[ad_1] Introduction Cyber threats targeting supply chains have become a growing concern for businesses across industries. As companies continue to expand their reliance on third-party vendors, cloud-based services, and global logistics networks, cybercriminals are exploiting vulnerabilities within these interconnected systems to launch attacks. By first infiltrating a third-party vendor with undetected security gaps, attackers can…
Month: April 2025
Experts Uncover Four New Privilege Escalation Flaws in Windows Task Scheduler
[ad_1] Apr 16, 2025Ravie LakshmananEndpoint Security / Vulnerability Cybersecurity researchers have detailed four different vulnerabilities in a core component of the Windows task scheduling service that could be exploited by local attackers to achieve privilege escalation and erase logs to cover up evidence of malicious activities. The issues have been uncovered in a binary named…
Google Blocked 5.1B Harmful Ads and Suspended 39.2M Advertiser Accounts in 2024
[ad_1] Apr 16, 2025Ravie LakshmananArtificial Intelligence / Malvertising Google on Wednesday revealed that it suspended over 39.2 million advertiser accounts in 2024, with a majority of them identified and blocked by its systems before it could serve harmful ads to users. In all, the tech giant said it stopped 5.1 billion bad ads, restricted 9.1…
Gamma AI Platform Abused in Phishing Chain to Spoof Microsoft SharePoint Logins
[ad_1] Threat actors are leveraging an artificial intelligence (AI) powered presentation platform named Gamma in phishing attacks to direct unsuspecting users to spoofed Microsoft login pages. “Attackers weaponize Gamma, a relatively new AI-based presentation tool, to deliver a link to a fraudulent Microsoft SharePoint login portal,” Abnormal Security researchers Hinman Baron and Piotr Wojtyla said…
Chinese Android Phones Shipped with Fake WhatsApp, Telegram Apps Targeting Crypto Users
[ad_1] Cheap Android smartphones manufactured by Chinese companies have been observed pre-installed with trojanized apps masquerading as WhatsApp and Telegram that contain cryptocurrency clipper functionality as part of a campaign since June 2024. While using malware-laced apps to steal financial information is not a new phenomenon, the new findings from Russian antivirus vendor Doctor Web…
U.S. Govt. Funding for MITRE’s CVE Ends April 16, Cybersecurity Community on Alert
[ad_1] Apr 16, 2025Ravie LakshmananVulnerability Management / Incident Response The U.S. government funding for non-profit research giant MITRE to operate and maintain its Common Vulnerabilities and Exposures (CVE) program will expire Wednesday, an unprecedented development that could shake up one of the foundational pillars of the global cybersecurity ecosystem. The 25-year-old CVE program is a…
Malicious PyPI Package Targets MEXC Trading API to Steal Credentials and Redirect Orders
[ad_1] Apr 15, 2025Ravie LakshmananSupply Chain Attack / Malware Cybersecurity researchers have disclosed a malicious package uploaded to the Python Package Index (PyPI) repository that’s designed to reroute trading orders placed on the MEXC cryptocurrency exchange to a malicious server and steal tokens. The package, ccxt-mexc-futures, purports to be an extension built on top of…
Critical Apache Roller Vulnerability (CVSS 10.0) Enables Unauthorized Session Persistence
[ad_1] Apr 15, 2025Ravie LakshmananVulnerability / Software Security A critical security vulnerability has been disclosed in the Apache Roller open-source, Java-based blogging server software that could allow malicious actors to retain unauthorized access even after a password change. The flaw, assigned the CVE identifier CVE-2025-24859, carries a CVSS score of 10.0, indicating maximum severity. It…
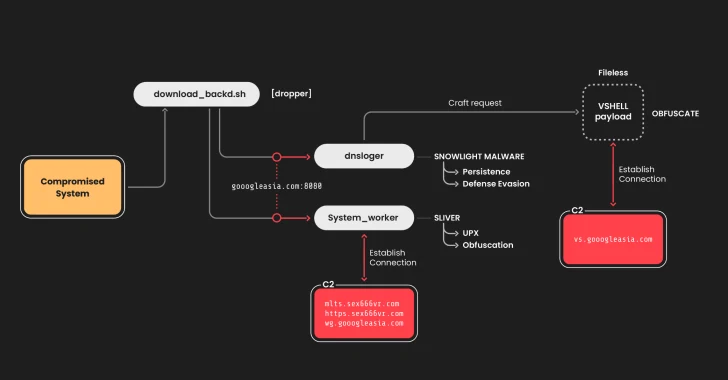
Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool
[ad_1] Apr 15, 2025Ravie LakshmananLinux / Malware The China-linked threat actor known as UNC5174 has been attributed to a new campaign that leverages a variant of a known malware dubbed SNOWLIGHT and a new open-source tool called VShell to infect Linux systems. “Threat actors are increasingly using open source tools in their arsenals for cost-effectiveness…
Majority of Browser Extensions Can Access Sensitive Enterprise Data, New Report Finds
[ad_1] Apr 15, 2025The Hacker NewsData Privacy / Enterprise Security Everybody knows browser extensions are embedded into nearly every user’s daily workflow, from spell checkers to GenAI tools. What most IT and security people don’t know is that browser extensions’ excessive permissions are a growing risk to organizations. LayerX today announced the release of the…