[ad_1]
Amazon Web Services (AWS), Cloudflare, and Google on Tuesday said they took steps to mitigate record-breaking distributed denial-of-service (DDoS) attacks that relied on a novel technique called HTTP/2 Rapid Reset.
The layer 7 attacks were detected in late August 2023, the companies said in a coordinated disclosure. The cumulative susceptibility to this attack is being tracked as CVE-2023-44487, and carries a CVSS score of 7.5 out of a maximum of 10.
While the attacks aimed at Google’s cloud infrastructure peaked at 398 million requests per second (RPS), the ones aimed at AWS and Cloudflare exceeded a volume of 155 million and 201 million requests per second (RPS), respectively.
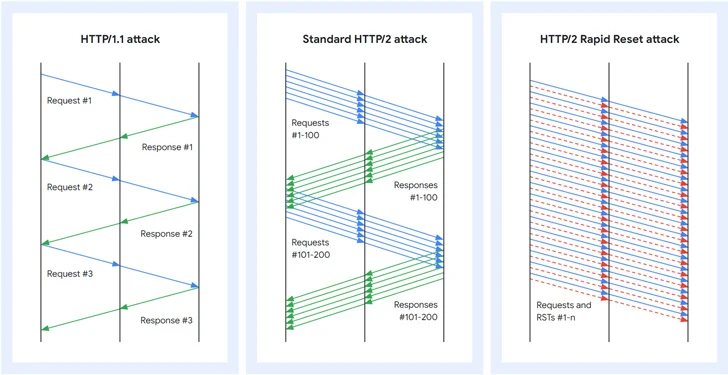
HTTP/2 Rapid Reset refers to a zero-day flaw in the HTTP/2 protocol that can be exploited to carry out DDoS attacks. A significant feature of HTTP/2 is multiplexing requests over a single TCP connection, which manifests in the form of concurrent streams.
What’s more, a client that wants to abort a request can issue a RST_STREAM frame to halt the data exchange. The Rapid Reset attack leverages this method to send and cancel requests in quick succession, thereby circumventing the server’s concurrent stream maximum and overloading the server without reaching its configured threshold.
“HTTP/2 rapid reset attacks consist of multiple HTTP/2 connections with requests and resets in rapid succession,” Mark Ryland and Tom Scholl at AWS said.
“For example, a series of requests for multiple streams will be transmitted followed up by a reset for each of those requests. The targeted system will parse and act upon each request, generating logs for a request that is then reset, or canceled, by a client.”
This ability to reset streams immediately allows each connection to have an indefinite number of requests in flight, thereby enabling a threat actor to issue a barrage of HTTP/2 requests that can overwhelm a targeted website’s capability to respond to new incoming requests, effectively taking it down.
Put differently, by initiating hundreds of thousands of HTTP/2 streams and rapidly canceling them at scale over an established connection, threat actors can overwhelm websites and knock them offline. Another crucial aspect is that such attacks can be pulled off using a modestly-sized botnet, something to tune of 20,000 machines as observed by Cloudflare.
“This zero-day provided threat actors with a critical new tool in their Swiss Army knife of vulnerabilities to exploit and attack their victims at a magnitude that has never been seen before,” Grant Bourzikas, chief security officer at Cloudflare, said.
HTTP/2 is used by 35.6% of all the websites, according to W3Techs. The percentage of requests that use HTTP/2 is at 77%, per data shared by Web Almanac.
Google Cloud said it has observed multiple variants of the Rapid Reset attacks that while not as effective as the initial version, are more efficient than the standard HTTP/2 DDoS attacks.
“The first variant does not immediately cancel the streams, but instead opens a batch of streams at once, waits for some time, and then cancels those streams and then immediately opens another large batch of new streams,” Juho Snellman and Daniele Lamartino said.
“The second variant does away with canceling streams entirely, and instead optimistically tries to open more concurrent streams than the server advertised.”
F5, in an independent advisory of its own, said the attack impacts the NGINX HTTP/2 module and has urged its customers to update their NGINX configuration to limit the number of concurrent streams to a default of 128 and persist HTTP connections for up to 1000 requests.
“After today, threat actors will be largely aware of the HTTP/2 vulnerability; and it will inevitably become trivial to exploit and kickoff the race between defenders and attacks — first to patch vs. first to exploit,” Bourzikas further said. “Organizations should assume that systems will be tested, and take proactive measures to ensure protection.”
[ad_2]