[ad_1] Apr 23, 2025Ravie LakshmananPrivacy / Artificial Intelligence Google on Tuesday revealed that it will no longer offer a standalone prompt for third-party cookies in its Chrome browser as part of its Privacy Sandbox initiative. “We’ve made the decision to maintain our current approach to offering users third-party cookie choice in Chrome, and will not…
Month: April 2025
Docker Malware Exploits Teneo Web3 Node to Earn Crypto via Fake Heartbeat Signals
[ad_1] Apr 22, 2025Ravie LakshmananIoT Security / Malware Cybersecurity researchers have detailed a malware campaign that’s targeting Docker environments with a previously undocumented technique to mine cryptocurrency. The activity cluster, per Darktrace and Cado Security, represents a shift from other cryptojacking campaigns that directly deploy miners like XMRig to illicitly profit off the compute resources….
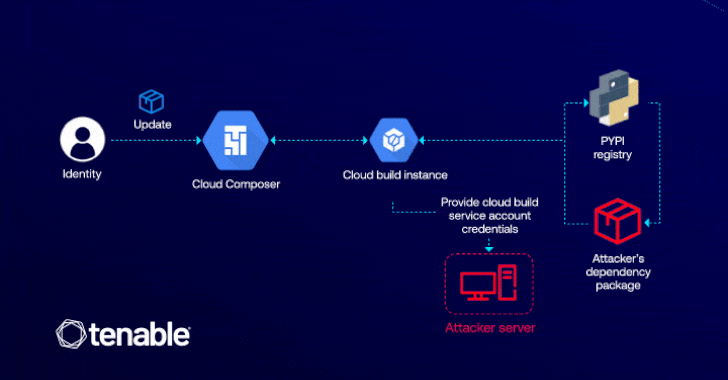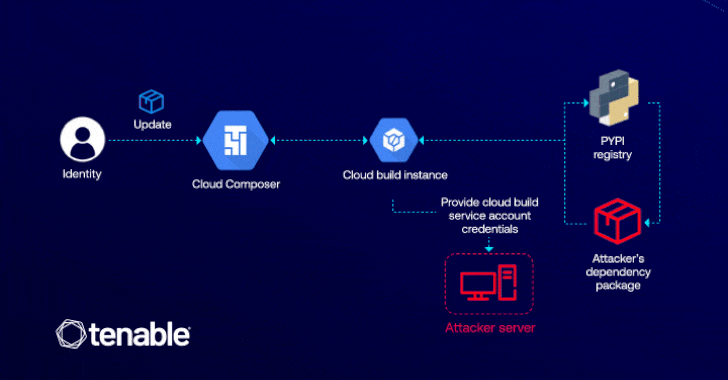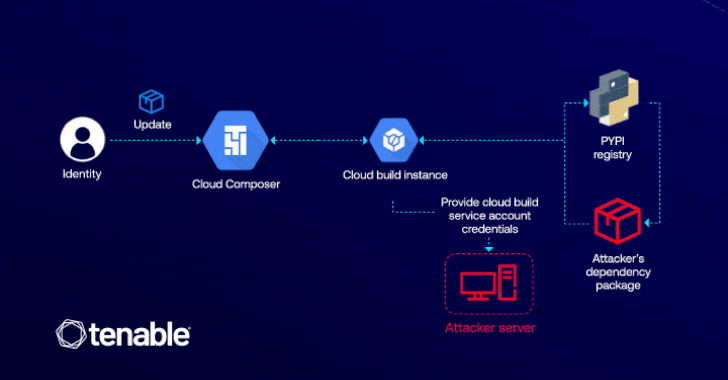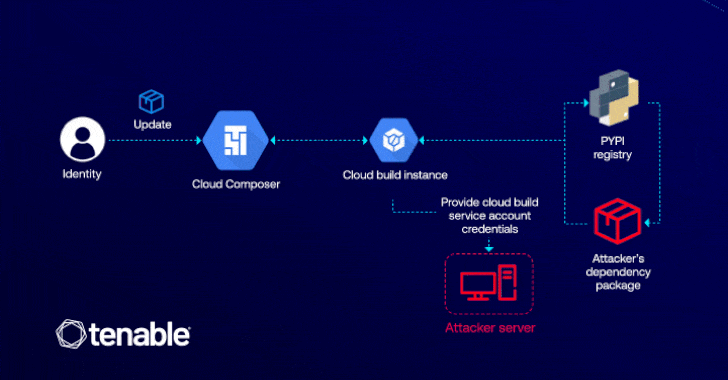
GCP Cloud Composer Bug Let Attackers Elevate Access via Malicious PyPI Packages
[ad_1] Cybersecurity researchers have detailed a now-patched vulnerability in Google Cloud Platform (GCP) that could have enabled an attacker to elevate their privileges in the Cloud Composer workflow orchestration service that’s based on Apache Airflow. “This vulnerability lets attackers with edit permissions in Cloud Composer to escalate their access to the default Cloud Build service…
Phishers Exploit Google Sites and DKIM Replay to Send Signed Emails, Steal Credentials
[ad_1] In what has been described as an “extremely sophisticated phishing attack,” threat actors have leveraged an uncommon approach that allowed bogus emails to be sent via Google’s infrastructure and redirect message recipients to fraudulent sites that harvest their credentials. “The first thing to note is that this is a valid, signed email – it…
5 Major Concerns With Employees Using The Browser
[ad_1] As SaaS and cloud-native work reshape the enterprise, the web browser has emerged as the new endpoint. However, unlike endpoints, browsers remain mostly unmonitored, despite being responsible for more than 70% of modern malware attacks. Keep Aware’s recent State of Browser Security report highlights major concerns security leaders face with employees using the web…
Microsoft Secures MSA Signing with Azure Confidential VMs Following Storm-0558 Breach
[ad_1] Apr 22, 2025Ravie LakshmananIdentity Management / Cloud Security Microsoft on Monday announced that it has moved the Microsoft Account (MSA) signing service to Azure confidential virtual machines (VMs) and that it’s also in the process of migrating the Entra ID signing service as well. The disclosure comes about seven months after the tech giant…
Lotus Panda Hacks SE Asian Governments With Browser Stealers and Sideloaded Malware
[ad_1] Apr 22, 2025Ravie LakshmananCyber Espionage / Threat Intelligence The China-linked cyber espionage group tracked as Lotus Panda has been attributed to a campaign that compromised multiple organizations in an unnamed Southeast Asian country between August 2024 and February 2025. “Targets included a government ministry, an air traffic control organization, a telecoms operator, and a…
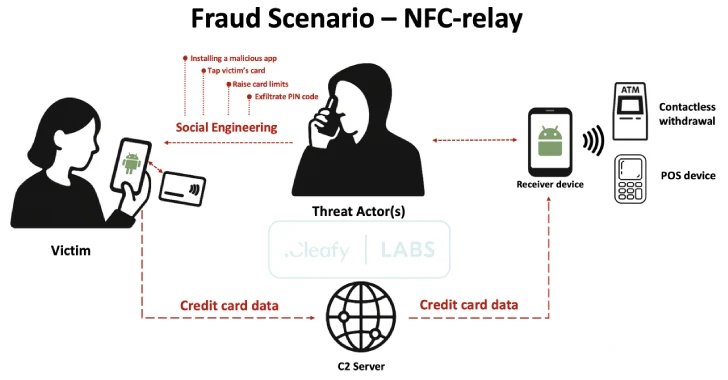
SuperCard X Android Malware Enables Contactless ATM and PoS Fraud via NFC Relay Attacks
[ad_1] Apr 21, 2025Ravie LakshmananTechnology / Mobile Security A new Android malware-as-a-service (MaaS) platform named SuperCard X can facilitate near-field communication (NFC) relay attacks, enabling cybercriminals to conduct fraudulent cashouts. The active campaign is targeting customers of banking institutions and card issuers in Italy with an aim to compromise payment card data, fraud prevention firm…
Kimsuky Exploits BlueKeep RDP Vulnerability to Breach Systems in South Korea and Japan
[ad_1] Apr 21, 2025Ravie LakshmananMalware / Vulnerability Cybersecurity researchers have flagged a new malicious campaign related to the North Korean state-sponsored threat actor known as Kimsuky that exploits a now-patched vulnerability impacting Microsoft Remote Desktop Services to gain initial access. The activity has been named Larva-24005 by the AhnLab Security Intelligence Center (ASEC). “In some…
iOS Zero-Days, 4Chan Breach, NTLM Exploits, WhatsApp Spyware & More
[ad_1] Apr 21, 2025Ravie LakshmananCybersecurity / Hacking News Can a harmless click really lead to a full-blown cyberattack? Surprisingly, yes — and that’s exactly what we saw in last week’s activity. Hackers are getting better at hiding inside everyday actions: opening a file, running a project, or logging in like normal. No loud alerts. No…