[ad_1] May 02, 2025Ravie LakshmananPassword Security / Windows A year after Microsoft announced passkeys support for consumer accounts, the tech giant has announced a big change that pushes individuals signing up for new accounts to use the phishing-resistant authentication method by default. “Brand new Microsoft accounts will now be ‘passwordless by default,’” Microsoft’s Joy Chik…
Month: May 2025
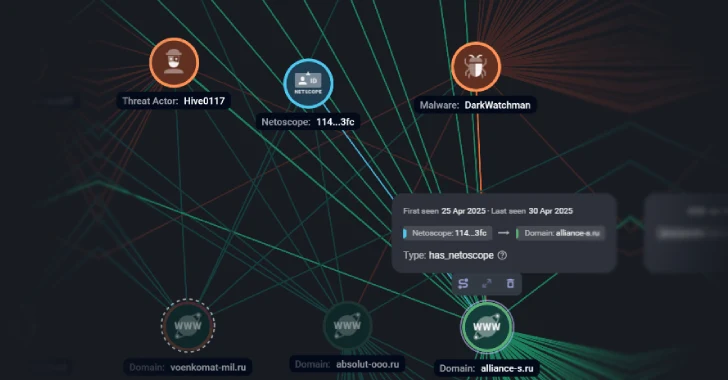
DarkWatchman, Sheriff Malware Hit Russia and Ukraine with Stealth and Nation-Grade Tactics
[ad_1] Russian companies have been targeted as part of a large-scale phishing campaign that’s designed to deliver a known malware called DarkWatchman. Targets of the attacks include entities in the media, tourism, finance and insurance, manufacturing, retail, energy, telecom, transport, and biotechnology sectors, Russian cybersecurity company F6 said. The activity is assessed to be the…
Fake Security Plugin on WordPress Enables Remote Admin Access for Attackers
[ad_1] May 01, 2025Ravie LakshmananMalware / Web Skimming Cybersecurity researchers have shed light on a new campaign targeting WordPress sites that disguises the malware as a security plugin. The plugin, which goes by the name “WP-antymalwary-bot.php,” comes with a variety of features to maintain access, hide itself from the admin dashboard, and execute remote code….
Claude AI Exploited to Operate 100+ Fake Political Personas in Global Influence Campaign
[ad_1] May 01, 2025Ravie LakshmananArtificial Intelligence / Disinformation Artificial intelligence (AI) company Anthropic has revealed that unknown threat actors leveraged its Claude chatbot for an “influence-as-a-service” operation to engage with authentic accounts across Facebook and X. The sophisticated activity, branded as financially-motivated, is said to have used its AI tool to orchestrate 100 distinct persons…
Why top SOC teams are shifting to Network Detection and Response
[ad_1] Security Operations Center (SOC) teams are facing a fundamentally new challenge — traditional cybersecurity tools are failing to detect advanced adversaries who have become experts at evading endpoint-based defenses and signature-based detection systems. The reality of these “invisible intruders” is driving a significant need for a multi-layered approach to detecting threats, including Network Detection…
95% of AppSec Fixes Don’t Reduce Risk
[ad_1] For over a decade, application security teams have faced a brutal irony: the more advanced the detection tools became, the less useful their results proved to be. As alerts from static analysis tools, scanners, and CVE databases surged, the promise of better security grew more distant. In its place, a new reality took hold—one…
Commvault Confirms Hackers Exploited CVE-2025-3928 as Zero-Day in Azure Breach
[ad_1] May 01, 2025Ravie LakshmananZero-Day / Threat Intelligence Enterprise data backup platform Commvault has revealed that an unknown nation-state threat actor breached its Microsoft Azure environment by exploiting CVE-2025-3928 but emphasized there is no evidence of unauthorized data access. “This activity has affected a small number of customers we have in common with Microsoft, and…
SonicWall Confirms Active Exploitation of Flaws Affecting Multiple Appliance Models
[ad_1] May 01, 2025Ravie LakshmananVulnerability / VPN Security SonicWall has revealed that two now-patched security flaws impacting its SMA100 Secure Mobile Access (SMA) appliances have been exploited in the wild. The vulnerabilities in question are listed below – CVE-2023-44221 (CVSS score: 7.2) – Improper neutralization of special elements in the SMA100 SSL-VPN management interface allows…