditional security approaches are proving inadequate. According to recent statistics, the healthcare sector experienced a record-breaking year for data breaches in…
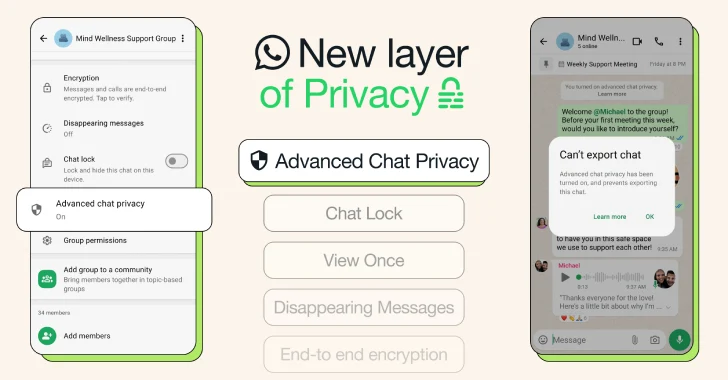
WhatsApp Adds Advanced Chat Privacy to Blocks Chat Exports and Auto-Downloads
[ad_1] Apr 24, 2025Ravie LakshmananData Protection / Artificial Intelligence WhatsApp has introduced an extra layer of privacy called Advanced Chat Privacy that allows users to block participants from sharing the contents of a conversation in traditional chats and groups. “This new setting available in both chats and groups helps prevent others from taking content outside…
DPRK Hackers Steal $137M from TRON Users in Single-Day Phishing Attack
[ad_1] Apr 23, 2025Ravie LakshmananMalware / Cryptocurrency Multiple threat activity clusters with ties to North Korea (aka Democratic People’s Republic of Korea or DPRK) have been linked to attacks targeting organizations and individuals in the Web3 and cryptocurrency space. “The focus on Web3 and cryptocurrency appears to be primarily financially motivated due to the heavy…
Russian Hackers Exploit Microsoft OAuth to Target Ukraine Allies via Signal and WhatsApp
[ad_1] Multiple suspected Russia-linked threat actors are “aggressively” targeting individuals and organizations with ties to Ukraine and human rights with an aim to gain unauthorized access to Microsoft 365 accounts since early March 2025. The highly targeted social engineering operations, per Volexity, are a shift from previously documented attacks that leveraged a technique known as…
Three Reasons Why the Browser is Best for Stopping Phishing Attacks
[ad_1] Phishing attacks remain a huge challenge for organizations in 2025. In fact, with attackers increasingly leveraging identity-based techniques over software exploits, phishing arguably poses a bigger threat than ever before. Attackers are increasingly leveraging identity-based techniques over software exploits, with phishing and stolen credentials (a byproduct of phishing) now the primary cause of breaches….
Iran-Linked Hackers Target Israel with MURKYTOUR Malware via Fake Job Campaign
[ad_1] The Iran-nexus threat actor known as UNC2428 has been observed delivering a backdoor known as MURKYTOUR as part of a job-themed social engineering campaign aimed at Israel in October 2024. Google-owned Mandiant described UNC2428 as a threat actor aligned with Iran that engages in cyber espionage-related operations. The intrusion set is said to have…
Android Spyware Disguised as Alpine Quest App Targets Russian Military Devices
[ad_1] Apr 23, 2025Ravie LakshmananSpyware / Mobile Security Cybersecurity researchers have revealed that Russian military personnel are the target of a new malicious campaign that distributes Android spyware under the guise of the Alpine Quest mapping software. “The attackers hide this trojan inside modified Alpine Quest mapping software and distribute it in various ways, including…
Ripple’s xrpl.js npm Package Backdoored to Steal Private Keys in Major Supply Chain Attack
[ad_1] Apr 23, 2025Ravie LakshmananBlockchain / Cryptocurrency The Ripple cryptocurrency npm JavaScript library named xrpl.js has been compromised by unknown threat actors as part of a software supply chain attack designed to harvest and exfiltrate users’ private keys. The malicious activity has been found to affect five different versions of the package: 4.2.1, 4.2.2, 4.2.3,…