[ad_1] Nov 09, 2023NewsroomVulnerability / Zero Day The threat actor known as Lace Tempest has been linked to the exploitation of a zero-day flaw in SysAid IT support software in limited attacks, according to new findings from Microsoft. Lace Tempest, which is known for distributing the Cl0p ransomware, has in the past leveraged zero-day flaws…
Month: November 2023
New Malvertising Campaign Uses Fake Windows News Portal to Distribute Malicious Installers
[ad_1] Nov 09, 2023NewsroomEndpoint Security / Malware A new malvertising campaign has been found to employ fake sites that masquerade as legitimate Windows news portal to propagate a malicious installer for a popular system profiling tool called CPU-Z. “This incident is a part of a larger malvertising campaign that targets other utilities like Notepad++, Citrix,…
High-Severity SLP Vulnerability Now Under Active Exploitation
[ad_1] Nov 09, 2023NewsroomCyber Attack / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a high-severity flaw in the Service Location Protocol (SLP) to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. Tracked as CVE-2023-29552 (CVSS score: 7.5), the issue relates to a denial-of-service (DoS) vulnerability that could…
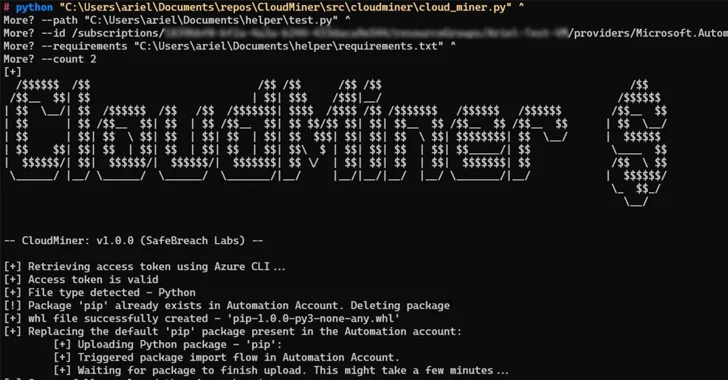
Researchers Uncover Undetectable Crypto Mining Technique on Azure Automation
[ad_1] Nov 08, 2023NewsroomCloud Security / Cryptocurrency Cybersecurity researchers have developed what’s the first fully undetectable cloud-based cryptocurrency miner leveraging the Microsoft Azure Automation service without racking up any charges. Cybersecurity company SafeBreach said it discovered three different methods to run the miner, including one that can be executed on a victim’s environment without attracting…
BlazeStealer Malware Discovered in Python Packages on PyPI
[ad_1] Nov 08, 2023NewsroomSupply Chain / Software Security A new set of malicious Python packages has slithered their way to the Python Package Index (PyPI) repository with the ultimate aim of stealing sensitive information from compromised developer systems. The packages masquerade as seemingly innocuous obfuscation tools, but harbor a piece of malware called BlazeStealer, Checkmarx…
Confidence in File Upload Security is Alarmingly Low. Why?
[ad_1] Nov 07, 2023The Hacker NewsWeb Security / Cyber Threat Numerous industries—including technology, financial services, energy, healthcare, and government—are rushing to incorporate cloud-based and containerized web applications. The benefits are undeniable; however, this shift presents new security challenges. OPSWAT’s 2023 Web Application Security report reveals: 75% of organizations have modernized their infrastructure this year. 78%…
N. Korea’s BlueNoroff Blamed for Hacking macOS Machines with ObjCShellz Malware
[ad_1] Nov 07, 2023NewsroomEndpoint Security / Malware The North Korea-linked nation-state group called BlueNoroff has been attributed to a previously undocumented macOS malware strain dubbed ObjCShellz. Jamf Threat Labs, which disclosed details of the malware, said it’s used as part of the RustBucket malware campaign, which came to light earlier this year. “Based on previous…
New GootLoader Malware Variant Evades Detection and Spreads Rapidly
[ad_1] Nov 07, 2023NewsroomEndpoint Security / Malware A new variant of the GootLoader malware called GootBot has been found to facilitate lateral movement on compromised systems and evade detection. “The GootLoader group’s introduction of their own custom bot into the late stages of their attack chain is an attempt to avoid detections when using off-the-shelf…
Critical Flaws Discovered in Veeam ONE IT Monitoring Software – Patch Now
[ad_1] Nov 07, 2023NewsroomNetwork Security / Vulnerability Veeam has released security updates to address four flaws in its ONE IT monitoring and analytics platform, two of which are rated critical in severity. The list of vulnerabilities is as follows – CVE-2023-38547 (CVSS score: 9.9) – An unspecified flaw that can be leveraged by an unauthenticated…
New Jupyter Infostealer Version Emerges with Sophisticated Stealth Tactics
[ad_1] Nov 06, 2023NewsroomData Security / Malvertising An updated version of an information stealer malware known as Jupyter has resurfaced with “simple yet impactful changes” that aim to stealthily establish a persistent foothold on compromised systems. “The team has discovered new waves of Jupyter Infostealer attacks which leverage PowerShell command modifications and signatures of private…