[ad_1] The North Korea-linked threat actor assessed to be behind the massive Bybit hack in February 2025 has been linked to a malicious campaign that targets developers to deliver new stealer malware under the guise of a coding assignment. The activity has been attributed by Palo Alto Networks Unit 42 to a hacking group it…
Month: April 2025
Meta Resumes E.U. AI Training Using Public User Data After Regulator Approval
[ad_1] Apr 15, 2025Ravie LakshmananArtificial Intelligence / Data Privacy Meta has announced that it will begin to train its artificial intelligence (AI) models using public data shared by adults across its platforms in the European Union, nearly a year after it paused its efforts due to data protection concerns from Irish regulators. “This training will…
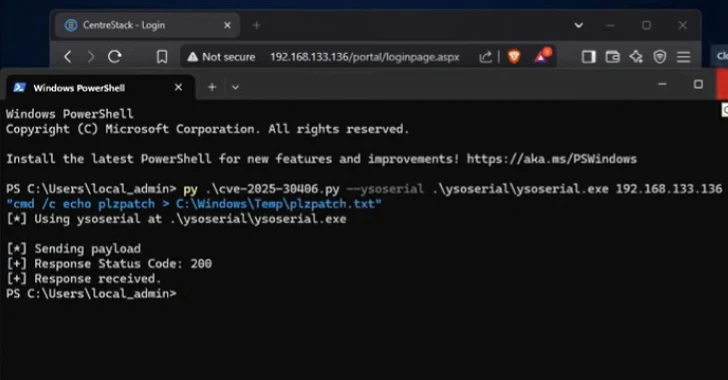
Gladinet’s Triofox and CentreStack Under Active Exploitation via Critical RCE Vulnerability
[ad_1] Apr 15, 2025Ravie LakshmananVulnerability / Endpoint Security A recently disclosed security flaw in Gladinet CentreStack also impacts its Triofox remote access and collaboration solution, according to Huntress, with seven different organizations compromised to date. Tracked as CVE-2025-30406 (CVSS score: 9.0), the vulnerability refers to the use of a hard-coded cryptographic key that could expose…
ResolverRAT Campaign Targets Healthcare, Pharma via Phishing and DLL Side-Loading
[ad_1] Cybersecurity researchers have discovered a new, sophisticated remote access trojan called ResolverRAT that has been observed in attacks targeting healthcare and pharmaceutical sectors. “The threat actor leverages fear-based lures delivered via phishing emails, designed to pressure recipients into clicking a malicious link,” Morphisec Labs researcher Nadav Lorber said in a report shared with The…
Phishing Campaigns Use Real-Time Checks to Validate Victim Emails Before Credential Theft
[ad_1] Apr 14, 2025Ravie LakshmananEmail Security / Cyber Attack Cybersecurity researchers are calling attention to a new type of credential phishing scheme that ensures that the stolen information is associated with valid online accounts. The technique has been codenamed precision-validating phishing by Cofense, which it said employs real-time email validation so that only a select…
Windows 0-Day, VPN Exploits, Weaponized AI, Hijacked Antivirus and More
[ad_1] Apr 14, 2025Ravie LakshmananThreat Intelligence / Cybersecurity Attackers aren’t waiting for patches anymore — they are breaking in before defenses are ready. Trusted security tools are being hijacked to deliver malware. Even after a breach is detected and patched, some attackers stay hidden. This week’s events show a hard truth: it’s not enough to…
Evolve Faster Than the Threats or Get Left Behind
[ad_1] Apr 14, 2025The Hacker NewsCybersecurity / Security Training AI is changing cybersecurity faster than many defenders realize. Attackers are already using AI to automate reconnaissance, generate sophisticated phishing lures, and exploit vulnerabilities before security teams can react. Meanwhile, defenders are overwhelmed by massive amounts of data and alerts, struggling to process information quickly enough…
Pakistan-Linked Hackers Expand Targets in India with CurlBack RAT and Spark RAT
[ad_1] Apr 14, 2025Ravie LakshmananCyber Attack / Malware A threat actor with ties to Pakistan has been observed targeting various sectors in India with various remote access trojans like Xeno RAT, Spark RAT, and a previously undocumented malware family called CurlBack RAT. The activity, detected by SEQRITE in December 2024, targeted Indian entities under railway,…
Fortinet Warns Attackers Retain FortiGate Access Post-Patching via SSL-VPN Symlink Exploit
[ad_1] Apr 11, 2025Ravie LakshmananNetwork Security / Vulnerability Fortinet has revealed that threat actors have found a way to maintain read-only access to vulnerable FortiGate devices even after the initial access vector used to breach the devices was patched. The attackers are believed to have leveraged known and now-patched security flaws, including, but not limited…
SpyNote, BadBazaar, MOONSHINE Malware Target Android and iOS Users via Fake Apps
[ad_1] Cybersecurity researchers have found that threat actors are setting up deceptive websites hosted on newly registered domains to deliver a known Android malware called SpyNote. These bogus websites masquerade as Google Play Store install pages for apps like the Chrome web browser, indicating an attempt to deceive unsuspecting users into installing the malware instead….